- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Routers/switch to ISE/Okta for MFA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2020 09:45 AM
Looking at changing our router/switch environment to use MFA with ISE/Okta. Trying to find any information on this hasn't turned up much.
I am assuming i need to change the AAA to use Radius, but unsure how to go about the rest. Right now with ISE when you login it is using AD to authenticate you, then based on AD group assignment you are given access.
Solved! Go to Solution.
- Labels:
-
AAA
-
Identity Services Engine (ISE)
-
MFA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2020 08:09 PM
We ended up reusing the same config we had on the router/switches using TACACS and Cisco ISE. The only thing we changed on the devices was the timeout to 60 seconds. Then in ISE we created a Radius Token server that pointed to Okta, there was an option that we had to check to not reauth or something. Then we changed the device admin policy to use the Okta server for authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2020 05:34 PM
Currently SAML based authentication with Identity Providers (IdPs) is only available for web portal single sign on (device registration, sponsor), not 802.1X authentication.
You would want to consider doing RADIUS proxy instead.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2020 09:56 AM
@thomas wrote:Currently SAML based authentication with Identity Providers (IdPs) is only available for web portal single sign on (device registration, sponsor), not 802.1X authentication.
You would want to consider doing RADIUS proxy instead.
That is what I was looking at doing. Just wanted to know if anyone has set this up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2020 06:11 PM
I am in process of getting this to work. I got it to work using the authentication piece. We use the Radius Agent and then use the Radius application in the cloud. It doesnt pass authorization though. SO if you you want the tfa with the username login you could say authorization NONE OR set it to local and mimick the account login with the username command with the privilege level set.
It works for that but OKTA does not send back the shell command. It will send back groups in OKTA but not the shell command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2020 06:15 PM
There is a reference in the Client IP for Vendor Specific but the only response is in the groups. If you know of a way to reference Cisco-AV-Pair = shell:priv-lvl=7 that would be awesome. I can get it to send group names back but not sure how I would reference that in aaa switch configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2020 08:09 PM
We ended up reusing the same config we had on the router/switches using TACACS and Cisco ISE. The only thing we changed on the devices was the timeout to 60 seconds. Then in ISE we created a Radius Token server that pointed to Okta, there was an option that we had to check to not reauth or something. Then we changed the device admin policy to use the Okta server for authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2020 07:20 AM
I figured as much that I would have to end up using our Clearpass as a tacacs solution using tfa to OKTA if I want to receive the shell response back. I was trying to eliminate complexity and figured OKTA has this Radius App and the solution should be like a Radius Server. Just frustrating that they dont support this option or have this in their scope. I did reach out to OKTA on this and they were basically saying that their product doesnt do this and was quickly trying to close my ticket. Thanks for your response.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2020 07:50 AM
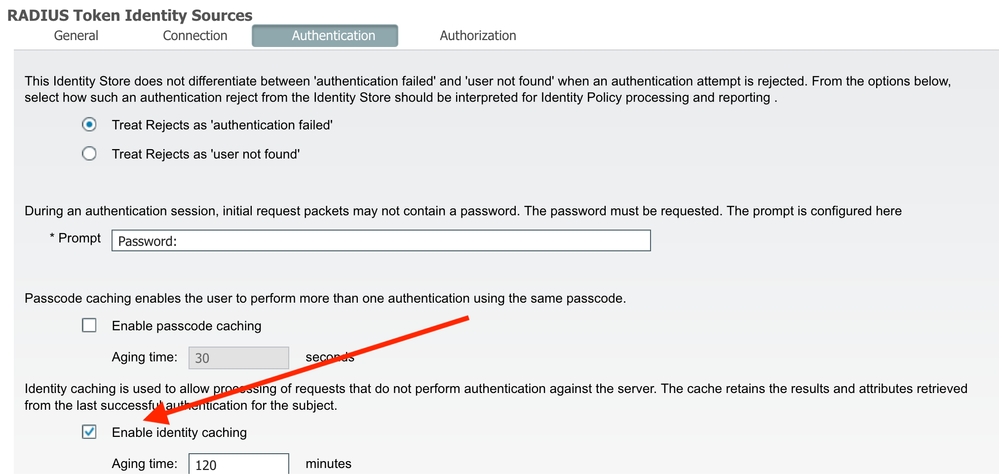
This is the setting
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2023 06:08 PM
I am working on this and have had some luck (specifically Cisco UCSM wouldn't work without the shell command). My fix was as follows
1) create an AD group called admin (lower case) Put your network admin AD accounts into this AD group. Force AD import into OKTA to seed this new group and membership
2) Under the OKTA RADIUS for AAA (or whatever you have named your app) click sign on. Go to Advanced RADIUS settings.
3) Edit - RADIUS attribute 26 Vendor-Specific, Vendor Specific ID = 009 and Attribute ID = 001
4) Group memberships to return (you should be able to search and find "admin"
5) Response format = repeating attributes
6) Group Name format = custom
7) shell:roles="${group.name}"
This method solved my UCSM issue. I have some A10 load balancers that don't give me priv 15 yet and when I compare my old RADIUS solution to OKTA I need to pass this (shell:priv-lvl=15) but am struggling with it so far. There are options for delimiter and how to respond and while I can see it in my wireshark trace and it looks right A10 device is not taking it. I have used this on Nexus, ISRs, MDS, ASA and just about every catalyst switch without issue so far though. One final thought you may find some devices that don't properly support OKTA push responses. Workaround is simple. Give it your OKTA username for user and okta password,okta.verify.tokencode all as the password. Works great on UCSM and Digi Console servers.
Hope this helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2024 09:49 AM
Hi Sir ,
Could you share the switch and ise policy setting?
My lab OKTA and ISE log all are allow , but switch still can't login
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2024 11:10 AM
Hi tzuyukuo31538,
I don't use ISE so I won't be much help on that front. As for sample router/switch config this is the basics.
We use custom port UDP 1650 for our RADIUS traffic (you can configure this in Okta App / admin dashboard)
aaa group server radius OKTA.RADIUS
server name OKTA.RADIUS.1
server name OKTA.RADIUS.2
aaa authentication login local_auth local-case
aaa authentication login OKTA.RADIUS group radius local-case
ip radius source-interface Vlan###
radius server OKTA.RADIUS.1
address ipv4 10.z.z.z auth-port 1650 acct-port 1651
key 7 ##################
!
radius server OKTA.RADIUS.2
address ipv4 10.x.x.x auth-port 1650 acct-port 1651
key 7 key 7 ##################
line vty 0 15
access-class 11 in
exec-timeout 15 0
login authentication OKTA.RADIUS
transport preferred ssh
transport input ssh
Hope this helps!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide