- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Not able to ping gateway from system
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2022 04:00 AM
Hi Team,
I have implemented dot1x with cisco ISE.
Below is switch configuration.
SW1#sh run
Building configuration...
Current configuration : 6616 bytes
!
! Last configuration change at 21:06:15 UTC Mon Mar 1 1993
!
version 15.0
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname SW1
!
boot-start-marker
boot-end-marker
!
enable password Admin@123
!
username admin privilege 15 password 0 Admin@123
aaa new-model
!
!
aaa group server radius ISE
server name ISE
!
aaa authentication dot1x default group ISE
aaa authorization network default group ISE
aaa authorization network cts_list group ISE
aaa accounting dot1x default start-stop group ISE
!
!
!
!
!
aaa server radius dynamic-author
client 192.168.1.21 server-key #B@07rusT
server-key #B@07rusT
!
aaa session-id common
system mtu routing 1500
authentication mac-move permit
ip routing
ip domain-name corp.blockarmour.com
ip name-server 192.168.1.155
ip name-server 8.8.8.8
ip dhcp excluded-address 10.0.10.1 10.0.10.100
ip dhcp excluded-address 10.0.50.1 10.0.50.100
ip dhcp excluded-address 10.0.70.1 10.0.70.100
ip dhcp excluded-address 10.0.100.1 10.0.100.100
!
ip dhcp pool VLAN10
network 10.0.10.0 255.255.255.0
dns-server 192.168.1.155
default-router 10.0.10.1
!
ip dhcp pool VLAN50
network 10.0.50.0 255.255.255.0
dns-server 192.168.1.155
default-router 10.0.50.1
!
ip dhcp pool VLAN70
network 10.0.70.0 255.255.255.0
dns-server 192.168.1.155
default-router 10.0.70.1
!
ip dhcp pool VLAN100
network 10.0.100.0 255.255.255.0
dns-server 192.168.1.155
default-router 10.0.100.1
!
!
!
cts authorization list cts_list
!
crypto pki trustpoint TP-self-signed-2649021440
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-2649021440
revocation-check none
rsakeypair TP-self-signed-2649021440
!
!
crypto pki certificate chain TP-self-signed-2649021440
certificate self-signed 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 32363439 30323134 3430301E 170D3933 30333031 30303038
34325A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D32 36343930
32313434 3030819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
810090A4 0909572A 01C5040B E7859C40 6A4F48EF 09BA7A44 5275E568 B43B728B
57494195 A0F95E22 58A700C4 BA07B797 22D07C3A D6937918 8A3FDF1B EA4A98F7
4B864665 33602417 7B514D13 FAF89BE0 75D06441 121176C7 8A681240 19E3992A
F61BA6FE 0AF97312 931144E0 9D5E9B25 D0DA4BE5 824DBA50 A37F18FE 1267CC06
18D90203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 145559A2 5685AB84 6D082FC6 A33E878E BB803CF5 6A301D06
03551D0E 04160414 5559A256 85AB846D 082FC6A3 3E878EBB 803CF56A 300D0609
2A864886 F70D0101 05050003 8181007B 15EB956F 098493FE E8433C09 49C1C58D
316D3E9D 0A9BD44A 62453083 FB2BE13A 762607FA 286BCDC1 6D62AAAA 2DFAE67F
3DD1BA14 26F3525C 89F3D9D5 5089D235 B86408B0 298AB5DF A733922F CE8814BC
9D5C6393 D45EDECB 5B39C0F9 F5907859 1FBC6BAA A6642CAE 24E12568 4897FC12
84952E1A 3B5D9FA9 A79F1DB8 0113B1
quit
dot1x system-auth-control
!
!
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
ip ssh authentication-retries 2
ip ssh version 2
!
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
switchport mode access
authentication event fail action next-method
authentication host-mode multi-auth
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
dot1x pae authenticator
spanning-tree portfast
!
interface GigabitEthernet0/3
switchport mode access
authentication event fail action next-method
authentication host-mode multi-auth
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
dot1x pae authenticator
spanning-tree portfast
!
interface GigabitEthernet0/4
switchport mode access
authentication event fail action next-method
authentication host-mode multi-auth
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
dot1x pae authenticator
spanning-tree portfast
!
interface GigabitEthernet0/5
switchport mode access
authentication event fail action next-method
authentication host-mode multi-auth
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
dot1x pae authenticator
spanning-tree portfast
!
interface GigabitEthernet0/6
switchport mode access
authentication event fail action next-method
authentication host-mode multi-auth
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
dot1x pae authenticator
spanning-tree portfast
!
interface GigabitEthernet0/7
!
interface GigabitEthernet0/8
!
interface GigabitEthernet0/9
!
interface GigabitEthernet0/10
!
interface GigabitEthernet0/11
!
interface GigabitEthernet0/12
!
interface GigabitEthernet0/13
!
interface GigabitEthernet0/14
!
interface GigabitEthernet0/15
!
interface GigabitEthernet0/16
!
interface GigabitEthernet0/17
!
interface GigabitEthernet0/18
!
interface GigabitEthernet0/19
!
interface GigabitEthernet0/20
!
interface GigabitEthernet0/21
!
interface GigabitEthernet0/22
!
interface GigabitEthernet0/23
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/24
no switchport
ip address dhcp
!
interface GigabitEthernet0/25
!
interface GigabitEthernet0/26
!
interface GigabitEthernet0/27
!
interface GigabitEthernet0/28
!
interface Vlan1
no ip address
!
interface Vlan10
ip address 10.0.10.1 255.255.255.0
ip helper-address 192.168.1.21
!
interface Vlan50
ip address 10.0.50.1 255.255.255.0
ip helper-address 192.168.1.21
!
interface Vlan70
ip address 10.0.70.1 255.255.255.0
ip helper-address 192.168.1.21
!
interface Vlan100
ip address 10.0.100.1 255.255.255.0
ip helper-address 192.168.1.21
!
ip http server
ip http secure-server
!
ip route 0.0.0.0 0.0.0.0 192.168.2.1
!
!
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 6 support-multiple
radius-server attribute 25 access-request include
radius-server attribute 31 mac format ietf upper-case
radius-server attribute 31 send nas-port-detail
radius-server dead-criteria tries 3
radius-server deadtime 30
radius-server vsa send accounting
radius-server vsa send authentication
!
radius server ISE
address ipv4 192.168.1.21 auth-port 1812 acct-port 1813
pac key #B@07rusT
!
!
vstack
!
line con 0
line vty 0 4
transport input ssh
line vty 5 15
!
end
SW1#
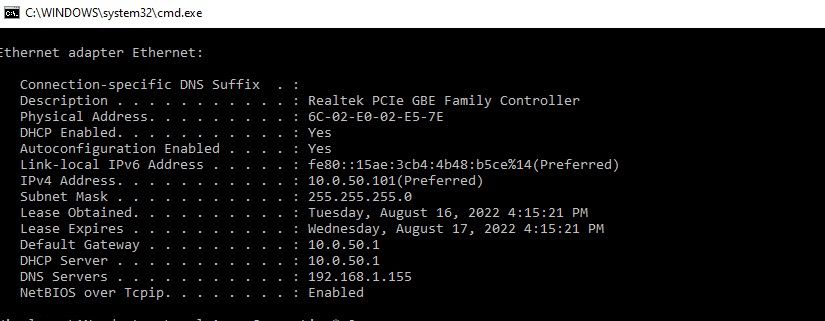
My endpoint (10.0.10.101) are getting authenticated from ISE also vlan is assigned to port and my endpoint is getting IP from pool.
But I am not able to ping my default gateway.
From outside network any one can reach to gateway which is 10.0.10.1
Please can you check.
Solved! Go to Solution.
- Labels:
-
AAA
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2022 06:30 AM
share the following
show auth session interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2022 08:30 AM
Right. show auth session interface|mac and verify whether the client IP address shown as expected. The device tracking needs enabled and configured on the switch because DACL relies on it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2022 10:58 PM
Hi @prathamesh002 ,
1st double check if you are able to ping other IP Addrs.
2nd double check if the port of your Endpoint is not blocking any ICMP packet via a dACL from ISE.
Hope this helps !!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2022 06:06 AM
permit ip any any
This is Dacl which profile gets when fully authenticated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2022 06:30 AM
share the following
show auth session interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2022 08:30 AM
Right. show auth session interface|mac and verify whether the client IP address shown as expected. The device tracking needs enabled and configured on the switch because DACL relies on it.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide