- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Ise automatic profiling disable
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ise automatic profiling disable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2022 10:46 AM - edited 02-10-2022 10:47 AM
Hi,
I was trying to develop a guest access portal solution with wired mab.
The switch and ise configured with standard configuration.
The policy is simple, when the user enter correct username/password they will get network access and their mac address will be added to a endpoint identity group. When they try to use the network again they do not need to reauthenticate again, because their mac adress is already in the endpoint database.
But what ise doing automatically is that it is receiving information from the switch and already dynamically assigns the guest compter in workstation-windows10 endpoint group. Ise does this because of different factory predefined policies for profiling.
What now happens after successful login throgh guest portal, the mac adress is not added to my custom endpoint group, because it is already in the dynamically profiled endpoint group. So, after radius coa, the host is redirected to the guest portal again because the mac adress not added to my custom endpoint group.
Can a mac adress belong to two groups at the same time. One in dynamically proling policy based group and my custom group?
Or anyway to disable this auto profiling?
Ideal would be if Ise allows mac adress to my custom group even though it is in the dynamic group.
Help is appreciated.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2022 05:27 AM
But what ise doing automatically is that it is receiving information from the switch and already dynamically assigns the guest compter in workstation-windows10 endpoint group. Ise does this because of different factory predefined policies for profiling.
-Have you attempted to try profiling these guest clients with a higher MCF so they dont match default out of box profiling policies? What about adding extra conditions in the radius authz policy so that the guest clients match the respective policy you want. Perhaps guests connect in same area so you could focus on that as an extra condition?
Or anyway to disable this auto profiling?
-I would not recommend disabling the profiling probes as that will limit/hurt your context visibility for attributes collected about devices on the network. You just need to find unique attributes/conditions to use so they clients hit your desired policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2022 01:42 PM - edited 02-11-2022 01:45 PM
Hi,
Thanks for your reply. I have mentioned that I am trying to develop a guest CWA solution with ISE. Guests client can be wired or wireless. Guests will be presented with portal and after authentication their mac addresses will be put into a endpoint group, so that for next 7 days they do not need to reauthenticate again.
And the problem is I do not want different guest devices (phone, pc, tablet) to be profiled by ISE and automatically put into different groups.
Problem -
1. I cannot put every single those auto profiled endpoint group in my authz policy.
2. I need to put them in custom group because I need to avoid reauthentication frequently. Also fails mac never added to custom endpoint group.
My current authz policy (according to matching order)
1. Detect wired/wireless mab then redirect to CWA portal. - Guest are redirected portal. This step works.
2. Detect mab and a user belongs to a custom usergroup and mac adress belongs to a custom endpoint group - allow access (this fails because no matching of the endpoint group which I have mentioned in the CWA portal, mac adress not added after successful authentication because it is already in auto profiled group, ISE does not allow mac in two different endpoint group).
3. Detect mab and mac address belongs to a endpoint group - allows access (avoids reauthentication through portal again).
I have not idea how to add more conditions in authz, because it is mab and I need to put mac adress in a endpoint group.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2022 03:49 PM
Hi @ssajiby2k
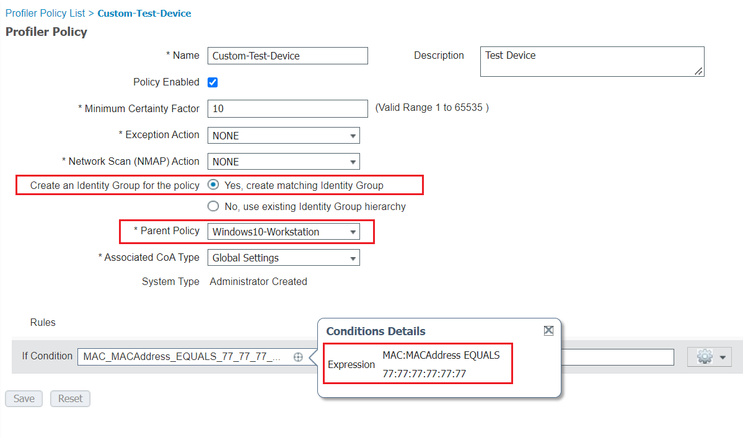
1st ... create a Custom Profile Policy as a child of the Auto Profiling Policy, i.e., at Work Centers > Profiler > Profiling Policies: Workstation > Microsoft Workstation > Windows 10 - Workstation > Custom Test Device, for example:
2nd ... for the Authorization Policy, you have two options
a. Identity Group (when you check the checkbox Yes, Create matching Identity Group - ex. above)
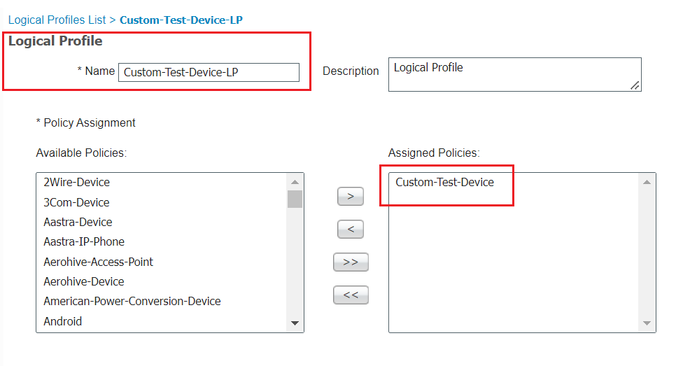
b. Logical Profiles ... for ex.:
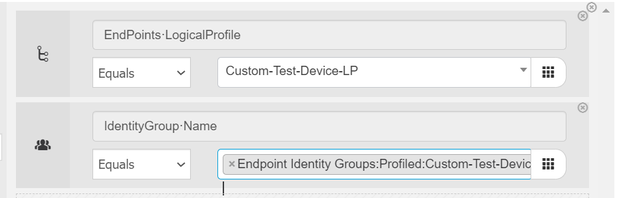
At Policy > Policy Set you are able to use one of the following as a Authorization Policy Condition:
Hope this helps !!!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide