- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Wireless MAB Authentication to AD/LDAP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2016 04:37 PM
I have a customer that has an SSID configured for MAC filtering pointing at ACS 4.2. The MAC addresses are objects in AD. The MAC addresses are entered into AD in the format of "fcc2de8195a3", If I configure a policy set in ISE for this SSID to go against AD, but ISE always tries to use fc:c2:de:81:95:a3 as the User ID. I even tried using LDAP and set MAC lookup to XXXXXXXXXXXX.
If I looked at the detailed logs I can see this:
OriginalUserName fcc2de8195a3
So the username is there in the correct format, but it looks like is using the username is set to:
Username FC:C2:DE:81:95:A3
I assuming since ACS 4.2 was able to do this without an issue there must be a way to have ISE do it.
What am I missing?
Thanks.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2016 04:43 AM
This is certainly possible with ISE, but not recommended as you have to create AD DB with username of MAC address and also password of MAC address (Password has to be lower case). In the past this was used as backdoor to network access when the RADIUS server was not properly configured. As you can imagine if the RADIUS server was not configured properly a user can enter MAC address as username and password and gain network access or Windows domain access. ACS 4.x was first version to move away from using username & password and started using Calling-Station-ID (CID) field for MAC addresses instead. Since then ACS 5.x and ISE all defaults to using CID though you can change it to process username and password like it used to. To change the behavior on ISE you need to create a new ‘Allowed Protocols’ and uncheck ‘Process Host Lookup’. Here I’ve created one called ACS4MAB.

This essentially tells ISE to look for username & password from the MAB request without using the CID. Once custom allowed protocol has been created apply it to Authentication rule within the policy set.
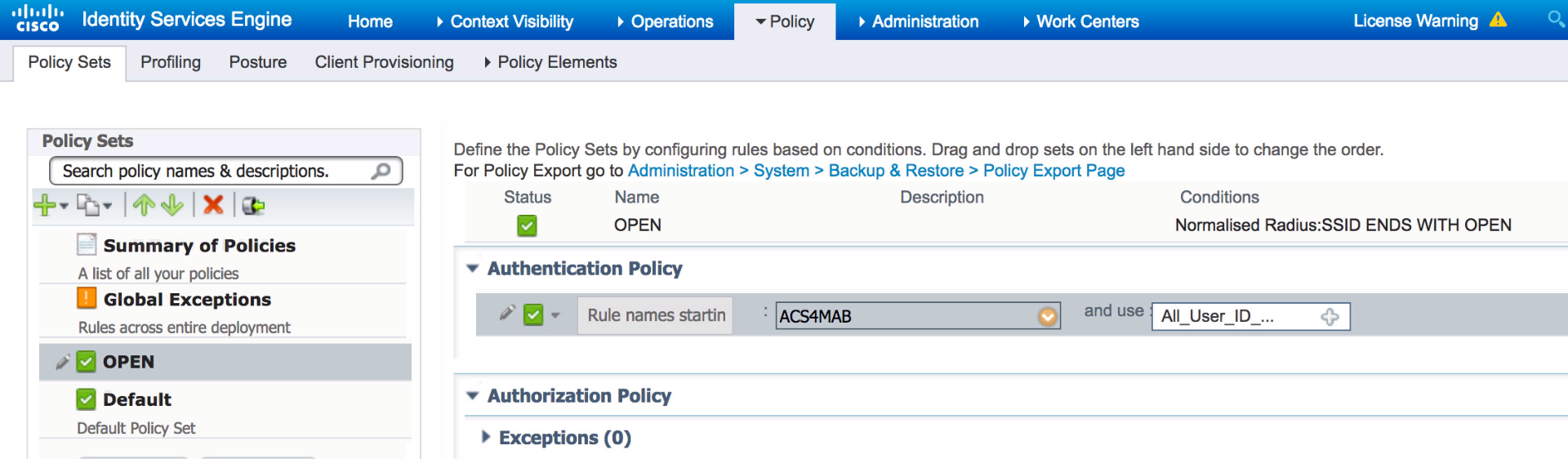
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2016 06:01 PM
It should not matter which MAC format used, as ISE able to normalize it for comparison. Could you please give more details of the failure? Else, please engage Cisco TAC to help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2016 11:15 PM
Here you can see the failure details in the attached screen shots and the fact that if I remove the colons or hyphens the AD lookup works just fine. You can also see the WISM is passing the username without any colons or hyphens as referred to in the OriginalUsername field in the screen shots.
Paul Haferman
Office- 920.996.3011
Cell- 920.284.9250
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2016 06:59 AM
Please check the configuration on the WiSM for MAC Delimiter. Also, perform a TCPDUMP/wireshark capture the RADIUS auth exchanges between ISE and WiSM to confirm the user name field.
One of our WLCs have Hyphen as the MAC Delimiter but the OriginalUserName has no delimiter.
If that does not give any clue, please detail how the AD records for MAC addresses are constructed so I will try a recreate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2016 07:37 AM
There are two spots in the WLC to control how the MAC is presented to the RADIUS server. Here are the screen shots of what is currently working with ACS 4.2 The first spot is in the RADIUS server definition and I believe controls the format contained in the RADIUS called station ID. This is currently setup as Hyphen.
The second spot is in the MAC filtering section which controls the username format and password. This is set to none which is why I believe you see the OriginalUsername attribute in ISE detailed record showing no delimiters:
You can see in the attached screen shots from the ISE AD lookup test on the external identity screen all the attributes. ISE is able to easily find the MAC address if I remove the delimiters. Here are the screen shots again.
I can try to get a packet capture of the authentication.
Paul Haferman
Office- 920.996.3011
Cell- 920.284.9250
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2016 11:44 PM
Please try connecting to your AD as LDAP, following the procedures here --> LDAP MAC Address Lookup
ISE allow us to select the MAC address search format in a LDAP ID source but not in an AD source.
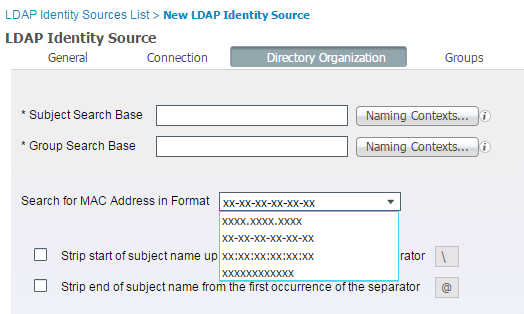
Besides, the "Identity Rewrite" feature in AD is not supporting it, as seen in this enhancement request -- CSCut92689 REQ: ISE1.3 support to rewrite a1-a2-a3-a4-a5-a6 to a1a2a3a4a5a6
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2016 04:43 AM
This is certainly possible with ISE, but not recommended as you have to create AD DB with username of MAC address and also password of MAC address (Password has to be lower case). In the past this was used as backdoor to network access when the RADIUS server was not properly configured. As you can imagine if the RADIUS server was not configured properly a user can enter MAC address as username and password and gain network access or Windows domain access. ACS 4.x was first version to move away from using username & password and started using Calling-Station-ID (CID) field for MAC addresses instead. Since then ACS 5.x and ISE all defaults to using CID though you can change it to process username and password like it used to. To change the behavior on ISE you need to create a new ‘Allowed Protocols’ and uncheck ‘Process Host Lookup’. Here I’ve created one called ACS4MAB.

This essentially tells ISE to look for username & password from the MAB request without using the CID. Once custom allowed protocol has been created apply it to Authentication rule within the policy set.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2016 07:34 AM
Our engineering team confirmed,
MAB is supported with Internal and LDAP – not AD.
Please do try connecting to your AD as a LDAP ID store and let us know whether that works for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2016 08:03 PM
I tested LDAP authentication before I posted this originally. We couldn’t get that working either. We are probably just going to create a static whitelist in ISE as we are migrating away from this SSID.
Paul Haferman
Office- 920.996.3011
Cell- 920.284.9250
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

