- Cisco Community
- Technology and Support
- Security
- Network Security
- Access Control Policy and Intrusion Policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2018 03:24 AM - edited 02-21-2020 07:29 AM
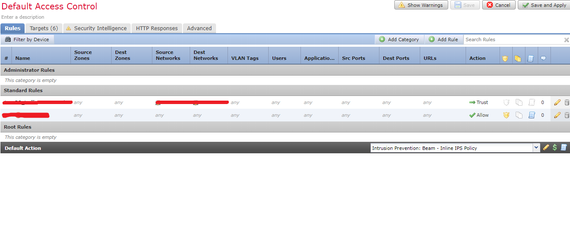
We are facing issue with intrusion policy that is not working as per the configuration. We have a intrusion policy in which multiple signature state are"Drop and Generate Events" and our base policy is "Balanced security and Connectivity". The the intrusion policy has been placed in access control policy, please see the below screenshot.
Please see below is one of the example,
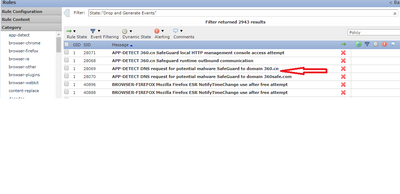
The signature state is in "Drop and generate" but while analysis the same intrusion events (triggered alert for that signature) the status is would has dropped. I guess this event should be drop and generate but here it seems is not dropping the connections. It would be great help if someone is give more clarification on this issue.
Note: issue is not only with single signature.
Thanks,
Susin.
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2018 06:52 AM
Hi Susin,
I am assuming you are talking about ASA-SFR module. If its in fail-open mode, than it means its supposed to drop traffic if configured to.
To answer your question, you don't need to change anything on managed device for this problem.
If the device is in promiscuous mode, it won't drop anything anyways.
Rate if helps,
Yogesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2018 09:52 AM
Hi Susin,
Basically the firepower was not able to take the decision in time and to avoid delay in processing, traffic was already passed on wire before it could decide the traffic needs to be dropped.
As this is the only rule that shows this behavior, it could be that the snort does not receive all the packets data from flow in time to determine the correct course of action.
I would suggest to enable inline normalization in network analysis policy to solve the problem.
usually this issue comes due to either of 3 reasons.
>Device is under heavy load
>Snort did not receive all the data to evaluate packet in time and flushed data to avoid latency
>The same traffic passed through firepower twice
Rate if helps,
Yogesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2018 07:22 PM
Thank you for your response.
Could you please confirm do we need to change any setting in Managed devices, as of now we didn't specify the inline or promiscuous mode but it in fail-open mode. Please advise this question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2018 06:52 AM
Hi Susin,
I am assuming you are talking about ASA-SFR module. If its in fail-open mode, than it means its supposed to drop traffic if configured to.
To answer your question, you don't need to change anything on managed device for this problem.
If the device is in promiscuous mode, it won't drop anything anyways.
Rate if helps,
Yogesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2018 09:37 AM
Hello Yogesh,
Thank you for your response.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide