- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE operational backup content to syslog instead of backups
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2022 10:03 AM
We found this thread: https://community.cisco.com/t5/network-access-control/ise-operational-backup-content/td-p/4184440 where it indicates that the Operational Data Backup contained basically RADIUS and TACACS logs.
We log most RADIUS and TACACS data to syslog from ISE already, which means that the backups are potentially quite a bit of redundant data, and excess storage usage.
What logging options on ISE would allow us to log all the operational data to syslog and then not worry about the operational data backup at all? Is that even possible?
We fully understand that sysylog will require different talents to generate reports than the GUI, but we already have talent in shop and would only need to determine the various record layouts.
ISE v3.1+ patches
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2022 10:25 AM
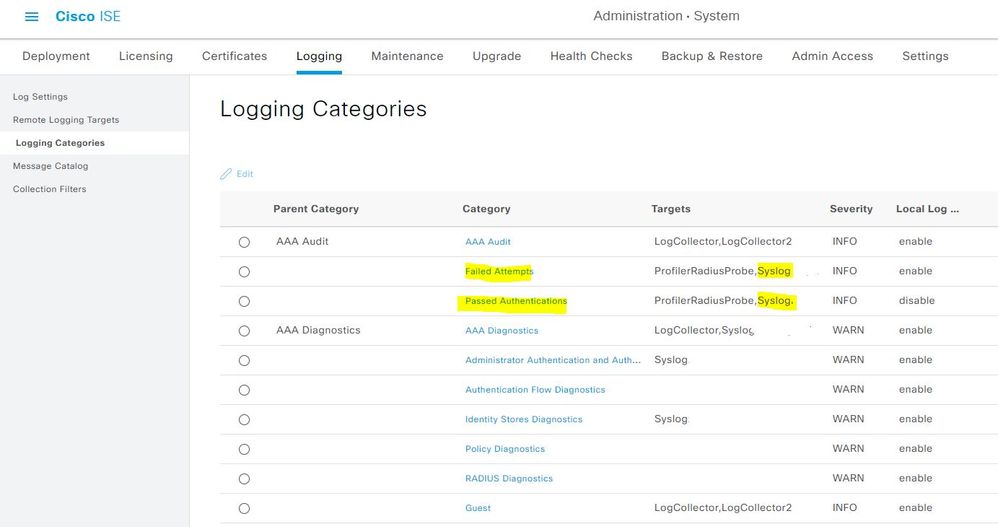
This is pretty easy to do and done quite frequently. It won't be done as a backup but as a new syslog exporter.
- Create a new remote logging target here https://<your-ise-node>/admin/#administration/administration_system/administration_system_logging/remote_log
- Add the new syslog target to the logging categories here https://your-ise-node/admin/#administration/administration_system/administration_system_logging/logging_categories
Depending on what you want to report from the syslog server you will need to enable those logging categories for export. To start you would probably want aaa authentication failed and passed, aaa radius and tacacs accounting as that's the primary data found within the operational backup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2022 10:25 AM
This is pretty easy to do and done quite frequently. It won't be done as a backup but as a new syslog exporter.
- Create a new remote logging target here https://<your-ise-node>/admin/#administration/administration_system/administration_system_logging/remote_log
- Add the new syslog target to the logging categories here https://your-ise-node/admin/#administration/administration_system/administration_system_logging/logging_categories
Depending on what you want to report from the syslog server you will need to enable those logging categories for export. To start you would probably want aaa authentication failed and passed, aaa radius and tacacs accounting as that's the primary data found within the operational backup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2022 10:44 AM
Thanks for the reply! Do you know where there might be specific Cisco documentation? Something that we can point to for an auditor who might think differently about the subject?
We have those already set up because we have historically used syslog so heavily. Again thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2022 03:47 PM
Hi @wags ,
please try the following: Cisco ISE Maintain and Monitor, search for Cisco ISE Logging Mechanism.
Hope this helps !!!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide