- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE integration with MS Intune - Auto discovery URL
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2019 06:06 AM
Hi ISE experts
We have a customer integrating ISE with Intune. The MS supplied "Auto Discovery URL" was "graph.microsoft.com" but I checked around and the suggested URL was "graph.microsoft.net". So the customer tried that, and .net works instead of .com
Supplied https://graph.microsoft.com/xxxxxxxxxx
Working https://graph.windows.net/xxxxxxxxxx
Did anyone get it to work with ".com"
I have no visibility of what Intune is showing, but the ".com" was the MS general recommendation, but clearly didn't work. Is this an error, or is there some pointers in Intune to ".net" also?
This is happening more the once from what I can see. Is there an error in Intune, or is ISE not doing something right with .com?
thanks
Mark
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2019 07:56 PM - edited 06-29-2019 08:00 PM
I just checked the URL you provided and it looked like already corrected.
Both Microsoft Intune as MDM server for Cisco ISE – Rohit Goel’s Blog and How to Integrate Microsoft Intune with ... - Cisco Community show it a string value for "MICROSOFT AZURE AD GRAPH API ENDPOINT" from the MS Azure management portal.
| ISE | Intune |
| Auto Discovery URL | Endpoints > Microsoft Azure AD Graph API Endpoint |
| Client ID | {Registered-App-Name} > Application ID |
| Token Issuing URL | Endpoints > OAuth 2.0 Token Endpoint |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2019 07:50 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2019 02:45 PM
hey Jason
So, from the Intune setup (https://www.cisco.com/c/en/us/td/docs/security/ise/2-4/admin_guide/b_ise_admin_guide_24/b_ise_admin_guide_24_new_chapter_01001.html#id_37138)
step 8, configuring Auto Discovery URL, we get the URL from MS, but it was originally graph.windows.com. The connection to Intune from ISE failed with this configuration, and the log:
>>>>>>
2019-06-17 12:47:01,567 ERROR [admin-http-pool1][] cpm.mdm.auto.discovery.MdmServerAutoDiscoveryManager -::::- Unable to discover MDM server for IntuneMDM.
com.cisco.cpm.mdm.auto.discovery.MdmServerAutoDiscoveryException: Unrecognized field "error" (Class com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorResponse), not marked as ignorable
at [Source: java.io.StringReader@abcdef; line: 2, column: 13] (through reference chain: com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorResponse["error"])
<<<<<<<
however, I noted in other cases with the same error, specifically the error: Unrecognized field "error" that changing to .net resolved the issue.
I realise this is a URL controlled and published by MS, I just want to understand why ISE may not like the .com, and if there is somewhere else in Intune (as I don't have a login) it show's a .net URL?
cheers
Mark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2019 08:00 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2019 03:02 PM
hi Nidhi
Not at the moment, I'll open one if it helps
cheers
Mark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2019 11:47 AM
I don't have an answer for you, but I can say I've had the windows.net autodiscovery URL configured for several years without issue on my deployment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2019 11:53 PM
The config guide also mentions .net .
you might want to verify the url in intune setup as well . Engineering says there is no such limitation from the code
Auto Discovery URL—Enter the value of Microsoft Azure AD Graph API Endpoint from the Microsoft Azure management portal. This URL is the endpoint at which an application can access directory data in your Microsoft Azure AD directory using the Graph API. The URL is of the form: https://<hostname>/<tenant id>, for example, https://graph.ppe.windows.net/47f09275-5bc0-4807-8aae-f35cb0341329. An expanded version of this URL is also in the property file, which is of the form: https://<Graph_API_Endpoint>/<TenantId_Or_Domain>/servicePrincipalsByAppId/<Microsoft Intune AppId>/serviceEndpoints?api-version=1.6&client-request-id=<Guid.NewGuid()>.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2019 06:21 PM
hi Nidhi
thanks again, the URL supplied by MS via the customer was: https://graph.microsoft.com/........
Our issue here is there are 3 URLs being thrown around.
1. graph.microsoft.com - supplied by customer from Intune. Didn't work
2. graph.ppe.windows.net - Cisco documentation. Didn't work
3. graph.micrsoft.net - found in various TAC cases and not known where it really came from.....Works!
If there's no limitation, why would the first two, well documented, URLs not work?
thanks
Mark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2019 07:08 PM - edited 07-01-2019 07:23 PM
If there's no limitation, why would the first two, well documented, URLs not work?
Please see my earlier response.
The URL is what set in the MS Azure management portal and the customers need copy from the values I indicated there. The URL string given there is an example and will look different on each Azure account.
To be clear, Microsoft Intune as MDM server for Cisco ISE – Rohit Goel’s Blog says,
7. In ISE, configure the Intune server in ISE
For more information about configuring and external MDM server, see Define Mobile Device Management Servers in ISE. The fields that are important for Intune are described below:
- Auto Discovery URL - Enter the value of Microsoft Azure AD Graph API Endpoint from the Microsoft Azure management portal. This the endpoint at which an application can access directory data in your Microsoft Azure AD directory using the Graph API. The URL is of the form: https://<hostname>/<tenant id>, for example, https://graph.ppe.windows.net/47f09275-5bc0-4807-8aae-f35cb0341329. An expanded version of this URL is also in the property file, which is of the form:
...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2019 07:56 PM - edited 06-29-2019 08:00 PM
I just checked the URL you provided and it looked like already corrected.
Both Microsoft Intune as MDM server for Cisco ISE – Rohit Goel’s Blog and How to Integrate Microsoft Intune with ... - Cisco Community show it a string value for "MICROSOFT AZURE AD GRAPH API ENDPOINT" from the MS Azure management portal.
| ISE | Intune |
| Auto Discovery URL | Endpoints > Microsoft Azure AD Graph API Endpoint |
| Client ID | {Registered-App-Name} > Application ID |
| Token Issuing URL | Endpoints > OAuth 2.0 Token Endpoint |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2020 06:51 PM
Unrecognized field "error" (Class com.cisco.cpm.mdm.auto.discovery.MdmAzureDi
rectoryServiceErrorResponse), not marked as ignorable at [Source: java.io.StringReader@4810b402; line: 2, column: 13] (through reference chain: com.cisco.cpm.mdm.auto.discovery.MdmAzureDi
rectoryServiceErrorResponse["error"])
I got this error despite i imported alot of CA cert related.. any advise?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2020 03:14 PM
Have you got any resolution to this ? Cisco documentation is vague at best.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2021 10:45 AM
This is a cert issue. Add these into the Cisoc ISE trust certificate store - 4 certs (2 root and 2 intermediate) need to be in there as well as the URL certificates for the following:
- DigiCert
- DigiCert Sha2 Secure Server CA
- DigiCert Global Root G2
- Microsoft Azure TLS issuing CA 06
- https://login.microsoftonline.com/<Tenat ID>/oauth2/v2.0/token
- https://fef.msuc05.manage.microsoft.com/
- https://graph.windows.net/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 03:46 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 02:37 AM
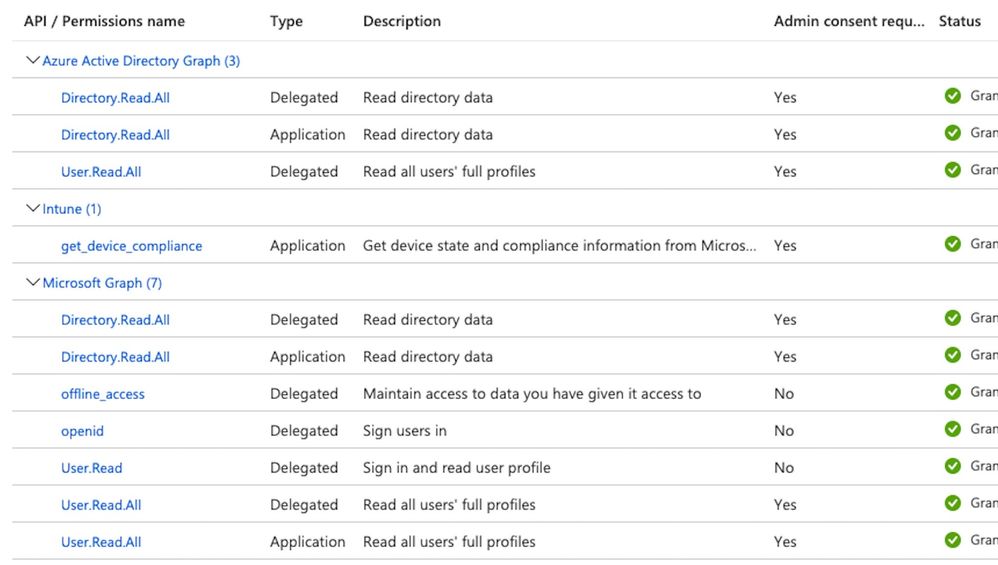
I've integrated Intune successfully recently, with the following settings:
Server Type: Mobile Device Manager
Authentication Type: OAuth – Client Credentials
Auto Discovery: Yes
Auto Discovery URL: https://graph.windows.net/{TenantID}
Client ID: {ClientID}
Token Issuing URL: https://login.microsoftonline.com/{TenantID}/oauth2/v2.0/token
Token Audience: https://api.manage.microsoft.com/
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide