- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE and Kerberos only AD
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2018 07:12 AM - edited 11-16-2018 07:54 AM
Hello,
I have a customer that is trying testing ISE with an AD where he is turning off NTLM, and using only Kerberos.
He says that when he tests a used from the test function directly, choosing Kerberos, all is fine.
But when the has the client using dot1x (MSCHAPv2), then he gets a failute from ISE, saying user unknown or wrong password.
He has checked the Kerberos Checkbox under the advanced capabilities in ISE (even if he is wondering why the setting says plain text password there).
Can you please help us in understanding if it should work?
Thanks a lot
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2018
08:19 AM
- last edited on
11-16-2018
08:40 AM
by
Jason Kunst
![]()
See Solved: SMB 445 protocol for AD integration in ... - Cisco Community
Kerberos only can be used for plain-text authentications, such as guest portal logins.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2018 08:06 AM
Have you tried to debug during the authentication? That should give more information around where the error is occuring.
Regards,
-Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2018
08:19 AM
- last edited on
11-16-2018
08:40 AM
by
Jason Kunst
![]()
See Solved: SMB 445 protocol for AD integration in ... - Cisco Community
Kerberos only can be used for plain-text authentications, such as guest portal logins.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2018 09:14 AM
Hi Hsing,
thanks.
so for dot1x, ISE will always speak NTLM to AD, and the protocol cannot be disabled , in order to enable Kerberos only?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2018 03:57 AM
Thanks Hsing,
We will ask the customer to test with GTC hat is a plain text password (they will have to use AnyConnect for that. Should it work as it is plain text?
Thanks a lot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2024 02:21 PM
For a solution posted by @hslai I am attempting to follow the link from https://community.cisco.com/t5/network-access-control/ise-and-kerberos-only-ad/td-p/3748136 "See Solved: SMB 445 protocol for AD integration in ... - Cisco Community" but denied access.
I am trying to access this page https://community.cisco.com/t5/security-discussions/smb-445-protocol-for-ad-integration-in-ise/m-p/3452622#263834
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2024 03:23 PM
@GeorgePerkins0204 That thread is posted in Cisco Security Partners forum.
ISE can't use AD without port 445. This is required for MS-RPC.
If your customer fears "Wannacry", please explain that it is an SMB1 exploit. ISE uses SMB2. The customer can disable SMB1 on the DCs, leaving SMB2 up.
SMB is needed for several things. It is the ONLY protocol that can authenticate PEAP EAP-MSCHAP credentials. So it is usually not an option to disable it…
Using AD as LDAP, we can't authenticate using EAP-MSCHAPv2, beside we won't be able to take advantages of Active Directory Sites and Services for HA and all the other benefits that ISE AD connector offers. ...
BRKSEC2132 is no longer at CiscoLive site so I attached the PDF file.
Also take a look at Understand Identity Service Engine (ISE) and Active Directory (AD)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 08:18 AM - edited 01-12-2024 08:22 AM
I cannot find documentation or blogs or tips where I turn off NTLM authentication in ISE. Like the original @martucci post, we are a customer that needs to turn off NTLM on all domain devices and users. Audit of NTLM group policy settings are enabled to find all sources of NTLM authentication in the domain. I see ISE continuously using NTLM for user and device lookup in AD.
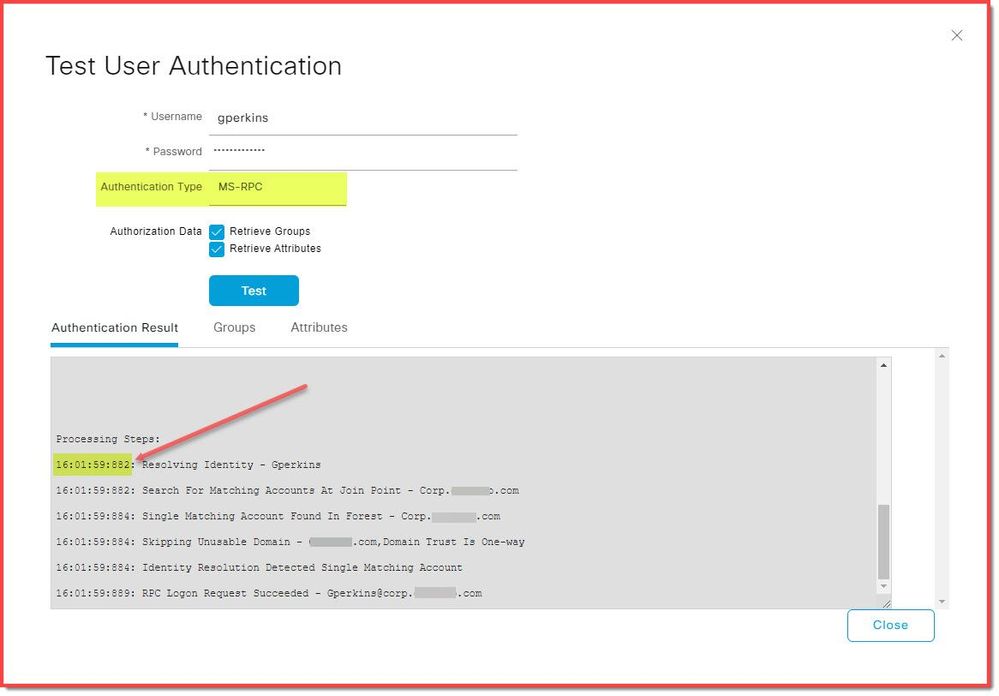
I use ISE Administration > Identity Management > External Identity Sources > Connection > select ISE node > Test User
There are three Authentication Type options in the Test User dialog: Kerberos, Lookup, MS-RPC. When I test each type they all work, returning expected results. Only the MS-RPC authentication type logs an NTLM audit record. The question then becomes, how do I disable MS-RPC lookups in ISE and require ISE to use only Kerberos?
| Log Name: Microsoft-Windows-NTLM/Operational Source: Microsoft-Windows-Security-Netlogon Date: 1/12/2024 10:01:59 AM Event ID: 8004 Task Category: Auditing NTLM Level: Information Keywords: User: SYSTEM Computer: GHCDC003.corp.blur.com Description: Domain Controller Blocked Audit: Audit NTLM authentication to this domain controller. Secure Channel name: ONSNS3615ISE User name: gperkins@corp.blur.com Domain name: NULL Workstation name: \\ONSNS3615ISE Secure Channel type: 2 Audit NTLM authentication requests within the domain NULL that would be blocked if the security policy Network Security: Restrict NTLM: NTLM authentication in this domain is set to any of the Deny options. If you want to allow NTLM authentication requests in the domain NULL, set the security policy Network Security: Restrict NTLM: NTLM authentication in this domain to Disabled. If you want to allow NTLM authentication requests to specific servers in the domain NULL, set the security policy Network Security: Restrict NTLM: NTLM authentication in this domain to Deny for domain servers or Deny domain accounts to domain servers, and then set the security policy Network Security: Restrict NTLM: Add server exceptions in this domain to define a list of servers in the domain NULL to which clients are allowed to use NTLM authentication. Event Xml: <Event xmlns=http://schemas.microsoft.com/win/2004/08/events/event> <System> <Provider Name="Microsoft-Windows-Security-Netlogon" Guid="{e5ba83f6-07d0-46b1-8bc7-7e669a1d31dc}" /> <EventID>8004</EventID> <Version>0</Version> <Level>4</Level> <Task>2</Task> <Opcode>0</Opcode> <Keywords>0x8000000000000000</Keywords> <TimeCreated SystemTime="2024-01-12T16:01:59.8876250Z" /> <EventRecordID>8663101</EventRecordID> <Correlation ActivityID="{91cb7c06-3883-0001-a87c-cb918338da01}" /> <Execution ProcessID="768" ThreadID="1440" /> <Channel>Microsoft-Windows-NTLM/Operational</Channel> <Computer>GHCDC003.corp.blur.com</Computer> <Security UserID="S-1-5-18" /> </System> <EventData> <Data Name="SChannelName">ONSNS3615ISE</Data> <Data Name="UserName">gperkins@corp.blur.com</Data> <Data Name="DomainName">NULL</Data> <Data Name="WorkstationName">\\ONSNS3615ISE</Data> <Data Name="SChannelType">2</Data> </EventData> </Event> |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 11:49 AM
I have started a new topic since the above reply is to an old, closed thread. Please see: turn-off-ntlm-in-ise-use-kerberos-instead
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide