- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Using Windows NPS for Cisco router aaa authentication - is this safe?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2015 08:52 AM - edited 03-10-2019 10:29 PM
I'm very confused about how all this works and was hoping someone could help me out.
I followed a bunch of online tutorials to setup RADIUS authentication on a Cisco router and pointed it to a Windows NPS. I can now ssh into the router my with AD account.
Now that I got it working I'm going over the settings to make sure everything is secure.
On my router the config is pretty simple:
aaa new-model
aaa group server radius WINDOWS_NPS
server-private 123.123.123.123 auth-port 1812 acct-port 1813 key mykey
aaa authentication login default local group WINDOWS_NPS
ip domain-name MyDom
crypto key generate rsa
(under vty and console)# login authentication default
On the Windows NPS:
- I created a new RADIUS client for the router.
- Created a shared secret and specified Cisco as Vendor Name.
- Created a new Network Policy with my desired conditions.
- And now the part of the Network Policy config that worries me:
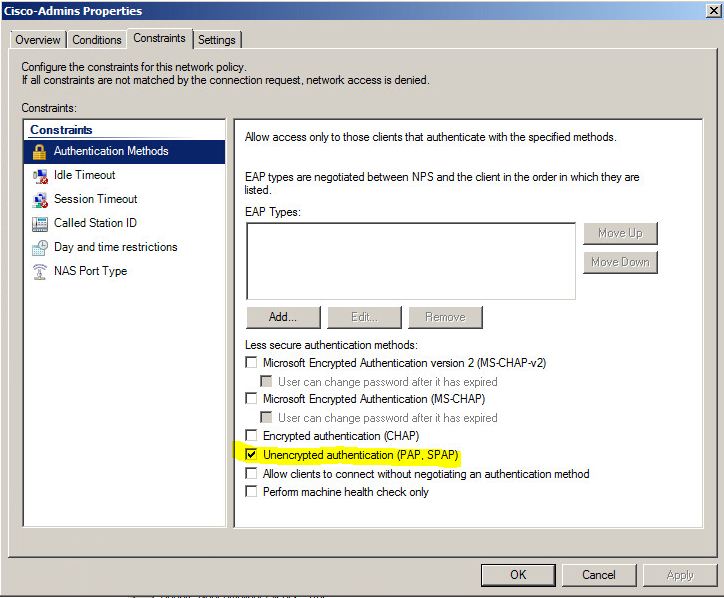
So initially I thought my AD credentials were being sent over the wire in plain text, but I did a capture and saw this:

How is my password being encrypted and how strong is the encryption?
Another thing is how can I configure aaa authentication with mschapv2? The documentation I saw for mschapv2 uses the "ppp authentication ms-chap-v2" command, but I'm not using ppp I'm using aaa with a radius server.
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2015 07:42 PM
Hi,
Radius encrypts the password but sends the user name in the clear. Tacacs encrypts both username and password.
You can find the encryption scheme used by Radius in the RFC:
https://tools.ietf.org/html/rfc2865#page-27
MS-Chap-V2 is used for user authentication like dial-in and vpn and not for switch management
Thanks
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2015 07:42 PM
Hi,
Radius encrypts the password but sends the user name in the clear. Tacacs encrypts both username and password.
You can find the encryption scheme used by Radius in the RFC:
https://tools.ietf.org/html/rfc2865#page-27
MS-Chap-V2 is used for user authentication like dial-in and vpn and not for switch management
Thanks
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2015 06:20 AM
Ok i think that clears it up. I looked at the RFC and guess RADIU just uses MD5 which is perfectly fine. But I have one more question: if a preshared radius key gets compromised I need to reissue a new key to all my clients correct? If a hacker knew the key they could decrypt the traffic right?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide