- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.3 and Active Directory Probe
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2018 02:24 PM
I think this bug is hitting our ISE and we are not able to use AD-Join-Host-Point as one of authentication for host.
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvf55996
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2018 11:12 AM
Attribute:AD-Last-Fetch-Time value:1540480480951
...
Attribute:User-Fetch-CountryName value:
Attribute:User-Fetch-Department value:
Attribute:User-Fetch-Email value:
Attribute:User-Fetch-First-Name value:
Attribute:User-Fetch-Job-Title value:
Attribute:User-Fetch-Last-Name value:
Attribute:User-Fetch-LocalityName value:
Attribute:User-Fetch-Organizational-Unit value:
Attribute:User-Fetch-StateOrProvinceName value:
Attribute:User-Fetch-StreetAddress value:
Attribute:User-Fetch-Telephone value:
Attribute:User-Fetch-User-Name value:<omitted>
This is pretty much CSCve03360. The User-Fetch-* attributes are fetched by the AD probe for the user visibility data and updated AD-Last-Fetch-Time so the AD probe won't fetch for the computer data for another 24 hours. I do not know any reliable workaround until getting the fix for the bug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2018 12:41 PM - edited 10-20-2018 12:44 PM
This is a mis-interpretation.
AD-Join-Point (without "-Host-") is the one collected by ISE profiler's AD probe. And, AD-Host-Join-Point (with "-Host-") is collected by ISE profiler's RADIUS probe. As a result, it's not currently available in the dictionary ACTIVEDIRECTORY_PROBE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 06:26 AM
With that being said I can't use it as a profiler condition?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 08:14 AM
With that being said I can't use it as a profiler condition?
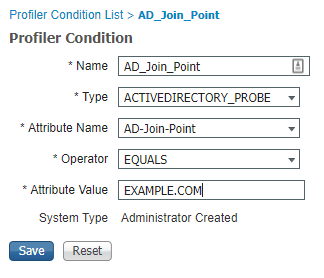
Your picture shows AD-Join-Point used as a condition for a profiler check. It would be a bug if that is not working to make a match. As said previously, the other attribute, despite with the same value most of the time, is not available for such.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 09:27 AM - edited 10-24-2018 09:28 AM
Checking EndPointSource Active Directory Probe, other attributes is AD-Host-Join-Point but on profiler condition is AD-Join-Point. The AD-Join-Point is not showing on Endpoint other attributes.
If AD-Host-Join-Point used by ISE Radius probe, how can I make ISE to perform EndPointSource Radius Probe instead of Active Directory Probe? Turning off AD probe will that make it Radius probe to take place?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 09:57 AM
No, it won't work like that. It's likely you are hitting some other bug, such as CSCve03360
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 10:05 AM
Our ISE 2.3 installed patch 2,3 I was planning on installing patch 4 and patch 5. Will that address the bug problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 10:58 AM - edited 10-24-2018 11:01 AM
When you patch ISE, you don't need to install every patch released. The most recent patch incorporates all the previous patch fixes.
ex. You can apply just patch 5 on your ISE deployment and it will include all patch 1-4 items too.
Just commentary on patching. I don't know if your issue is fixed in patch X. When I am unsure if an issue is fixed in patch X, I work with TAC, I would suggest you do the same here. It can be very difficult to troubleshoot/identify fridge issues via forum posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 04:41 PM
I concurred with Damien's comment.
CSCve03360 is due to ISE 2.2+ using AD probe to fetch both computer info and user info and two types of fetches using the same AD-Last-Fetch-Time such that computer info fetch not occurring if user info fetched within the last 24 hour or the configured interval. The bug is addressed in ISE 2.4 FCS. CSCvm72309 observed in ISE 2.4 Patch 1+.
Your deployment might need both bug fixes and TAC may help analyzing that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2018 08:42 AM
I turned on debug on ISE for profiler and I found out that the initial authentication method is MAB, then Radius Probe and then last Active Directory Probe.
I shutdown the interface first, deleted the endpoint on the ISE, rebooted the pc and do no shutdown on interface. For the first time when ISE sees the MAC address it will be unknown but the first sequence is MAB, then Radius Probe and then Active Directory probe.
ISE of course after I deleted the endpoint it has no longer the mac address in its database. How can I configure the ISE to perform Radius Probe or AD Probe only?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2018 09:02 AM - edited 10-25-2018 09:03 AM
Radius Probe
Attribute:AAA-Server value:<omitted>
Attribute:AD-Error-Details value:Domain trust is one-way
Attribute:AD-Groups-Names value:<omitted>/Builtin/Domain Computers
Attribute:AD-Host-Candidate-Identities value:<omitted>
Attribute:AD-Host-DNS-Domain value:<omitted>
Attribute:AD-Host-Join-Point value:EXAMPLE.ORG
Attribute:AD-Host-NetBios-Name value:EXAMPLE
Attribute:AD-Host-Resolved-DNs value:<omitted>
Attribute:AD-Host-Resolved-Identities <omitted>
Attribute:AD-Last-Fetch-Time value:1540480415942
Attribute:AKI value:<omitted>
Attribute:AuthenticationIdentityStore value:EXAMPLE
Attribute:AuthenticationMethod value:x509_PKI
Attribute:AuthenticationStatus value:AuthenticationPassed
Attribute:AuthorizationPolicyMatchedRule value:AD OU Computers Root CA
Attribute:BYODRegistration value:Unknown
Attribute:CacheUpdateTime value:1540480415962
Attribute:Called-Station-ID value:<omitted>
Attribute:Calling-Station-ID value:<omitted>
Attribute:CreateTime value:1540480406501
Attribute:DTLSSupport value:Unknown
Attribute:Days to Expiry value:3393
Attribute:DestinationIPAddress value:<omitted>
Attribute:DestinationPort value:1812
Attribute:Device IP Address value:<omitted>
Attribute:Device Identifier value:
Attribute:Device Port value:1645
Attribute:Device Type value:<omitted>
Attribute:DeviceRegistrationStatus value:NotRegistered
Attribute:EndPointMACAddress value:<omitted>
Attribute:EndPointPolicy value:Dell-Inc-Device
Attribute:EndPointPolicyID value:<omitted>
Attribute:EndPointProfilerServer value:<omitted>
Attribute:EndPointSource value:RADIUS Probe
On the Profiling Condition , selecting Radius as Type, searching for AD-Host-Join-Point name is not available. I can't build these attributes and use it for matching endpoint that are part of Active Directory.
Here is the AD Probe
MAC: <omitted>
Attribute:AD-Last-Fetch-Time value:1540480480951
Attribute:BYODRegistration value:Unknown
Attribute:DeviceRegistrationStatus value:NotRegistered
Attribute:EndPointProfilerServer value:<omitted>
Attribute:EndPointSource value:Active Directory Probe
Attribute:MACAddress value:<omitted>
Attribute:NmapSubnetScanID value:0
Attribute:OUI value:Dell Inc.
Attribute:PolicyVersion value:0
Attribute:PortalUser value:
Attribute:PostureApplicable value:Yes
Attribute:User-Fetch-CountryName value:
Attribute:User-Fetch-Department value:
Attribute:User-Fetch-Email value:
Attribute:User-Fetch-First-Name value:
Attribute:User-Fetch-Job-Title value:
Attribute:User-Fetch-Last-Name value:
Attribute:User-Fetch-LocalityName value:
Attribute:User-Fetch-Organizational-Unit value:
Attribute:User-Fetch-StateOrProvinceName value:
Attribute:User-Fetch-StreetAddress value:
Attribute:User-Fetch-Telephone value:
Attribute:User-Fetch-User-Name value:<omitted>
Attribute:SkipProfiling value:false
The attribute for AD-Join-Point is not even showing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2018 09:40 AM
Please check if this post could help you
https://community.cisco.com/t5/policy-and-access/ise-2-3-and-active-directory-probe/td-p/3351475
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2018 11:12 AM
Attribute:AD-Last-Fetch-Time value:1540480480951
...
Attribute:User-Fetch-CountryName value:
Attribute:User-Fetch-Department value:
Attribute:User-Fetch-Email value:
Attribute:User-Fetch-First-Name value:
Attribute:User-Fetch-Job-Title value:
Attribute:User-Fetch-Last-Name value:
Attribute:User-Fetch-LocalityName value:
Attribute:User-Fetch-Organizational-Unit value:
Attribute:User-Fetch-StateOrProvinceName value:
Attribute:User-Fetch-StreetAddress value:
Attribute:User-Fetch-Telephone value:
Attribute:User-Fetch-User-Name value:<omitted>
This is pretty much CSCve03360. The User-Fetch-* attributes are fetched by the AD probe for the user visibility data and updated AD-Last-Fetch-Time so the AD probe won't fetch for the computer data for another 24 hours. I do not know any reliable workaround until getting the fix for the bug.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide