- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.4 always using OCSP cache during certificate status check
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2020 02:17 AM
I’m currently running ISE 2.4 patch 10 and using OCSP in combination with ISE in order to check the certificate status before a user is granted access to the network.
So when the certificate is revoked, the user shouldn't be able to login via it's certificate.
The issue I'm having is that when a certificate is revoked and a client sets up a new connection to the network, the ISE keeps checking its cache in order to verify the certificate instead of polling the PKI server.
When I manually clear the cache on the ISE and a user tries to login, the ISE directly checks the PKI server for its validity.
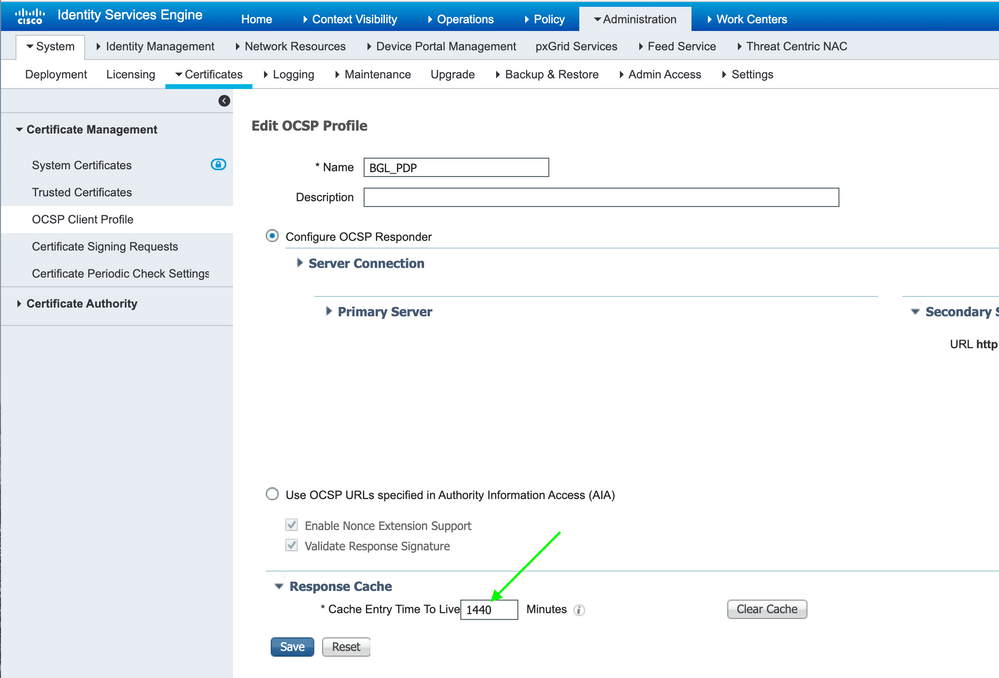
I have tried setting the Cache Entry Time To Live under the Response Cache settings to 1 minute and since that didn't work to 0 minutes, but even with 0 minutes its keeps checking in its cache.
Example with the Cache Entry TTL set to 0 minutes.
When a new connection is made from an existing user:
12568 Lookup user certificate status in OCSP cache - certificate for *Laptop*
12570 Lookup user certificate status in OCSP cache succeeded - certificate for *Laptop*
12554 OCSP status of user certificate is good - certificate for *Laptop*
When the cache is manually cleared, and the user reconnects and only then the ISE will check its PKI server.
12568 Lookup user certificate status in OCSP cache - certificate for *Laptop*
12569 User certificate status was not found in OCSP cache - certificate for *Laptop*
12988 Take OCSP servers list from OCSP service configuration - certificate for *Laptop*
12550 Sent an OCSP request to the primary OCSP server for the CA - External OCSP Server
12553 Received OCSP response - certificate for *Laptop*
12554 OCSP status of user certificate is good - certificate for *Laptop*
Is there anyone who has encountered this issue before or has an idea how to get the ISE to always check the PKI servers instead of its cache without manually clearing it?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2020 06:19 PM
Besides what Mike.Cifelli said, An OCSP profile has a configurable TTL:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2020 05:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2020 06:19 PM
Besides what Mike.Cifelli said, An OCSP profile has a configurable TTL:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2020 02:46 AM
Hi hslai,
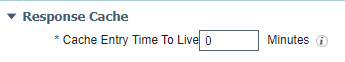
Thank you for your response. This is the setting that should work for us. We already have this configured to the value "0" which means that ISE should not cache the OCSP response according to Cisco documentation:
"Enter the time in minutes after which the cache entry expires.
Each response from the OCSP server holds a nextUpdate value. This value shows when the status of the certificate will be updated next on the server. When the OCSP response is cached, the two values (one from the configuration and another from response) are compared, and the response is cached for the period of time that is the lowest value of these two. If the nextUpdate value is 0, the response is not cached at all.
Cisco ISE will cache OCSP responses for the configured time. The cache is not replicated or persistent, so when Cisco ISE restarts, the cache is cleared.
The OCSP cache is used in order to maintain the OCSP responses and for the following reasons:
To reduce network traffic and load from the OCSP servers on an already-known certificate
To increase the performance of Cisco ISE by caching already-known certificate statuses
By default, the cache is set to 2 minutes for the internal CA OCSP client profile. If an endpoint authenticates a second time within 2 minutes of the first authentication, the OCSP cache is used and the OCSP responder is not queried. If the endpoint certificate has been revoked within the cache period, the previous OCSP status of Good will be used and the authentication succeeds. Setting the cache to 0 minutes prevents any responses from being cached. This option improves security, but decreases authentication performance."
Unfortunately ISE still uses OCSP cache after setting the value to 0:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2020 04:11 PM
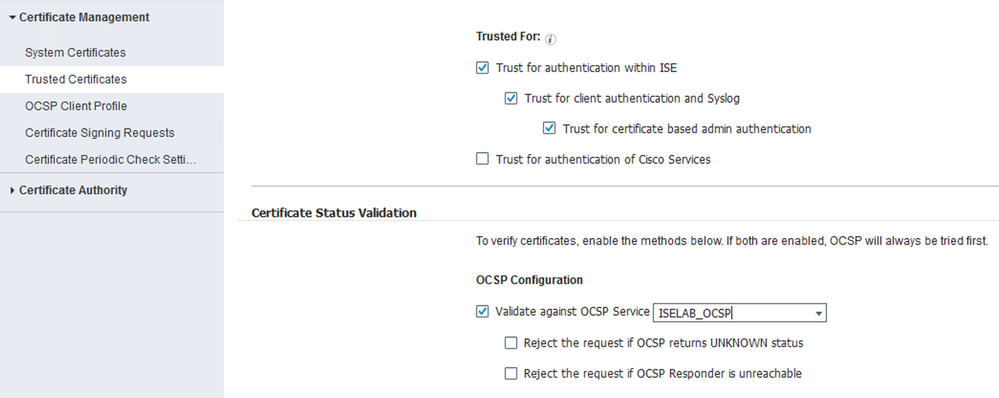
Have you confirmed that the OCSP Responder is configured for your Trusted Root CA cert?
Cheers,
Greg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2020 05:37 PM
I would also suggest you to verify on the PKI server side itself. I used the OCSP service on Microsoft CA a while ago and it took a while to show a certificate as revoked.
Perhaps, you may use some other means to block the devices; e.g. putting them in a black-list group.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2020 11:44 AM
Hi
If you set to 1 minute , isn't it honoring it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2020 05:47 PM
A defect has been filed for this issue few days ago which is yet to be fixed:
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvu02001
Till the time the workaround is to manually clear the cache.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2020 02:19 PM
This works properly in 2.4 P12
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide