- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE selects weak ciphers for EAP-TLS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2019 12:15 AM - edited 02-21-2020 11:12 AM
Hello,
I am facing a strange issue on ISE 2.6 deployment (latest patch installed).
I have windows clients (7 & 10) authentication through EAP-TLS. They offer 14 ciphers during the TLS handshake, with TLS_ECDHE_RSA_AES256_CBC_SHA being the strongest one, and TLS_RSA_RC4_128_MD5 being the weakest one.
I have two different behaviors depending on what i configure on ISE side :
- If weak ciphers is disabled in the allowed protocols for the matched policy => ISE rejects the client saying it has no common cipher / the client only supports weak ciphers.
- If weak ciphers is enabled => ISE selects the weakest possible cipher in its server hello.
I was not able to find relevent information in the doumentation or bug search tool.
I am wondering whether this could be a misconfiguration on ISE or maybe a bug.
Unfortunately i can't share packet captures as they include client identity and customer name in EAP packets.
Any help is welcome.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
-
Wired
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2019 01:06 PM
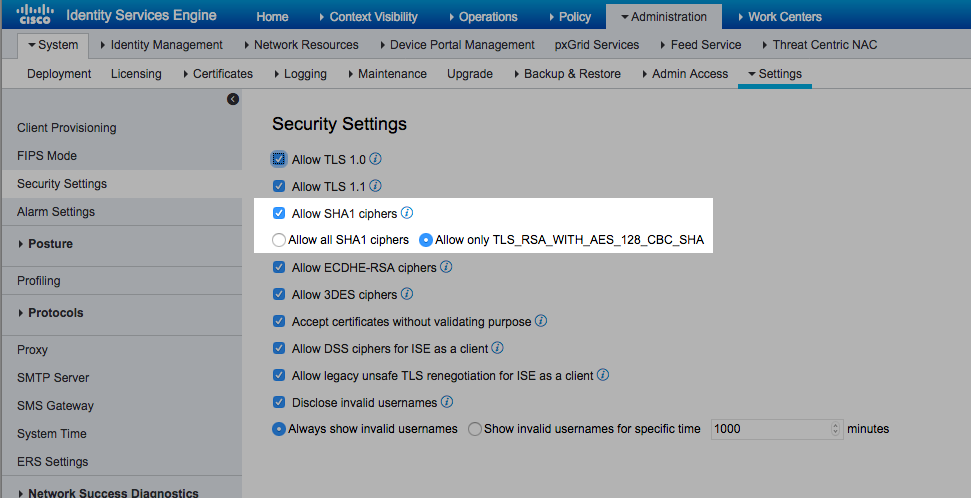
If using ISE 2.6+, the settings needed are Allow SHA1 ciphers and "Allow only TLS_RSA_WITH_AES_128_CBC_SHA" as shown below. The other weak cipher option is to support RC4 for some legacy devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2019 03:43 PM
Hi
it sounds like you have done a wireshark analysis of the TLS handshake. You have listed 14 offered ciphers (from the client side) - what is the ISE response to that? You should be able to see that in the wireshark too. Are you using a hardened version of Win7/10 by any chance?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2019 01:06 PM
If using ISE 2.6+, the settings needed are Allow SHA1 ciphers and "Allow only TLS_RSA_WITH_AES_128_CBC_SHA" as shown below. The other weak cipher option is to support RC4 for some legacy devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2019 02:26 AM
A great thank you, this was indeed the missing setting. Thank you for explaining the difference between weak ciphers and sha1 options.
Have a nice day.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide