- Cisco Community
- Technology and Support
- Security
- Network Access Control
- RADIUS server and 802.1x on switch Cisco Packet Tracer
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RADIUS server and 802.1x on switch Cisco Packet Tracer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2024 11:20 PM
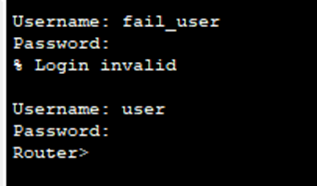
Good afternoon, Cisco community. I faced a problem when configuring RADIUS server using switch as authenticator. When using router everything was not complicated and worked, example below.
But my supervisor said that it is wrong to do it this way and in modern networks it is necessary to do authentication on switch. And that's where the problems started.
Immediately a question on topology, is a router needed if a switch is used to connect to a RADIUS server? What will change from this?
About configuring the switch. I did the following commands:
Interface vlan 1
No shutdown
Ip address 192.168.1.253 255.255.255.255.0
Exit
(ip default-gateway 192.168.1.254) #if a router is still needed in the topology
Interface range Fastethernet 0/1 - 24
Switchport mode access
Switchport access vlan 1
With these settings everything still works (you can ping the router from PC2)
Now on to configuring the aaa itself on the switch.
Here are the commands I used:
Aaa new-model
Radius-server host 192.168.88.8 key cisco
aaa authentication dot1x default group radius
dot1x system-auth-control
exit
interface range fastethernet 0/23 – 24
authentication port-control auto
dot1x pae authenticator
exit
copy run startup-config
I then added user data (user: root, password: root) to computers 1 and 2, which are connected to ports 23 and 24 respectively. And after that they become unavailable at all, orange. Although it seems that if 802.1x is enabled on them and user data has been added, then the port should allow the computer in question into the network. You can see this in the picture below
Configuring 802.1x on a computer
RADIUS server settings (Services - Radius EAP - EAP-MD5 enable):
Which default gateway should I specify for the router or switch? (And if there is no router in the topology, what should I do?)
Also a question what default Gateway to specify in the computer settings if there should be no router in the topology?
Thank you very much in advance, I hope you can help me!
P.S. as I have already dug through a lot of cisco documentation and not only, but everything does not work. When configuring 802.1x on the router there were no such problems and everything worked almost immediately.
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2024 11:56 PM
- FYI : Community group for Packet Tracer project questions
M.
-- Let everything happen to you
Beauty and terror
Just keep going
No feeling is final
Reiner Maria Rilke (1899)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2024 12:54 AM
I'm sorry. I wrote where you indicated, but I want to believe that someone here can help with this problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2024 01:37 AM
Couple of things here:
1) You would need the router if there is no direct comms between the switch and the RADIUS server. For instance, if the switch needs to route the RADIUS packets out of the interface 192.168.1.253, then yes the router is needed because the traffic flow would go this way Switch (192.168.1.253) > Router (192.168.1.254) > Router (192.168.88.2) > RADIUS Server (192.168.88.8), and it should return via the same path.
2) On the server configs it is showing the 192.168.1.254 as its default gateway? that should be adjusted to be the 192.168.88.2 which is the router interface in the same VLAN as the server interface.
3) The dot1x config on the PC it is showing MD5 as the authentication type? I think that should be changed to be EAP-PEAP which will rely on username and password for authentication.
4) The RADIUS port shown on the server configs is 1645, maybe the switch is using port 1812?, you can either set the port on the switch config to be port 1812 or change the port on the server configs to be 1812.
5) The dot1x config you shared seems to be minimum and I think you need to add more commands, please use the below template, maybe not all commands will be supported on PT.
aaa new-model
dot1x system-auth-control
aaa authentication dot1x default group < group name >
aaa authorization network default group < group name >
aaa accounting dot1x default start-stop group < group name >
radius server < server name >
address ipv4 x.x.x.x auth-port 1645 acct-port 1646 (you can use the 1812 and 1813 if you change them on the server config in PT)
key xxxxx
radius-server dead-criteria time 5 tries 3
radius-server deadtime 3
aaa group server radius < group name >
server name < server name >
ip radius source-interface Vlan1
radius-server vsa send authentication
radius-server vsa send accounting
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
interface < interface ID >
switchport mode access
authentication host-mode multi-auth
authentication order dot 1x mab
authentication priority dot1x mab
authentication event fail action next-method
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
mab
dot1x pae authenticator
authentication event server dead action authorize vlan xx
authentication event server dead action authorize voice
authentication event server alive action reinitialize
spanning-tree portfast
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2024 03:35 AM
About the first point, there is a direct link between the server and the switch. That is, I should specify the ip address 192.168.1.253 through vlan 1 and specify it as a client to the RADIUS server, and then the router won't be needed, right?
3) in CPT you can't select any other authentication type than MD5, in the YouTube example of similar work it was also used https://www.youtube.com/watch?v=8SlbCPFgVhY.
4)I will check this solution, but in the video above nothing changed either.
5) I need to make the simplest authentication, could you give me an example of a simplified version of your configuration like mine, thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2024 04:12 AM
On the topology you shared, the RADIUS server seems to be on subnet 192.168.88.x and the switch Vlan1 interface is on 192.168.1.x, hence I'd thought the are not on the same subnet.
The configs I pasted was taken from a template I have, I would try to apply all the commands, I wouldn't worry much if any of the advance commands wouldn't be supported by PT, for instance the RADIUS VSA, attributes, dead server detection, those wouldn't be essentials in your case.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide