- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.X limitation
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2018 06:48 AM
- Can we configure two different certificate authorities in the solution for authentication?
- If we can what are the limitations? For example, we will be unable to use both AD identity sources in the same policy.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2018 08:39 AM
Yes, you can define multiple external CAs but ISE can only run one internal CA, or be subordinate for one external CA. Authentication is via cert, not ID store, but authorization can reference multiple ID stores. Cert Profile will reference specific cert fields.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2018 08:39 AM
Yes, you can define multiple external CAs but ISE can only run one internal CA, or be subordinate for one external CA. Authentication is via cert, not ID store, but authorization can reference multiple ID stores. Cert Profile will reference specific cert fields.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2018 10:02 AM
Roger,
When you check the "Trust for Client Authentication and Syslog" option on any cert you import in the Trusted certificate section of ISE you are telling ISE that that CA can issue client certs and ISE can authenticate them.
The issue you have to watch out for is the cert structure on each of the CAs. Ideally, the cert templates in each CA would place identity information in a similar location. Most modern templates should be using the SAN field to hold identity information. If that is the case, then you can setup one cert profile that tells ISE to check the SAN field for identity information. You have the option to tie your cert profile into AD as well, which I would do in your case.
So assuming you have a cert profile that checks that extract identity information from the SAN field here is what would happen during authentication/authorization.
- Authentication- ISE will authenticate the presented certificate to ensure that the cert is not expired, it was issued by a CA that has the "Trust for Client Authentication" enabled, and that the cert is not revoked (assuming you have revocation checking enabled). As part of this process the identity information will be extracted from the cert using the cert profile specified, i.e. SAN field.
- Authorization- you can do AD group checks. ISE will take the extracted identity information and do AD checks. Note: if the identity in the certificate is not a fully qualified object (user or computer) you may need to set the advanced option in your AD configuration to have ISE check all whitelisted domains for to find the object. If you don't set that setting, ISE will only check the domain it is joined to.
If the CAs don't have consistent identity placement in their templates then you need to create multiple cert profile and have multiple authentication rules to direct ISE to the correct cert profile based on what CA issued the cert.
Hope this helps. Craig let me know if I misstated anything. This is how I explain the process to my customers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2018 06:46 PM
Regarding #2, I think you have it reversed. If domain is specified (for example, jsmith@domain1.com), then we will limit the lookups to that particular domain and avoid ambiguity in username. If no domain specified, then ISE will search all domains for that username. Whitelist helps reduce the total domains searched.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2018 08:18 PM
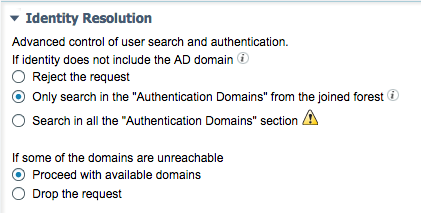
It doesn’t search all whitelisted domain by default which was why I talked about #2. I just ran into this issue.
There is a setting in the advanced tab for the domain that says “Advanced control of user search and authentication if the identity does not include the AD domain”. The default is “Only search in the Whitelisted domain from the joined forest”. ISE will not search across two way trusts unless you change the setting to “Search in all the whitelisted domain section”.
That was my point. Something to watch out for.
I had a customer migrating from Domain A to Domain B. There was a two way trust between Domain A and Domain B. We joined ISE to Domain B. With the default setting we had to fully qualify the domain A users anytime we wanted to use them. With the change ISE now searches both domain for users that don’t have domain specified.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2018 08:58 PM
That is correct and thanks for clarifying it further. Only the earlier post said, " ... If you don't set that setting, ISE will only check the domain it is joined to. ... " That sounds, as if ISE searching one and only one domain in the forest.
Here is the screenshot showing the default.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2018 09:02 PM
Yep good call. I should have been more clear in my first response.
Good stuff.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide