- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Sending specific VSAs on a successful authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Sending specific VSAs on a successful authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2019 06:18 PM
I am trying to get a Linux application A to interoperate with an instance of Cisco's ISE 2.3. A will interact with the ISE through the RADIUS protocol - in essence, A will send a username, password pair (U, P) to the ISE, so the ISE can carry out authentication chores on this pair. When the authentication succeeds, A expects the Authentication-Accept RADIUS message from the ISE, plus a number of VSAs with appropriate values assigned to them.
I have successfully added a RADIUS dictionary to the ISE, containing the definition of the VSAs that I am going to use. With the Identity Management -> Identities -> Users -> Add I have added a number of users that the ISE can authenticate as expected - I have been through the tasks required to accomplish this, but that has no bearing on my question.
Then, with Identity Management -> Settings -> User Custom Attributes I was able to add the VSAs that I am interested in.
After this, I went back to Identity Management -> Identities -> Users, clicked on one of the users I created, and the User Attributes foldout allowed me to add VSAs that I defined above, together with specific values for those attributes.
I next tried to perform an authentication from a Linux system by means of the radtest command, as follows:
# radtest -x -t pap mike AtISE2.3 192.168.124.57 1812 ISE2.3Secret
This generates the following output:
Sent Access-Request Id 49 from 0.0.0.0:53852 to 192.168.124.57:1812 length 74
User-Name = "mike"
User-Password = "AtISE2.3"
NAS-IP-Address = 192.168.123.66
NAS-Port = 1812
Message-Authenticator = 0x00
Cleartext-Password = "AtISE2.3"
Received Access-Accept Id 49 from 192.168.124.57:1812 to 0.0.0.0:0 length 187
User-Name = "mike"
State = 0x52656175746853657373696f6e3a6330613837633339744635666b643268344754714b4671726131556172464a4b454644346e614a6b6a2f646f56756470596159
Class = 0x434143533a6330613837633339744635666b643268344754714b4671726131556172464a4b454644346e614a6b6a2f646f567564705961593a69736532332f3336343237303432322f38
Message-Authenticator = 0x6dc49b450b8c6d0383646dc8026f8b26
The authentication succeeded - but no VSAs were sent back. When I do the same operation against an ACS 5.8 server, I get the following:
Sent Access-Request Id 39 from 0.0.0.0:42405 to 192.168.124.58:1812 length 80
User-Name = "atacsalone"
User-Password = "AtACS5.*"
NAS-IP-Address = 192.168.123.66
NAS-Port = 1812
Message-Authenticator = 0x00
Cleartext-Password = "AtACS5.*"
Received Access-Accept Id 39 from 192.168.124.58:1812 to 0.0.0.0:0 length 113
User-Name = "atacsalone"
Class = 0x434143533a61637335382f3336343031313139342f3138
Message-Authenticator = 0xdff9ea8cd8c9e3f4b34d1f8308a734a7
MyAttributeOne = "ValueOne"
MyAttributeTwo = "ValueTwo"
The ACS 5.8 is sending back two of my VSAs, as expected.
Any suggestions on how to configure the ISE 2.3 system so that it sends back my VSAs on a successful authentication, just like the ACS 5.8 does?
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2019 06:50 PM
You need to create an authorization profile that will send the VSAs you want. At the bottom of the authorization profile configuration screen, you should see an area for advanced attributes. Hit the drop-down and select the VSA you want to send. Then on the right side, select Internal User->Attribute 1 for example. When the authentication request matches on a specific authorization rule in ISE, ISE will respond with the authorization profile that you configured. It will send back the VSAs with whatever mapped attributes you configured.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2019 08:20 PM
Thanks for your feedback. I do have an authorization profile. Under Advanced Attributes settings there are two boxes, and two downward-pointing arrows, one in the left box, the other immediately below it. When I click on the first arrow, I get a pop up with the title Dictionaries, that enables me the attribute that I want. When doing so, the left box is filled out with something like the following:
MyVendorID:MyAttribute1
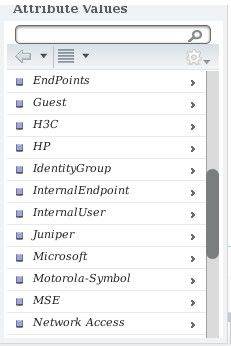
When I click on the second arrow I get another popup, this time with the title Attribute Values. However, the options I am getting are exactly the same as before. I end up with boxes looking as follows:
MyVendorID:MyAttribute1 = MyVendorID:MyAttribute1
which doesn't look right. In addition, I don't see Internal User (menu, or anything else) anywhere in this page - there is nothing to the right of the boxes. In case this is relevant, my browser is Firefox 68.2.0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2019 09:29 PM
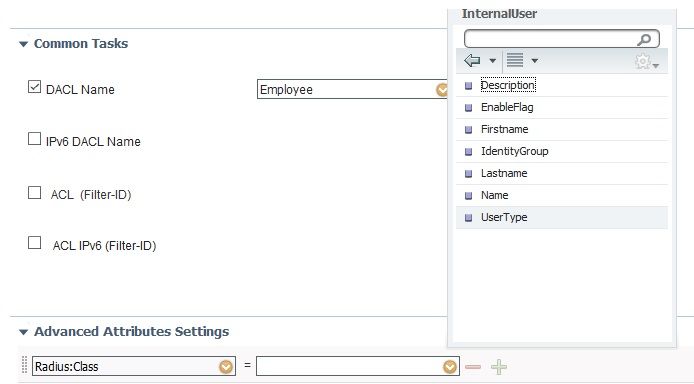
Try a different browser. I just tried it using the Radius::Class attribute as an example on the left. On the right, you get another menu and there is an "InternalUser" option as shown in the screenshot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2019 09:09 AM
Well, this is a bummer. I have tried several version of all the major browsers (Firefox, Chrome, IE) on the major platforms (Linux, Mac, Windows) and I keep getting the same behavior. I even tried older versions of Firefox, but the ISE's web interface would loudly complain when the version is too old - for example, Firefox 50.0.
No matter what I do, the InternalUser never shows up. Do you have to do anything in particular to elicit it? I mean, do you have to click on something, or is it supposed to be always there? I find it difficult to believe that all the browsers/platforms I have tried to use are not supported in exactly the same way - I must be doing something stupid, but I can't see what it is. Would you mind anyway sharing the details about the platform and browser that you are using?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2019 10:55 AM
I was using ISE 2.6 and Firefox 70.0.1. But I have done this also with Chrome, other browsers, and other versions of ISE.
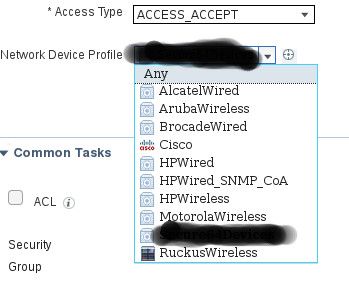
What about the Network Device Profile that you have selected for the authorization profile? Can you post a screenshot of what you see?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2019 12:34 PM
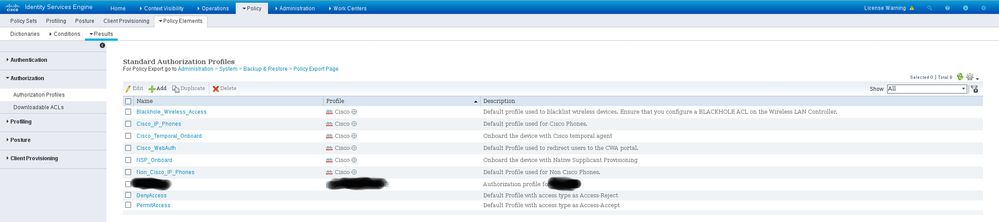
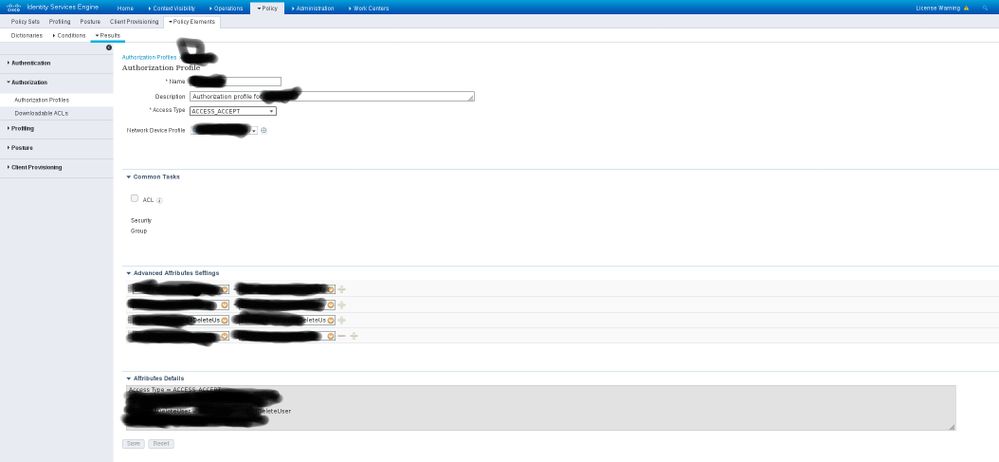
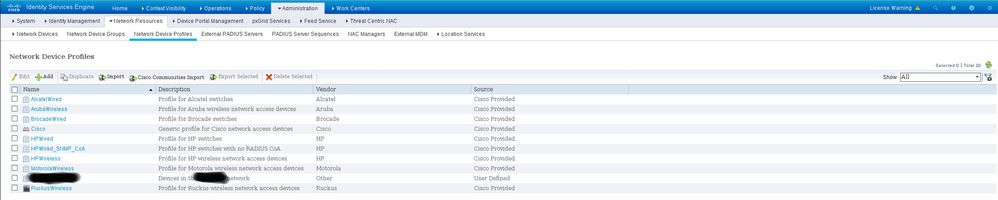
Check out the following screenshots - I have blacked out some names, for privacy reasons.
When I click in the target profile in the Authorization Profiles page (the blacked-out entry in the Auth Profiles screenshot) I get the page in the My Auth Profile screenshot. This illustrates what I described - no InternalUsers menu.
When I click in the target entry in the Network Device Profiles screenshot I get the My Network Device screenshot.
If having access to the blacked out names would help, I'll try to add ones that illustrate the same problem but that are not subject to privacy considerations.
Your feedback is much appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2019 01:18 PM
Looks like you do have access to the "Advanced Attribute Settings" in the authorization profile. So when you click the drop-down on the right side, you don't see anything other than your dictionary items?
Try adding the Radius::Class attribute on the left side and then see if you get the InternalUser option on the right. If you do, then it has something to do with how your dictionary attributes are created.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 12:25 PM
A bit of a breakthrough: when I click on the drop-down menu on the right side, this is what I am getting:
InternalUser is there all right! Thank you!
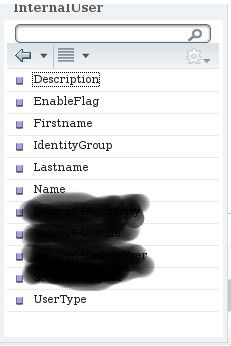
Now what I did next is to click on InternalUser, getting the following:
The blacked out stuff is the set names of the VSAs that I want to use. Let's assume that the first one is called Attribute1. If click on it, the right-hand-side box in the Advanced Attributes Setting ends with InternalUser:Attribute1. After saving these changes and attempting an authentication, I still get no VSAs from the ISE. I tried with other names, in the list above, to no avail. I am obviously missing a big ingredient here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2019 07:48 PM
Hi
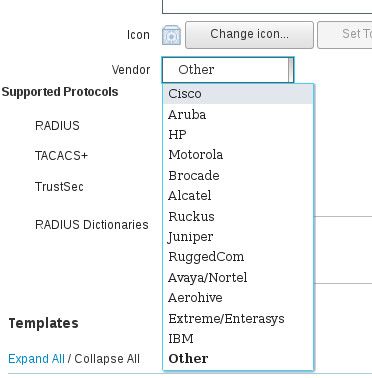
you have greyed out the Vendor field of the Authorization Profile. And in the Device Profile you have "Other" - the main thing is that the Device Profile and the Authorization Profile MUST use the same Vendor type (e.g. Cisco, or other, etc.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 12:48 PM
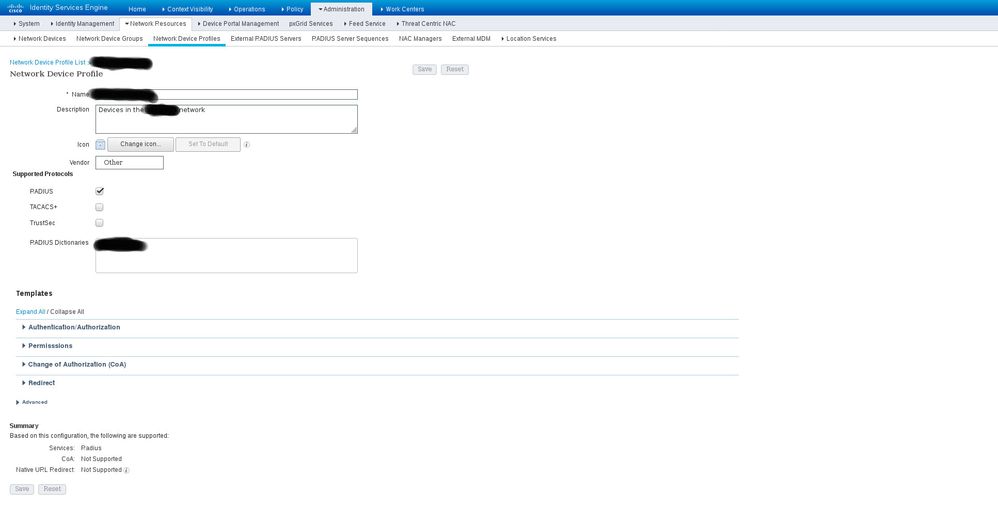
I am guessing you are talking about the second screenshot. By Vendor field you mean the Name field? I see no Vendor field anywhere, and I thought that the Name field contained just an otherwise arbitrary identification. In the Authorization Profile page I have the following:
where the name blacked out corresponds to the Network Device Profile I have defined. In the page for this network device profile I have the following:
Is this not right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 04:32 PM
Have you verified in the Live Logs that you are hitting the right authorization rule and that the authorization profile is applied? In the details of that Live Log entry, you can scroll down on the bottom-left and see what was sent back to the network device. If you see it there but the Linux server is not processing it, then that is a different issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2019 01:58 PM
Perhaps my terminology was not very precise. I was asking whether you were using the same Device Type in your Authorization Profile that relates to the NAS that is involved in the AAA request? If you have created a new Network Device Profile (e.g. called "BlackBox") then you will assign that to the NAS, as well as to any/all Authorization Profiles involved in the AAA. The only other allowed option is to leave the Authorization Profile's Network Device Profile as "Any" (i.e. no selection). But in general, if you mismatch the Network Device Profile (e.g. use "Cisco" for the NAS, and then use "BlackBox" in the AuthZ Profile), then ISE will play tricks on you.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide