- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.7 - Configurable Password Prompt in RADIUS Token Servers does not work.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE 2.7 - Configurable Password Prompt in RADIUS Token Servers does not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2021 01:01 AM
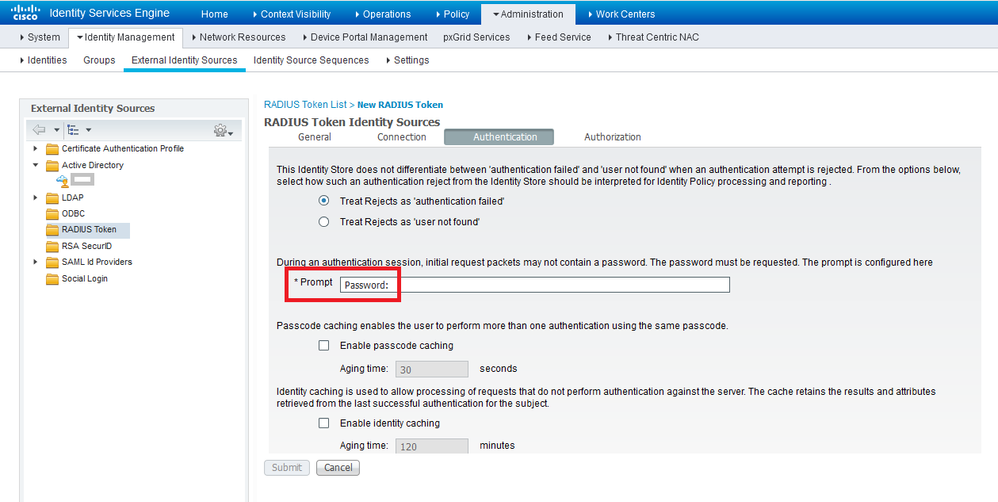
If I configure Password Prompt in the definition of RADIUS Token Server, it will not take effect at login.
ISE Configuration through the Admin portal>
RADIUS Token List > OTP > Authentication - *Prompt "OTP Challenge:"
CLI Login will not change >
Username: user
Password: xxxx
I have used same configuration on the ACS 5.8, where it worked.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2021 03:15 AM
Possibly a bug. I have noticed that the tacacs custom username and password prompts don’t work well either when using SSH. But for telnet it works great. In SSH use case I can only see the custom password prompt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2021 06:59 AM
Yes, ssh and telnet authentication often work differently.
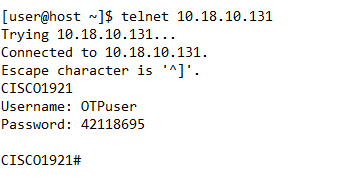
I tested a telnet login on Cisco 1921.
In the case of ACS, the prompt changes but not for ISE.
ACS: internal user - Password Type: "external RADIUS OTP"
Username: user
OTP Challenge: xxxx
ISE: internal user - Password Type: "external RADIUS OTP"
Username: user
Password: xxxx
The situation is same with the "Identity Source Sequences" setting in the Authentication Policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2021 03:11 PM
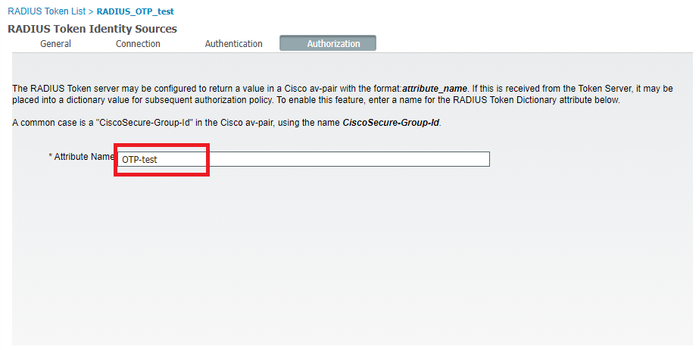
For the Attribute Name, ISE pre-populates CiscoSecure-Group-Id - is your token server returning the Cisco AVPair exactly as ISE expects it? I guess it must, if everything is working
e.g. cisco-av-pair = ACS:CiscoSecure-Group-Id=avaya
But if it's just the prompt that is not being modified, then it smells like a bug to me
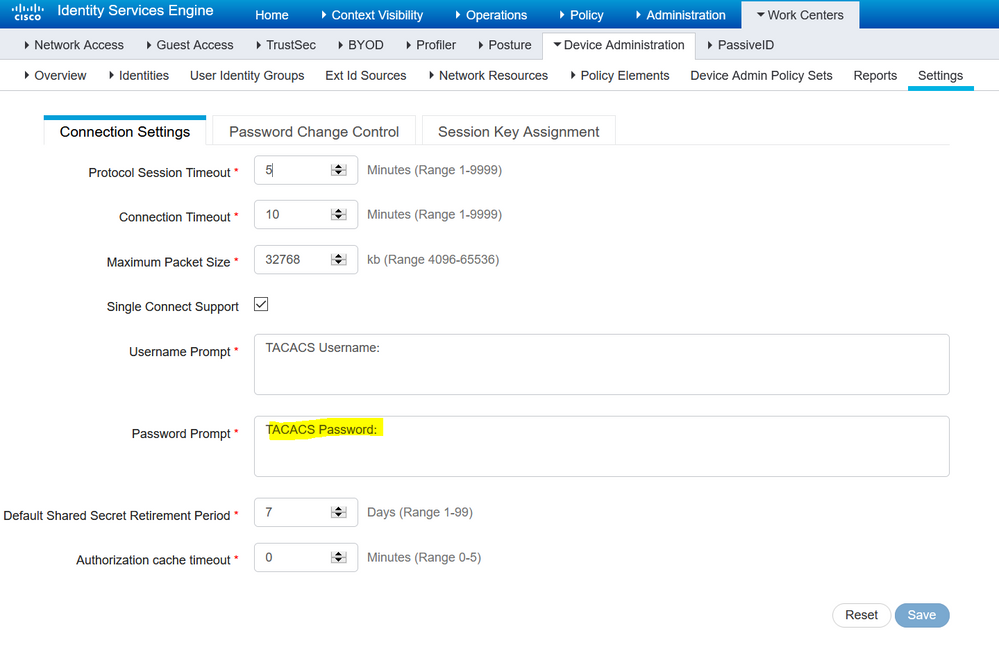
Just checking - you changed the text below in your ISE from "Password:" to something like "OTP Challenge" ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2021 08:04 AM
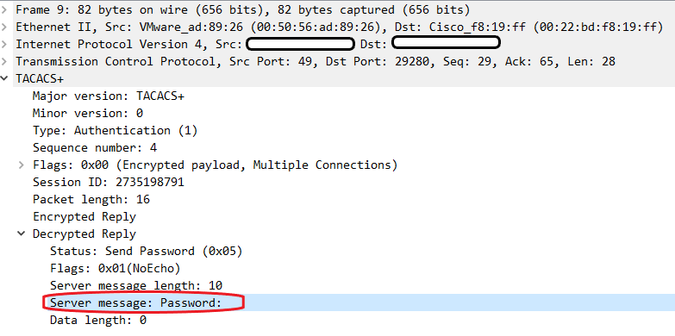
I replicated how working ISE in my case.
cisco-av-pair setting:
cisco-av-pair = ACS:CiscoSecure-Group-Id=OTP-test
RADIUS_OTP_test server reply:
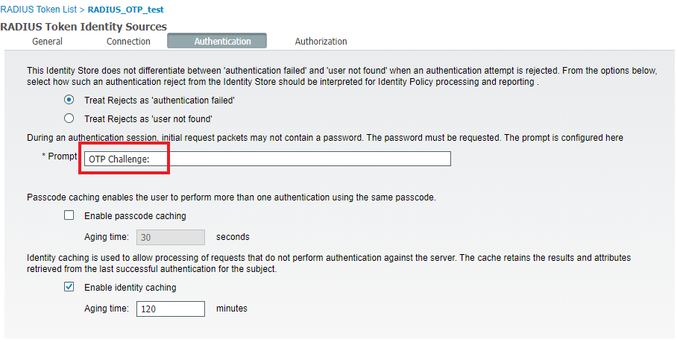
Password prompt setting:
TACACS+ server reply:
Telnet successfull login:
but password prompt has not changed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2021 01:37 PM
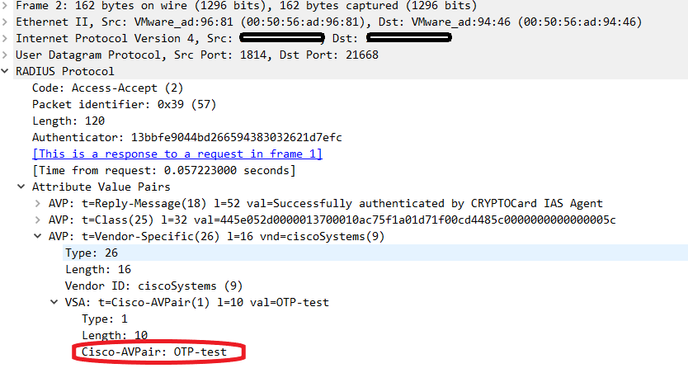
The RADIUS reply is not correct:
Cisco-AVPair= OTP-test
It has to be as follows, because you have overridden the string from the default 'CiscoSecure-Group-Id' to 'OTP-test'
Cisco-AVPair = ACS:OTP-test
When your NAS sends the Access-Accept to ISE then there might be a value assigned to this attribute - e.g.
Cisco-AVPair = ACS:OTP-test=SuperUser
or Cisco-AVPair = ACS:OTP-test=NormalUser
And your ISE Authorization logic can then decide how to treat that user.
So, think of that horrible looking attribute "Cisco-AVPair = ACS:OTP-test" as ONE RADIUS attribute that you can give a value (e.g. SuperUser, NormalUser, etc.) - ISE MUST see the attribute as Cisco-AVPair = ACS:<custom_attr_name> where the <custom_attr_name> is by default CiscoSecure-Group-Id - and in ACS it was Filter-Id.
Hope that works
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2021 07:00 AM
Hi Arne,
We discussed parameters related to authorization against the RADIUS Token server.
However, the issue I am dealing is password prompt that is not being modified.
It's still not working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2021 01:45 PM
What does this screen look like on your ISE?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2021 04:26 PM - edited 03-21-2021 04:27 PM
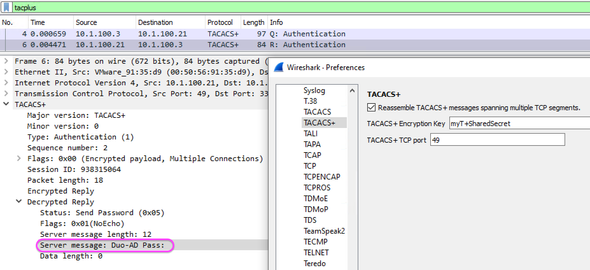
ISE is working for me, even with SSH.
I found the custom prompt ("Duo AD-Pass:") shown in the T+ server reply.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide