- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE not pulling all identity attributes from AD.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2017 01:43 AM
I'm trying to use the device group condition to create an authorization policy based on user attributes from the AD.
It didn't work out and also got this from the report.
Code 24100 seems to be the problem. Cause I have deployed similar policy for another client and code 24100 seems to be the only strange report I can see.
Thanks.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2017 08:42 PM
The error implies the attribute is empty. If your AD test is done with the same user, are you seeing it differently?
For example, I configured an authz profile to return the attribute "mail" from AD. It does NOT give 24100 when the AD user has non-empty value for this attribute; whereas it gives 24100 for an user not configured for this attribute.
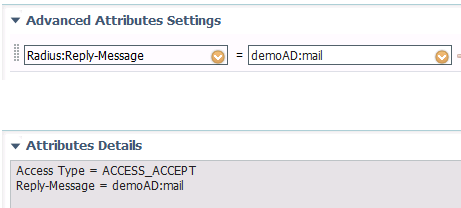
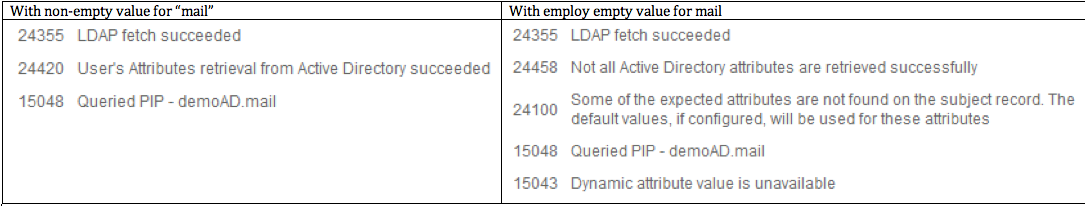
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2017 07:05 AM
did you see these attributes on the client if you use the AD test tool on external identity sources?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2017 11:09 AM
Yes I do. All required required attributes were pulled when I did a test
tool.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2017 08:42 PM
The error implies the attribute is empty. If your AD test is done with the same user, are you seeing it differently?
For example, I configured an authz profile to return the attribute "mail" from AD. It does NOT give 24100 when the AD user has non-empty value for this attribute; whereas it gives 24100 for an user not configured for this attribute.


Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide