- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE EasyConnect and 802.1X machine authentication integration...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE EasyConnect and 802.1X machine authentication integration...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2022 01:28 AM - edited 03-07-2022 01:29 AM
Hi all;
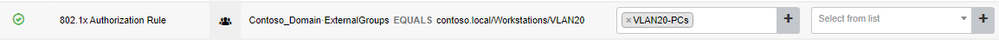
Because of some limitations of implementing User-based 802.1X port-based authentication (like, a user cannot change an expired password), I want to implements machine-based 802.1X authentication (based on PEAP - MSCHAPv2). Based on this document, it is a supported scenario. So, I have implemented machine-based 802.1X and now everything looks great. Please look at the following figure:
I have created the above Authorization Policy for the purpose of this scenario (machine-based 802.1X authentication).
Now, I created the following Authorization Policy for the purpose of implementing EasyConnect:
Although I have enabled the "Passive Identity Tracking" option for "HR_Users" Authorization Profile, when a user in "HR_Users" group logins to the machine, ISE does not match with the above rule!
Any ideas?
Thanks
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2022 01:59 PM
Is your integration with AD working correctly? It's been a while since I tried this, but I recall that you can see all the events in ISE (if the WMI integration is working)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2022 11:58 PM
Thanks for your reply...
My first question is that, is this scenario supported by Cisco?
My second question is, are the configured policies are correct?
Yes, I have checked the AD integration, and everything is OK!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2022 08:17 PM
If your ISE is of 2.2 before Patch 17, 2.4 before Patch 13, 2.6 before Patch 7, you might run into a known bug which resolved in these patch releases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2022 06:12 AM
Thanks for your reply;
Can you please give me the link of any docs that help me to implement this scenario?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2022 12:16 PM
You can try this link here.
And Labminutes.com has a two part video series where you can watch how it's done (Easy Connect using Passive ID)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide