- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: MAB authentication instead 802.1x on pc
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
MAB authentication instead 802.1x on pc
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2022 02:22 AM
Goodmorning. we have the followinh problem. On some pc, in random moment, cisco ise authenticate pc using MAB instead 802.1x. So the user reboot the pc or remove & reinsert the ehternet cable and the pc can reauthenticate using user account.
into the ise log i see that the pc is find into AD but try to use MAB and than fail.
802.1x on pc is enabled with GPO. The ip phone (yealink) can authenticate successfully using mab
we have hp aruba 2930 switch.
here the config:
radius-server host 172.18.253.247 key "XXXXXXX"
radius-server host 172.18.253.247 dyn-authorization
aaa server-group radius "ISE" host xxx.xxx.xxx.xxx
aaa authentication num-attempts 10
aaa authentication telnet login radius local
aaa authentication telnet enable radius local
aaa authentication ssh login radius local
aaa authentication ssh enable radius local
aaa authentication port-access eap-radius server-group "ISE"
aaa authentication mac-based chap-radius server-group "ISE"
aaa port-access authenticator 1/1-1/8,1/10-1/19,1/21-1/46,2/10-2/24,2/26-2/32,2/34-2/44,2/46,3/1-3/47
aaa port-access authenticator x/y client-limit 3
aaa port-access authenticator active
aaa port-access mac-based 1/1-1/8,1/10-1/19,1/21-1/46,2/10-2/24,2/26-2/32,2/34-2/44,2/46,3/1-3/47
aaa port-access mac-based x/y addr-limit 3
aaa port-access mac-based x/y reauth-period 60
cisco ise log and cisco ise config is attached
thanks for helping!!
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2022 06:28 AM
can I see the config of one port ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2022 06:49 AM
for example:
interface 2/42
tagged vlan 66
untagged vlan 21
aaa port-access authenticator
aaa port-access authenticator client-limit 3
aaa port-access mac-based
aaa port-access mac-based addr-limit 3
aaa port-access mac-based reauth-period 60
exit
vlan 66 is voice vlan for phone
vlan 21 is lan vlan for pc
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2022 04:15 AM - edited 04-09-2022 04:16 AM
I see only MAC-Based so PC use MAC-Based.
but you can try enable 802.1x-based also if SW support both Auth in same port.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2022 12:05 AM
Hi,
this aaa port-access authenticator and this aaa port-access authenticator client-limit 3 are the command to enable 802.1x authentication user-based (https://techhub.hpe.com/eginfolib/networking/docs/switches/WB/15-18/5998-8152_wb_2920_asg/content/ch13s05.html and https://support.hpe.com/hpesc/public/docDisplay?docId=emr_na-c02642107)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2022 08:58 AM
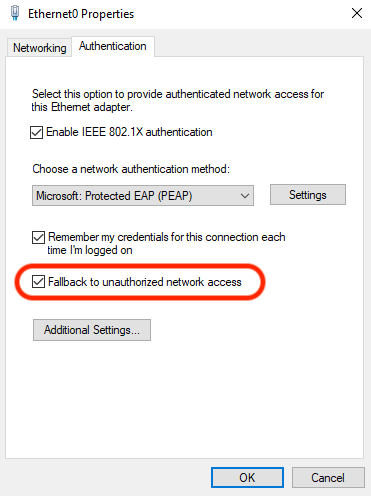
Your ISE log was helpful to understand how and why it was falling back to MAB.
Try turning OFF "Fallback to unauthorized network access" on your supplicant so it will only do 802.1X.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2022 09:03 AM
@thomas but the client is first try 802.1x and then failed and try MAB.
I think that he need
reauth command to make client always reauth and if it not reauth the client will delete form ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2022 09:17 AM - edited 04-12-2022 09:18 AM
If 802.1X failed, why did it fail? You only showed the MAB authentication.
The user may unplug and replug their cable to have the switch start 802.1X or they can login and logout and that will trigger 802.1X from the client side.
I don't know what re-authentication command you are expecting them to use on their computer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2022 05:37 PM
Re auth command in switch not client.
this force sw to Start 802.1x again for this port.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2022 11:56 PM
Hi, yesterday i have set tx period on switch
aaa port-access authenticator 3/35 tx-period 1
(Sets the period the port waits to retransmit the next EAPOL PDU during an authentication session. (Default: 30 seconds))
so, now retansmit every seconds.
@thomas i try to remove the flag, thanks
@MHM Cisco World the re auth is already set, if you see the config there is reauth-period 60 for the mac-based, should i set it also for aaa port-access authenticator?
thanks to everyone!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2022 12:57 AM
Yes you need re auth for 802.1x
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2022 12:07 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2022 12:57 AM
Hi, @MHM Cisco World with reauth enable it was a disaster :D. the PCs lost their network and never re-authenticated themselves
@thomas i've try to remove the flag but the problem still persists
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2022 08:31 AM
Does it do 802.1X if you remove
aaa authentication mac-based chap-radius server-group "ISE"
At this point it appears to be a problem with your HP switch configuration.
Your endpoint supplicant looks OK.
Try other endpoints to verify it is not this one endpoint, also.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide