- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Tying a Client Certificate to One Endpoint in ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2019 12:48 PM - edited 02-21-2020 11:10 AM
Is there a way to tie a user's client certificate (EAP-TLS authentication) to one endpoint? I'm looking to authenticate based on clients having the proper certificate but don't want them to be able to take that certificate, install it on another device, and authenticate onto our network? Anyone have any tips on this? TAC told me I can limit the number of concurrent sessions a user can have at once but didn't seem to have an answer on a configurable policy that ties one cert to one endpoint.
Thanks!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2019 12:55 PM
When you issue a certificate, you can specify that it is not exportable. So in that case, the user would not have the ability to export the certificate off of the machine. If it is a machine certificate, you can also try to issue it with the MAC address of the device in a SAN attribute. Then on ISE, you can make sure the SAN value matches the calling-station-id (MAC address). What are you using as a CA to issue certificates? Are these machine certificates or user certificates?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2019 12:55 PM
When you issue a certificate, you can specify that it is not exportable. So in that case, the user would not have the ability to export the certificate off of the machine. If it is a machine certificate, you can also try to issue it with the MAC address of the device in a SAN attribute. Then on ISE, you can make sure the SAN value matches the calling-station-id (MAC address). What are you using as a CA to issue certificates? Are these machine certificates or user certificates?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2019 01:20 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2019 01:27 PM
There are a number of ways to do it. One is using the Web Enrollment feature for MS CA servers. A user goes to a particular web URL to enroll and get a certificate. For MACs, one of my previous customers used AirWatch to enroll machines and users for certificates. There is also the manual enrollment where you generate the CSR on the Linux machine using openssl, send the CSR to the CA administrator, they sign it and return the public key, then bind the two on the Linux machine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2019 01:34 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2019 08:04 AM
Not sure how to implement the latter yet, but the former is pretty simple. I'll just need a way to utilize OSCP for revocation and something else for expiration. Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
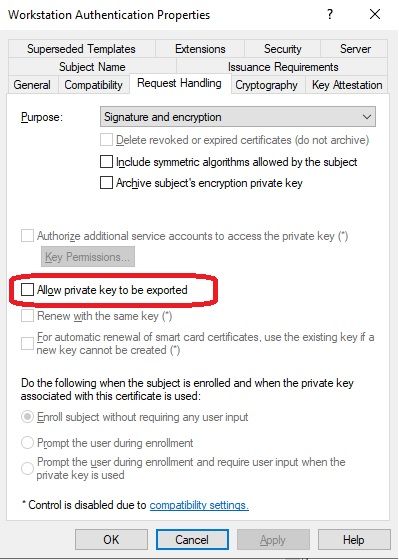
10-08-2019 01:13 PM
Here is a screenshot showing the certificate template configuration for a computer certificate. Similar options would be available in the user certificate template. The option to allow the private key to be exported is what you want to make sure is not allowed. This is on a Windows 2019 1809 Certificate Server. Your options may be worded differently.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide