- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Understanding Authorization Profiles
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2021 09:20 AM
I have a customer solution that has an authorization profile to allow users who register their details access to the internet with their personal devices.
The attached screenshots show the policy works but I can't understand how.
there are no users in the identity group used in the profile.
The users registers via an internal website that communicates with ISE via REST API.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2021 03:16 PM - edited 06-27-2021 03:16 PM
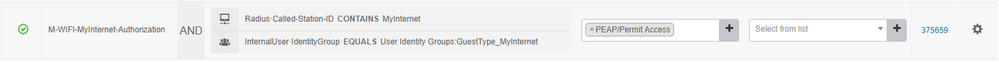
This is your Policy Authorization Rule from your picture:
First condition matches on your SSID containing "MyInternet"
Second condition matches any ISE internal users in the group GuestType_MyInternet.
From your explanation, it sounds like you are adding guest users' Username and Password via REST API to the ISE internal identity group GuestType_MyInternet. This allows them to authenticate to SSID MyInternet so they can connect securely with PEAP rather than an open, unencrypted SSID. I figured this because even though you did not show your authentication policy, you named your Authorization Result "PEAP/PermitAccess".
To find out exactly Why it is working, simply look at the ISE LiveLogs and click on the
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2021 03:11 PM
In this case internal users creates on the internal website and during the time of authentication which will push to ise using API. its like an automated process.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2021 03:16 PM - edited 06-27-2021 03:16 PM
This is your Policy Authorization Rule from your picture:
First condition matches on your SSID containing "MyInternet"
Second condition matches any ISE internal users in the group GuestType_MyInternet.
From your explanation, it sounds like you are adding guest users' Username and Password via REST API to the ISE internal identity group GuestType_MyInternet. This allows them to authenticate to SSID MyInternet so they can connect securely with PEAP rather than an open, unencrypted SSID. I figured this because even though you did not show your authentication policy, you named your Authorization Result "PEAP/PermitAccess".
To find out exactly Why it is working, simply look at the ISE LiveLogs and click on the
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2021 12:35 AM
Thomas
Thanks for the reply. I did look at the logs. It states it matched against the conditions in the screenshot. The point of my post was that when you look in the internal identity GuestType_MyInternet there are no entries as seen in the second screenshot. So how is it matching?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide