- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Tacacs + for F5 using Cisco ISE 2.4
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 12:55 AM
Guys,
Can i have have any proper document detailing how to integrate F5 to Cisco ISE for Tacacs + ..
Regards
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 04:19 AM
The job in ISE is fairly straightforward and mostly always the same. It's nice that Cisco put some defaults into ISE for IOS-style devices and nexus and WLC. But for everything else, your're going to have to RTFM of the 3rd party vendor's product.
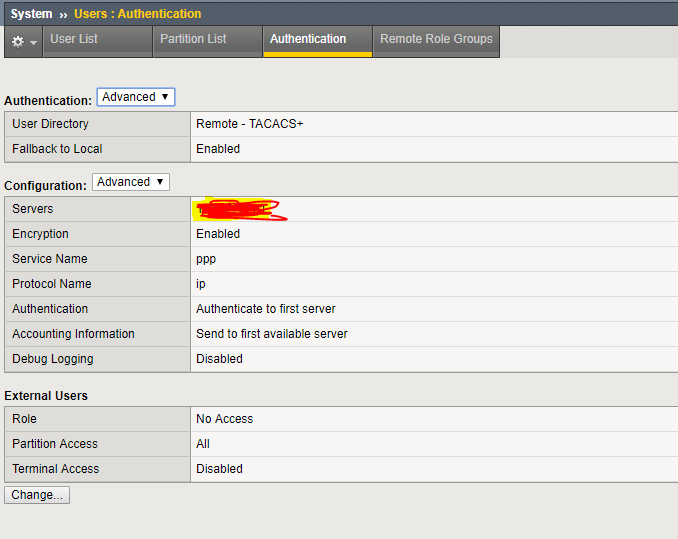
If you read further down the F5 page you will see that you need to assign roles to the F5 when it performs TACACS authorization requests to ISE. In ISE this would mean, specifying the Profile as "custom" and then pasting the values in.
The same thing happens for Cisco Prime Infrastructure - if you read the documentation, then it will tell you all the lines of data you need to paste in when you assign a role of Full Admin, Read-Only Admin, etc. I think F5 is similar, because it's not like IOS at all (that is, there is no concept of shell level 0-15)
Having said all that, it would be handy if someone could paste some examples of how they did it, just to help clarify.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2019 11:43 AM
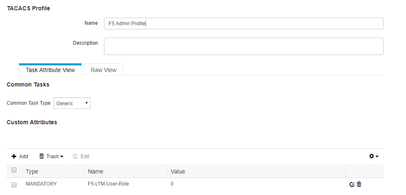
its simple .
create below F5 profile in ISE :
for different user role pass the different user role value and then create Remote user role group in F5 to call this .Make sure to select the fallback to admin in TACACS on F5 to make sure we dont lock ourself out .
Hope it helps .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 04:19 AM
The job in ISE is fairly straightforward and mostly always the same. It's nice that Cisco put some defaults into ISE for IOS-style devices and nexus and WLC. But for everything else, your're going to have to RTFM of the 3rd party vendor's product.
If you read further down the F5 page you will see that you need to assign roles to the F5 when it performs TACACS authorization requests to ISE. In ISE this would mean, specifying the Profile as "custom" and then pasting the values in.
The same thing happens for Cisco Prime Infrastructure - if you read the documentation, then it will tell you all the lines of data you need to paste in when you assign a role of Full Admin, Read-Only Admin, etc. I think F5 is similar, because it's not like IOS at all (that is, there is no concept of shell level 0-15)
Having said all that, it would be handy if someone could paste some examples of how they did it, just to help clarify.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2019 11:43 AM
its simple .
create below F5 profile in ISE :
for different user role pass the different user role value and then create Remote user role group in F5 to call this .Make sure to select the fallback to admin in TACACS on F5 to make sure we dont lock ourself out .
Hope it helps .
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide