- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2021
07:46 AM
- last edited on
03-09-2022
11:15 PM
by
smallbusiness
![]()
Hi Team,
In our Infra devices have been integrated into the Cisco ISE for device Authentication. I need some help with log fetching.
Post tacacs authentication only the end-users can do the device configuration changes.
Now one of the users had done the changes in the device but we don't know which user had been made.
So we need your help to find out the below details based on the log reporting.
1. How to fetch the log report for the last 7 days?
2. Who all are the users can login into the specific device for the past 7 days?
3. And what all are the configuration changes happened to the specific device?
Please clarify the above details ASAP.
Regards,
RK
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2021 01:31 PM
See the section on Cisco ISE Reports in the Admin Guide.
In the Device Administration section of the Reports, you will find TACACS Accounting, Authentication, and Authorization and TACACS Command Accounting reports. If you have these features enabled on the network device, you should see the information you're looking for there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2021 01:31 PM
See the section on Cisco ISE Reports in the Admin Guide.
In the Device Administration section of the Reports, you will find TACACS Accounting, Authentication, and Authorization and TACACS Command Accounting reports. If you have these features enabled on the network device, you should see the information you're looking for there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2022 06:57 AM
Hello Gibbs,
Thanks for providing the idea. I have one more query, please clarify.
I have created one new user in the Tacacs server. Now I have query about how to provide access to the user for some of the specific devices alone? We integrated almost 500 devices into the cisco ISE but the main objective is the created user wouldn't access all the devices, it should access the specific devices only.
Regards,
RK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2022 01:39 PM
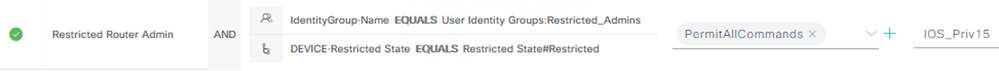
If I understand correctly, you have a set of network devices to which a restricted admin user/group should have access. Ideally, you want to use groups where possible in ISE to improve the ability to scale. One way you could achieve this would be:
- Create a new root-level Network Device Group (e.g. 'Restricted State') with two child groups (e.g. 'Restricted' and 'Non-Restricted)
- Update the relevant network device configurations to use the 'Restricted' value (you can do this in bulk using CSV export/import or via API)
- (Optionally) Create a User Identity Group for your restricted user(s)
- Update your Device Admin AuthZ Policy to match on the groups you created
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2022 07:25 AM
Hi Gibbs,
Thanks for providing the suggestion.
Can you please share any reference link or websites? I am a beginner for the cisco ise and we aren't aware deep in this.
Regards,
R K
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2022 01:20 PM
You should start with the Admin Guide and learning resource links documented here in the NAC Community.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide