- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE return different framed IP address based on the source NAS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2017 07:13 AM - edited 02-21-2020 10:33 AM
Hi,
I have an ISE RADIUS setup where I would like to return a different static framed IP address to a client based on the source NAS that issued the request to ISE.
i.e. if NAS1 sends the request, return user1 framed IP address 192.168.1.1, if NAS2 sends the request, return user1 framed IP address 192.168.2.1
Is there a way of configuring this in ISE?
Many thanks,
Dave
Solved! Go to Solution.
- Labels:
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2017 05:01 PM
Hi Dave
If each user requires a unique Framed-IP-Address (which I assume they do?) based on NAS IP address, then it could get tricky.
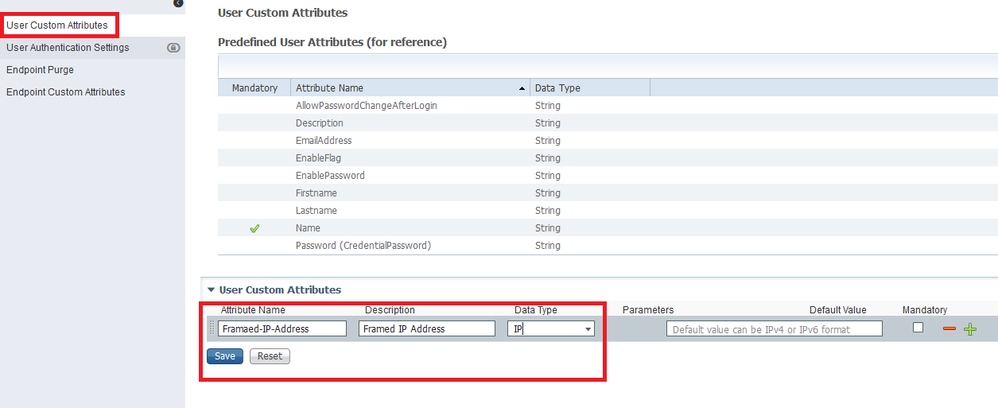
Normally, the way you return a static Framed-IP-Address per named user (if this is what you're trying to do) you would configure the static Framed-IP-Address as part of the local ISE user account. If the authentication and authorization passes then the custom attribute is automatically returned as part of the Access-Accept
I deliberately misspelled the attribute below so that I could search for it in the Authorization policies. In real life I would spell it Framed-IP-Address
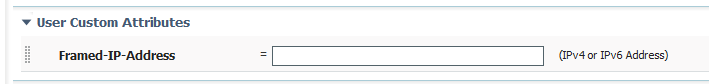
When you edit your local accounts you will then see a new attribute for that user.
So how does one take that to the next level, of making the return value based on NAS IP address? I don't know of any way of manipulating the policy result set during authorization - that would be handy, since then you could perhaps just change the 3rd octet in the user's Framed-IP-Address. We don't get much control over the final result set processing in ISE.
Depending on how many users you have, you may end up having to create an authorization policy PER user and statically return the Framed-IP-Address - which is ugly.
Alternatively, a better approach (depending on where the user ID resides), if the user lives in AD or LDAP, then you could retrieve both IP's user's attributes, and then have a AUthZ policy that decides which one to return, based on NAS-IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2017 05:01 PM
Hi Dave
If each user requires a unique Framed-IP-Address (which I assume they do?) based on NAS IP address, then it could get tricky.
Normally, the way you return a static Framed-IP-Address per named user (if this is what you're trying to do) you would configure the static Framed-IP-Address as part of the local ISE user account. If the authentication and authorization passes then the custom attribute is automatically returned as part of the Access-Accept
I deliberately misspelled the attribute below so that I could search for it in the Authorization policies. In real life I would spell it Framed-IP-Address
When you edit your local accounts you will then see a new attribute for that user.
So how does one take that to the next level, of making the return value based on NAS IP address? I don't know of any way of manipulating the policy result set during authorization - that would be handy, since then you could perhaps just change the 3rd octet in the user's Framed-IP-Address. We don't get much control over the final result set processing in ISE.
Depending on how many users you have, you may end up having to create an authorization policy PER user and statically return the Framed-IP-Address - which is ugly.
Alternatively, a better approach (depending on where the user ID resides), if the user lives in AD or LDAP, then you could retrieve both IP's user's attributes, and then have a AUthZ policy that decides which one to return, based on NAS-IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2017 03:31 PM
Thanks for your reply. I assume if I went down the LDAP route I'd simply store two different attributes per user containing the static IPs and just retrieve/send the relevant one using an authorisation policy per NAS? Is it relatively straight forward to select individual attributes from the LDAP reply? I've only ever used ISE/ACS with an internal user db so am not familiar with this functionality.
Kind regards,
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2018 08:05 AM
I have a similar issue. Using a Palo Alto VPN, a client needs to get assigned an IP based upon the value of an AD extensionAttribute. Neither AD nor ISE actually know or care about the actual IP handed out.
If the AD attribute is set to "A", then we use an IP from VLAN 1. If the AD attribute is set to "B", then we use an IP from VLAN2.
When talking to wired and wireless clients, we use this methodology to request a DHCP address from the pool/scope assigned to that VLAN in a result in AuthZ Profile in the following manner:
Access Type = ACCESS_ACCEPT Tunnel-Private-Group-ID = 1:vlan1 Tunnel-Type = 1:13 Tunnel-Medium-Type = 1:6
However, in the case of Palo Alto, we seem to be limited as to what VSAs it will work with, and it seem that PaloAlto-Client-Source-IP is the only thing that we can send back.
So, instead of DHCP on the client handling the request, apparently, we need to have ISE do this. Any pointers would be appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2018 03:36 PM
The only way I know how to do this is either
- Have an external system that ISE can query for an IP address and then hand that IP back to the Palo Alto in the appropriate radius attribute (PaloAlto-Client-Source-IP ?) - the trick is that your VPN username is the index for the IP address assignment.
- Hard code VPN username to IP address mapping in ISE internal User Identities. You can expand a regular ISE Identity to include any number of Radius Attributes. What then happens is that when Palo Alto performs a Radius Access-Request for user VPN_0001, and if the password matches, then ISE returns ALL the attributes associated with that Internal Identity. So all you need to do is to maintain this within ISE. The IP assignment would be static though - not a big deal if you don't mind managing it
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide