- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE Certificate replacement issues
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE Certificate replacement issues
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 06:03 AM
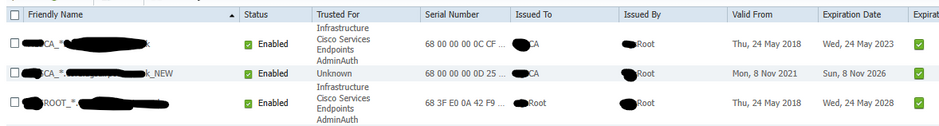
We have a Distributed deployment with 1 PAN, 1 SAN, 3 Nodes. We've replaced the System certificate on one of the Node, we've also uploaded the new intermediate CA cert in the Trusted certificates section. When we go to change the second (second in the list) certificate' option for "Trusted for Infrastructure, Cisco services, endpoints and admin auth" we get the below message
The reason for the second trusted certificate is due to having a new intermediate CA server (as the first one is expiring).
The PAN SAN and the other 2 nodes (out of 3) certificates are signed by the current CA (first in the list). These are all due to renewal as well.
Does this mean to make the second Trusted certificate work, i need update the system certificates for all the remaining devices (PAN,SAN, 2 nodes signed by the new CA (second on the list) then remove the trusted for options on the first trusted cert for all of it to work?
Apologies this is a long-winded post, but i am hoping someone else has had a similar issue/conundrum when it came to replacing the cert.
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2023 12:30 AM
Hi,
There is check in code that will not allow update to a Admin Cert with Cert Based Authentication, if there is another Trust Cert with Admin Role and also enabled for Cert based Authentication. As said in the alert message need to disable cert based authentication of the other cert and update this trust cert.
This is expected behaviour and not an error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2023 05:50 AM
Hi Poongarg
On the second CA certificate we've enabled the "Infrastructure and Endpoints" however the node we'd replaced the system certificate on is still not handling Radius requests.
From ISE manuals, it wont work until we move the admin role to the second CA certificate to allow connectivity between the node and the PAN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 09:39 PM
No, the admin and the EAP server certificates need not be the same one.
> ... however the node we'd replaced the system certificate on is still not handling Radius requests.
If the new system certificate is configured as the EAP server certificate of the ISE node and if the EAP-based authentications are not working against this ISE node, take a packet capture (e.g. tcpdump) and verify if this ISE node is sending the full certificate chain properly. Please engage Cisco TAC, as needed.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide