- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Policy Set Conditions - Cert Check
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Policy Set Conditions - Cert Check
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2018 01:36 PM
When creating policy sets, we create conditions that are checked (like wireless 802.1x or wireless MAB) in order to match on that policy set. In the event of multi-tenancy, especially when not all user devices are named a certain way to reflect their individual business unit, or what NAD they'll come from, anyone have a good way to match on a policy set specific to their BU?
For example, BU A, BU B, BU C.
Create policy sets for each BU.
BU A - Wireless or Wired .1x and ?
I was thinking about using the CN in their cert which will have the BU name, but ISE 2.2 is not allowing that as a condition.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2018 04:36 AM
Assuming this is a Cisco or Meraki wireless environment, in my opinion you should always build your wireless policy sets using the RADIUS called station ID attribute coming from the controllers. The called station ID contains the SSID name the user is connecting to and allows you to create discreet policy sets per SSID use case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2018 05:10 AM
Morning Paul. It is a Cisco wireless/wired environment. I should've been more clear in my original post, but the idea is to differentiate users based on BU, even if they connect to the same SSID or switch. We're going to have another discussion around that tomorrow. As I keep thinking about it, it seems like an unnecessary level of granularity to begin with, but in the event they want to move forward with such a thing, any other ideas to differentiate?
I can't separate based on NAD, SSID, cert(when choosing a policy set. I can in the authorization rules of an individual policy set of course), or even user device name... Makes things difficult. It may end up coming down to single policy set for wired/wireless .1x and using authz policy to differentiate based on cert CN...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2018 03:49 PM
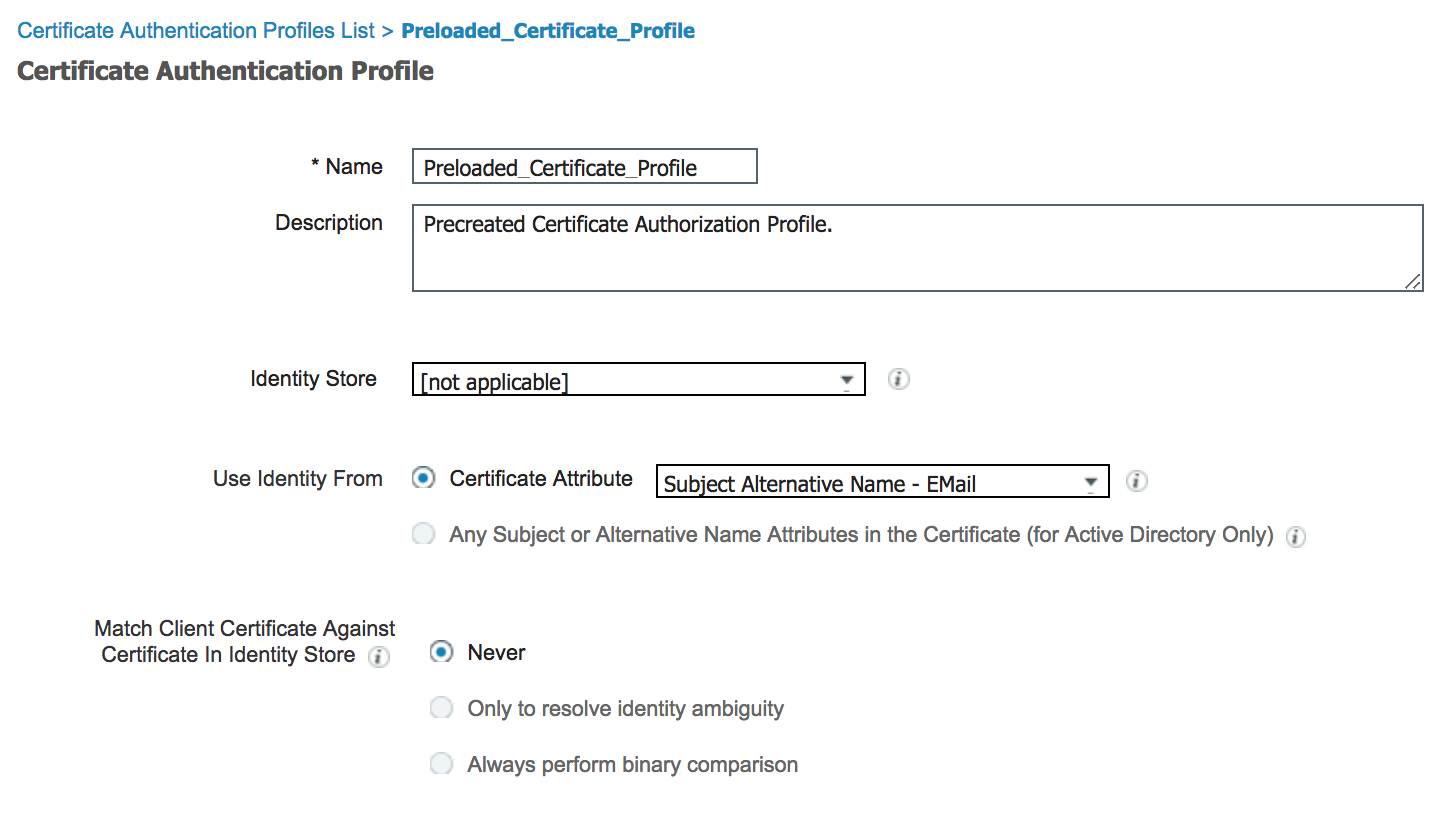
If you have the domain name in the CN / SAN / SAN - Email field of the certificate, then you can set that as the source of the user identity in the certificate template and then use it the policy set for high level classification. Try this:
RADIUS: COA received from id 8 172.20.254.4:59599, CoA Request, len 158 RADIUS/ENCODE(00000000):Orig. component type = Invalid RADIUS(00000000): sending RADIUS(00000000): Send CoA Ack Response to 172.20.254.4:59599 id 8, len 217 RADIUS: authenticator 26 83 79 8C 60 CA 00 42—2D F7 C3 74 AF 4A BC 92 RADIUS: Framed-IP-Address [8] 6 172.20.200.3 RADIUS: Vendor, Cisco [26] 20 RADIUS: Cisco AVpair [1] 14 "method=dot1x" RADIUS: Vendor, Cisco [26] 49 RADIUS: Cisco AVpair [1] 43 "audit-session-id=AC14FE6500000FCC0A83BF62" RADIUS: User-Name [1] 20 "employee1@isedemo.lab" RADIUS: Vendor, Cisco [26] 19 RADIUS: Cisco AVpair [1] 13 "vlan-id=200" RADIUS: NAS-Port [5] 6 60000 RADIUS: NAS-Port-Id [87] 22 "GigabitEthernet1/0/1" RADIUS: NAS-Port-Type [61] 6 Ethernet [15] RADIUS: Vendor, Cisco [26] 9 RADIUS: ssg-command-code [252] 3 RADIUS: 04 RADIUS: Calling-Station-Id [31] 16 "7011.248d.4b7f" RADIUS: Dynamic-Author-Error[101] 6 Success [200] RADIUS: Message-Authenticato[80] 18 RADIUS: 0B 77 48 92 9B 67 5E D7 AB 1B 06 2B 50 43 88 EE [ wHg^+PC] |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 12:44 PM
It would need to based on whatever incoming RADIUS attributes or authentication material (user@domain or certificate attributes) that you have like Hari showed above.
Typically you get BU/Department groupings from AD policy after the authentication, not before.
So unless you have some kind of departmental identifier there is no way for ISE to know how to handle the request per BU.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 04:33 PM
1. If there is a clear way of differentiating the network devices in different BU’s and they are using same ISE deployment, it is easy to use Network Device Groups in Policy sets to differentiate BU’s.
2. If you have AD for authentication and these BU have different domains, then use can differentiate based on domain name in the policy set. I have seen AD join point as attributes in policy sets in ISE.
3. You can also use RADIUS attributes Policy set.
Suggestion is to identify what is the best and easy way to identify the BU and use it.
If you have an ISE server, take a look at the policy set conditions and you will get an idea about the attributes.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide