- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.6 DST Root CA X3 Certificate Authority expires September 2021
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 09:33 AM
Hello,
On ISE deployment version 2.6 we have a trusted certificate named DST Root CA X3 Certificate Authority that expires in September 2021.
This certificate is included with ISE (not installed by us) and according to this documentation its purpose is "This certificate can serve as the root CA certificate for the CA chain used by cisco.com." which seems pretty important.
Do we know if this certificate expiration will break things ?
I can't find any information about this specific certificate, did cisco already communicate on how customers should handle that ?
Thanks,
Have a nice day.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2021 01:00 PM
Hi Tom,
Sorry, but I think you're overreacting.
Just like Marcelo said, ISE comes preinstalled with a bunch of root CA certs. It doesn't mean it needs or uses all of them.
Regarding your note:
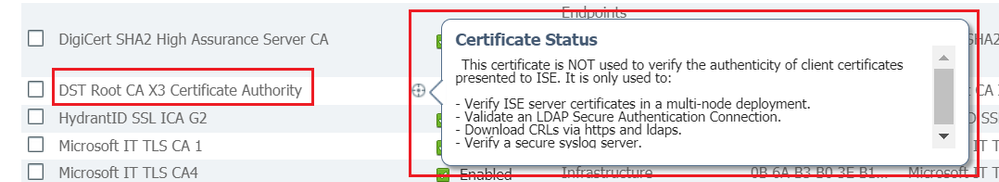
- certificate tooltip says it is used for secure ldap, secure syslog, and internal trust between ISE nodes. We need this certificate. We can't just delete it.
Are you using secure LDAP? If so, you would be the one to know what root CA signed your LDAP server cert.
Secure syslog? I don't think so.
Trust between ISE nodes? That's the system cert that has the admin use case checked, that's usually signed by any internal or public CA, other than those already installed on ISE by Cisco.
Just like with the VeriSign Class 2 Secure Server CA G3 certificate that expired 1 or 2 years ago (don't remember exactly), all you have to do is wait for this one to expire, then delete it. You don't have to delete anything as of now as long as the certificate is valid.
There is nothing to be worried about.
Best regards,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2021 02:17 PM
Hi tom.barat@dimensiondata.com ,
as an example for the 3rd option "replace this cisco-provided cert with one of our own":
1st ... to install the CA's Certificate into ISE
At Administration > System > Certificate > Certificate Management > Trusted Certificates:
. Import:
The CA's Certificate
. Trusted for:
Trust for Authentication within ISE
Trust for Client Authentication and Syslog
Trust for Certificate Based Admin Authentication
Trust for Authentication of Cisco Services
2nd ... to generate CSR from ISE for signing it's Certificate from the CA
At Administration > System > Certificate > Certificate Management > Certificate Signing Requests:
. Generate Certificate Signing Requests (CSR):
Usage: Multi-Use
Node: select the Node
<please enter the other values>
. Bind Certificate
<select the Certificate Request that you generated and bind to the Signed Certificate>
Usage: Admin, EAP Authentication and Portal
3rd ... to install the CA's Certificate on your Clients. (as an example not only for ISE, but also for your Clients)
Download the CA's Certificate
Install Certificate
Store Location: Local Machine
Certificate Store: Trusted Root Certification Authorities
Hope this helps !!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2021 09:04 AM
Marcello and Octavian are both correct that this certificate is no longer by any of ISE services by default.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 10:27 AM
Hi tom.barat@dimensiondata.com ,
DST Root CA X3 is an older Root Certificate ... please take a look at: DST Root CA X3 Expiration (September 2021).
Also at: ISE Guide, 3.0, search for Default Trusted Certificates in Cisco ISE:
"... The Trusted Certificates store (Administration > System > Certificates > Trusted Certificates) in Cisco ISE includes some certificates that are available by default. These certificates are automatically imported into the store to meet security requirements. However, it is not mandatory for you to use all of them. Unless mentioned otherwise in the following table, you can use certificates of your choice instead of the ones that are already available..."
Also double check at Administration > System > Certificates > Trusted Certificates:
Hope this helps !!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 10:44 AM
Hello,
Thanks for the answer, it is helpful. I didn't notice the details button next to the cert name in ISE GUI.
Based on "Verify ISE server certificates in a multi-node deployment", the answer to my first question is Yes, this will definitely break things.
If i understand your comment correctly the answer to "How should we handle that?" is we need to replace this default certificate with one of our own because cisco won't renew this one or replace it with a new root, is that correct ?
If so, do we have documentation explaining the requirements for this certificate ?
Usually this is my go-to documentation for ISE certificate matters, but it focuses on system certificates rather than trusted certificates.
Thanks again!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 12:35 PM - edited 06-26-2021 04:20 PM
Hi tom.barat@dimensiondata.com
the How To Implement Digital Certificates in ISE is an amazing doc, the What Certificate Values Should be Used with an ISE Deployment? is the topic that you need.
Please also take a look at: Install a 3rd party CA Certificate in ISE., How to Install Wildcard Certificates and Configure Guide to Certificate Renew on ISE.
Hope this helps !!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2021 02:01 AM
Thank you for the follow-up answer but unfortunately the resources you linked are related to system certificates, which i already know how to handle.
My question is specific to trusted certificates provided by cisco.
I can't find any documentation explaining clearly how to deal specifically with these cisco-provided trusted certificates.
Have a nice day.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2021 06:21 AM
Hi tom.barat@dimensiondata.com ,
take a look at ISE 2.1 Guide, search for Trusted Certificates Store.
"...You can delete trusted certificates that you no longer need. However, you must not delete Cisco ISE internal CA Certificates. Cisco ISE internal CA Certificates can be deleted only when you replace the Cisco ISE Root Certificate Chain for the entire deployment..."
Hope this helps !!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2021 07:28 AM
Yes, i know that we can delete trusted certs we don't need. We had the case with the verisign CA cert that expired relatively recently.
The question is what to do when we do need the certificate ?
This is the situation we are in :
- certificate tooltip says it is used for secure ldap, secure syslog, and internal trust between ISE nodes. We need this certificate. We can't just delete it.
- certificate is in trusted store and provided by cisco, so we can't renew it ourselves as we would with a self-signed or PKI-signed certificate.
- We could hypothetically replace this cisco-provided cert with one of our own, but the procedure and certificate requirements are not doucmented (or at least i couldn't find the doc).
Thanks again for the follow up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2021 01:00 PM
Hi Tom,
Sorry, but I think you're overreacting.
Just like Marcelo said, ISE comes preinstalled with a bunch of root CA certs. It doesn't mean it needs or uses all of them.
Regarding your note:
- certificate tooltip says it is used for secure ldap, secure syslog, and internal trust between ISE nodes. We need this certificate. We can't just delete it.
Are you using secure LDAP? If so, you would be the one to know what root CA signed your LDAP server cert.
Secure syslog? I don't think so.
Trust between ISE nodes? That's the system cert that has the admin use case checked, that's usually signed by any internal or public CA, other than those already installed on ISE by Cisco.
Just like with the VeriSign Class 2 Secure Server CA G3 certificate that expired 1 or 2 years ago (don't remember exactly), all you have to do is wait for this one to expire, then delete it. You don't have to delete anything as of now as long as the certificate is valid.
There is nothing to be worried about.
Best regards,
Octavian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2021 02:51 AM
Hello,
Thanks for the answer.
I was pretty sure from the beginning that the answer would be "just delete it, it's useless", but we needed clear confirmation from cisco since it's not obvious from the documentation and the certificate tooltip whether the certificate is actually used or not.
Have a nice day.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2021 02:17 PM
Hi tom.barat@dimensiondata.com ,
as an example for the 3rd option "replace this cisco-provided cert with one of our own":
1st ... to install the CA's Certificate into ISE
At Administration > System > Certificate > Certificate Management > Trusted Certificates:
. Import:
The CA's Certificate
. Trusted for:
Trust for Authentication within ISE
Trust for Client Authentication and Syslog
Trust for Certificate Based Admin Authentication
Trust for Authentication of Cisco Services
2nd ... to generate CSR from ISE for signing it's Certificate from the CA
At Administration > System > Certificate > Certificate Management > Certificate Signing Requests:
. Generate Certificate Signing Requests (CSR):
Usage: Multi-Use
Node: select the Node
<please enter the other values>
. Bind Certificate
<select the Certificate Request that you generated and bind to the Signed Certificate>
Usage: Admin, EAP Authentication and Portal
3rd ... to install the CA's Certificate on your Clients. (as an example not only for ISE, but also for your Clients)
Download the CA's Certificate
Install Certificate
Store Location: Local Machine
Certificate Store: Trusted Root Certification Authorities
Hope this helps !!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2021 02:54 AM
Hello,
Thanks for the answer. If i understand correctly this is the normal certificate provisioning process and ISE will automatically know the certificate requirements when creating the CSR, that's good to know.
Thanks,
Have a nice day.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2021 10:49 PM
Hi tom.barat@dimensiondata.com ,
also take a look at: OK to delete DST Root CA X3 Certificate Authority ?.
Hope this helps !!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2021 09:04 AM
Marcello and Octavian are both correct that this certificate is no longer by any of ISE services by default.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2021 02:45 AM
Hello,
Thank you for the much needed clarification from cisco employee.
Have a nice day.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide