- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Session Reauthentication in GUI results in CoA from PAN->PSN->NAD. Why?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Session Reauthentication in GUI results in CoA from PAN->PSN->NAD. Why?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2017 09:40 PM
Hi gurus
In my customer deployment I have configured and successfully tested Sponsored CWA using ISE 2.2p1 and Cisco WLC (Model 2504 running 8.2.151.0 code) - I checked the TCPdump in Wireshark and all the Message Authenticators are correct, after I discovered a bug in 8.2.110.0 where the WLC was sending CoA-ACK with the wrong authenticator. Good news is that 8.2.151.0 fixed that.
Then I tested a Session Re-authentication initiated from the GUI - and now I have questions ... :-) Why is the PAN suddenly involved ?
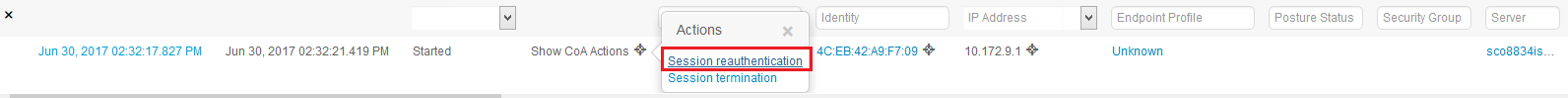
I would have thought that the CoA would go only from the relevant PSN to the NAD.
On a related note, does the PAN and PSN use an internal (undisclosed) Radius shared secret, that would cause the CoA-ACK to fail as shown below? I only know the Radius shared secret between PSN and WLC, and that is what Wireshark uses to calculate the authenticator.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2017 09:58 AM
I believe this is how it working when triggering CoA from the PPAN admin web UI.
It should use the RADIUS shared secret as configured in the NAD. If it's doing so, then it might be a bug. If you may give me the exact info how to recreate it, and if I am able to reproduce it in our lab, I can log a bug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2017 03:25 PM
Hi
Thanks for looking into this. I still don't understand the reasoning why a PAN sends radius CoA to a PSN? My pPAN has no Services configured.
I have a fully distributed deployment running ISE 2.2p1. My NAS is a Cisco WLC2054 running 8.2.151.0. I started a TCPDump on my PSN Gig0
I authenticate to a sponsored Guest portal. And then navigate to the PAN Operations->Live Sessions and choose Reauthenticate under the CoA Actions icon.
Load the .pcap into Wireshark (I used Windows ver 2.2.7) and configure your NAS's shared secret into Wireshark
Edit -> Preferences
Protocols / Radius

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2017 05:23 PM
I think it's done by design that the primary ISE node be the initiator to the CoA when requested at the live sessions. Is it causing you a particular concern?
Yeah, you are correct. I never thought about it before. During a proxy request, only the peers need the same shared secrets so that the one(s) between PPAN and PSN might as well differ from that between PSN and NAD. PPAN needs not serve session services as it acts a RADIUS client but not a server in the CoA requests.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

