- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: New to Cisco ISE and wish to know how to configure ISE for Web Auth and MAB from WLC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2017 04:01 PM
We have just bought the Cisco ISE 2.2 (But still running on Eval at the moment) and I am trying to configure this as the MAB authentication for the Cisco WLC – Presently we have a couple of SSIDs which we do Web Authentication on and then failing that goes to MAC Authentication – we do both of these on the WLC – but we want to be able to add the User Data Base for Web Auth and the MAC address lists onto the ISE? (As we have 2 WLC’s is a pain keeping info up to date on both)
I have had a good look around and am having trouble working out exactly where/ how I can do this – could you maybe point me in the right direction? I am on site in PNG at the moment and need to get this sorted before I can leave
Thanks in advance for your assistance.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2017 04:15 PM
Hi Graham
Oh I see. You Create a Endpoint Identity Group that is a container for the MAC addresses you wish to have bypassing the authentication (i.e. to pass the MAB) - below is a summary screen showing a simple EIG containing a dummy MAC address. You can add them in manually or add them from the internal database if ISE has seen the MAC before
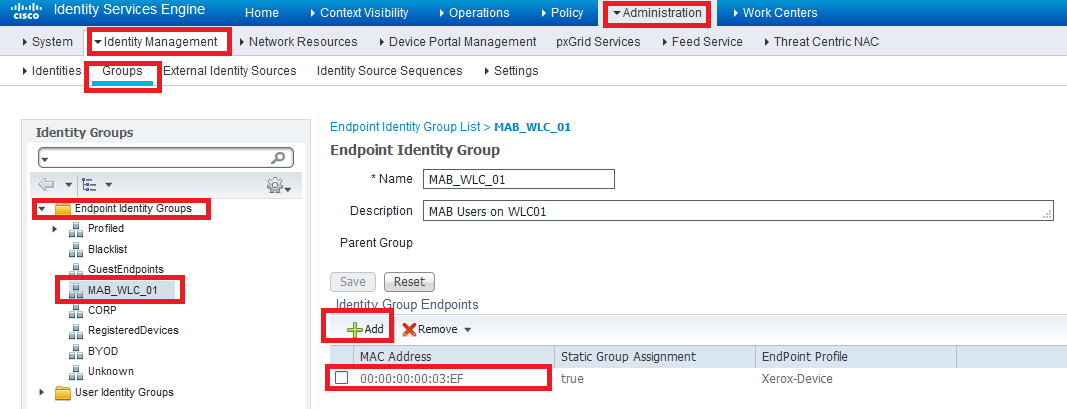
And then you create a AuthZ policy that does something if the MAC is found in the EIG.
I can't recall whether it worked or not, but be careful with creating hierarchies (multi-level EIG's) - I have a feeling that the Policies don't work well (I didn't have success with that in ISE 1.4). Perhaps keep is simple as above and create another EIG for WLC 02 etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2017 04:56 PM
Hi Graham
Not sure I understand your question exactly, but here is my take. You have Web-Auth as well as the ability to auto-login users who have already passed the Web-Auth (so that they don't have to authenticate again within a certain time frame). On the WLC you would have enabled MAC Authentication so that the WLC sends a Service-Type = "Call Check" and the MAC address of the client as soon as the client associates to the open SSID.
With an ISE web portal you can tell ISE in which Endpoint Identity Group to place the MAC address once the user has successfully authenticated. This happens automagically and by default it's the GuestEndpoints (but as I said, you can configure your portal to place the MAC address in any user defined EIG based on the Guest Type (contractor, daily, etc.)).
Your Wirelress MAB Policy should then perform the following Authorization check
If GuestEndpoints AND Wireless_MAB then Guest_Permissions
If Wireless_MAB then Guest_WebRedirect
The first AuthZ Policy will fail when the user first connects, because he is not in the EIG. The second Policy will redirect him to the Portal. Iff the user authenticates successfully on the web portal, then the first Policy will apply - until such time as you remove that MAC address from the EIG.
Examples below
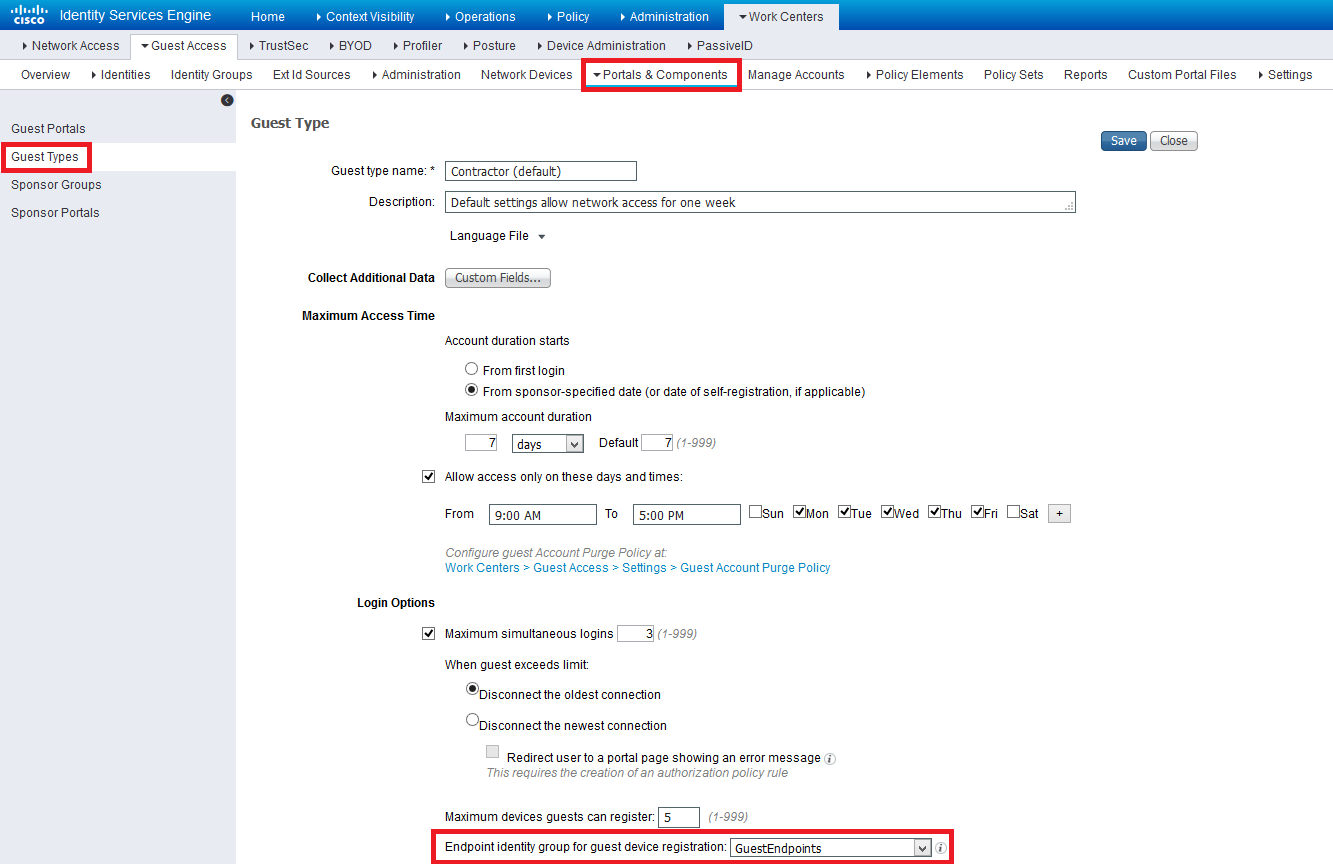

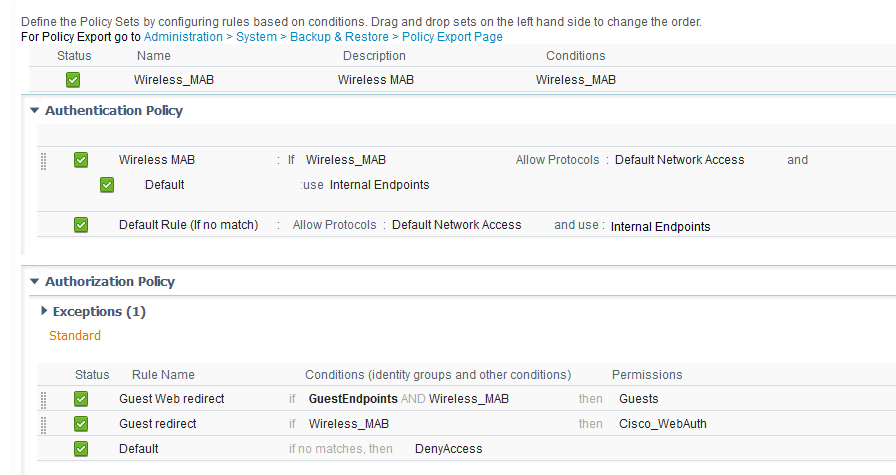
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2017 03:51 PM
thank you for your response. I am trying to understand where on the ISE i can create the MAB entry for the bypass - IE on the Cisco WLC it is currently under Security MAC Filtering - we can set a MAC Address, description, SSID and WLAN -- Where we would we create this detail on the ISE so we can use the ISE as the Database instead of this being on the WLC (Reason being we have more than one WLC and do not wish to create all the MAC Filtering entries on each WLC and went for the ISE so we can have a centralised data base for the MAC filters/ allow. We also perform Web Authentication from the WLC and again this has a local Data base o the WLC under Local Network Users or configured from the Lobby portal. We wish this Data base of users to also be centralised and not have t rely on a local WLC database - but instead each WLC be able to perform a lookup on the Cisco ISE. Thanks in advance for your assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2017 04:15 PM
Hi Graham
Oh I see. You Create a Endpoint Identity Group that is a container for the MAC addresses you wish to have bypassing the authentication (i.e. to pass the MAB) - below is a summary screen showing a simple EIG containing a dummy MAC address. You can add them in manually or add them from the internal database if ISE has seen the MAC before

And then you create a AuthZ policy that does something if the MAC is found in the EIG.
I can't recall whether it worked or not, but be careful with creating hierarchies (multi-level EIG's) - I have a feeling that the Policies don't work well (I didn't have success with that in ISE 1.4). Perhaps keep is simple as above and create another EIG for WLC 02 etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2017 05:06 PM
Graham,
Recommend you take a look at How-To: Monitor Mode Deployment with ISE. See page 13 for how to Create a Whitelist for Endpoints. It will also show you how to Create an Authorization Profile for Whitelisted Devices. That should get you what you need!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2018 10:42 PM
Hello All,
I need to do somewhat similar thing below are the details..
For 802.1x wireless users who have account in AD will be authenticated by AD
and will match the Authorization profile accordingly
For Wireless users who do not have AD account should be authenticated locally and there MAC addresses should be permitted in authorization, how can i do this??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2018 04:54 AM
Details in a new thread. It’s not clear to me
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



