- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE DACL does not allow host to obtain DHCP address from cisco switch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE DACL does not allow host to obtain DHCP address from cisco switch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 09:48 AM
We run ISE version 2.4
We have a DACL that gets assigned to specific MAC addresses to restrict their access to the LAN.
One of the entries in the DACL is as below to allow the host to pick up a DHCP address
permit udp any eq bootpc any eq bootps
When we host the DHCP on a remote server this works fine.
If we host DHCP services on a local cisco switch the host never picks up an IP address
Even if I change the DACL so it has a "permit any any" entry it still does not pick up an IP address.
It would seem that unless the DHCP requests are forwarded it does not reference the DACL until it picks up an IP address.
How can I assign a DACL in this situation?
- Labels:
-
Network Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2022 07:21 AM
Idid not have that command, I added it but no difference.
This is my AAA config:
aaa new-model
!
aaa group server radius ISER
server-private A.B.C.D key 7 045F0E251vvvvv31
server-private A.B.C.D key 7 070B24vvvvvv102F
ip radius source-interface Vlan0x0
!
aaa authentication login default group ISE local
aaa authentication enable default group ISE enable
aaa authentication dot1x default group ISER
aaa authorization network default group ISER
aaa accounting update newinfo periodic 2880
aaa accounting identity default start-stop group ISER
aaa accounting commands 0 default stop-only group ISE
aaa accounting commands 1 default stop-only group ISE
aaa accounting commands 15 default stop-only group ISE
!
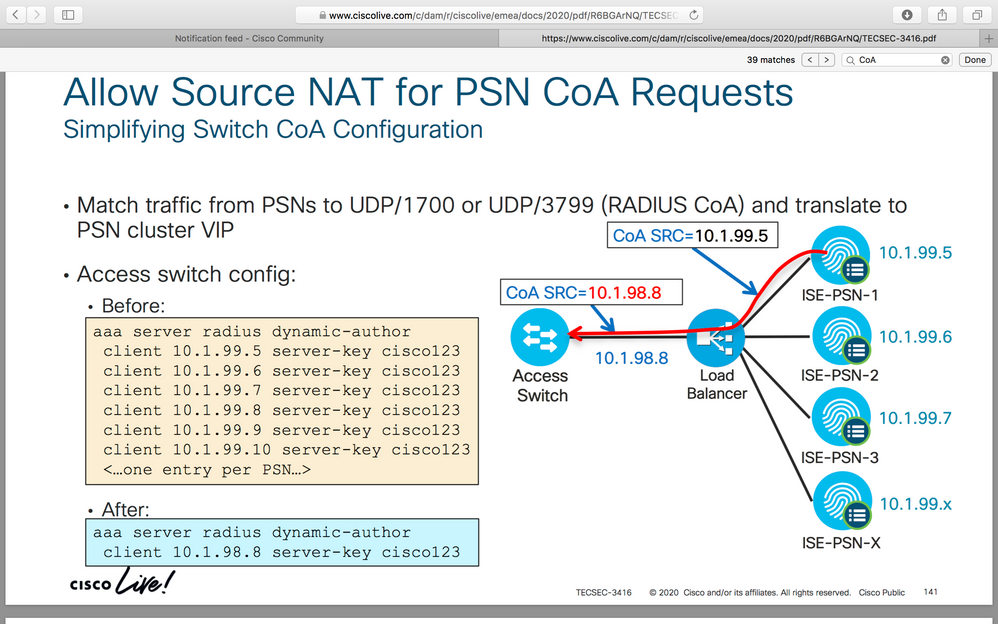
aaa server radius dynamic-author
!
aaa session-id common
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2022 07:58 AM - edited 06-30-2022 08:16 AM
check this guide there are some command you need to add to make CoA work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2022 08:51 AM
CoA works just fine for all sites except this one.
I have other sites that use DACL's without any issue, some have a local ISE server and some use an ISE server behind a DMVPN tunnel.
This site is the only one behind a Checkpoint P2P tunnel and we cannot get the CoA to work over this tunnel.
We do not have dynamic-author configured in any other site, but for due diligence I added the dynamic-author to this site, unfortunately it did not make any difference.
Seems when we add a DACL to the mix for this site it never gets past the Access Request - Access Challenge - Access Request loop.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2022 08:28 AM
I have been doing more discovery with this and I can get it to work but not consistently.
First I took the Standard PERMIT_ALL_TRAFFIC DACL and applied that to the Auth Profile, this allowed the client to connect, was authorized and downloaded the "permit ip any any" DACL
I then made a copy of the PERMIT_ALL_TRAFFIC DACL, renamed it to what I want for my DACL and applied this DACL to the Auth Profile, again I was able to connect and get authorized.
So I then decided to edit the DACL I had just copied and add all the DACL entries I need to protect my network, this also allowed the client to connect, was authorized and downloaded the full DACL.
So I then left it for 5 - 10 minutes, shut and no shut the port and then I was back to the original problem, unauthorized and not downloading the DACL. (sometimes I can reset the port 5 or 10 times but then at some point it will go to unauthorized)
I then found if I change the DACL, even slightly and then reset the port, it will work successfully but then if I reset the port again it will no longer work unless I modify the DACL again.
So I guess what confuises me the most is that it works for a while but will always revert back to unauthorized and only a change to the contents of the DACL will get it to authorize once it has failed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2022 09:09 AM
just one Q may be I am wrong
but CoA use in case of auth client and then use another auth process for client and hence we need CoA to not authz the client for first auth.
you mention that other site work with out CoA command I mention before are they even use CoA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2022 12:45 PM
Hi
How many ACEs does your "full" DACL have? Could possibly be a TCAM utilization issue - thread below outlines some TCAM troubleshooting steps.
hth
Andy
https://community.cisco.com/t5/network-access-control/dacl-with-over-100-lines/m-p/3866198
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2022 11:15 PM
It has been a couple of weeks now of back and forth and real troubleshooting information has been difficult to get.
Please see How to Ask The Community for Help .
I recommend creating a TAC case so they can get the necessary configuration details and debugs to troubleshoot it.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide