- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Access Control Policy Blocking Sites targeting Active Directory Us
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Access Control Policy Blocking Sites targeting Active Directory Users
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2022 10:18 PM
Hi Everyone,
I got into this roadblock while implementing a blocking to specific websites like facebook, youtube and adult sites and i want to block only certain group of people by targeting their active directory users login.
i have already created Realms and imported users and groups from AD and it was running pretty smooth, even my RAVPN is getting authentication from it is running pretty well and i also created an Identity policy as the Access Control Policy requires me for it.
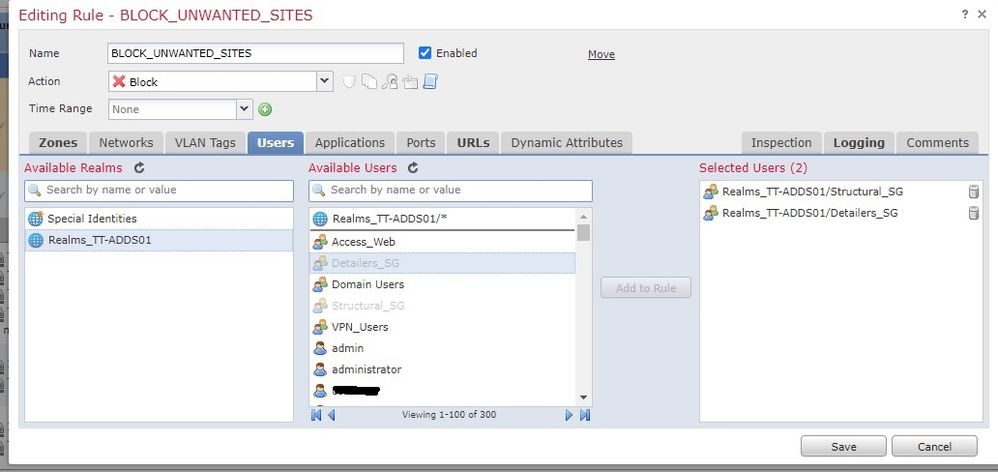
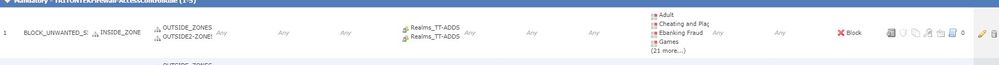
Now, i made a test block under ACP for any users any source and any destination with the specific urls and it worked well but when i tried to add specific users under USERS tab in my Policy all users can access the blocked URL's which is not what i expect i even added a single AD group or a single AD user it still can access those blocked url's,
I am using FTD7.0.1.1 and FMC 7.0.1.1 with ASA5508X
Here is a look on my ACP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2022 03:12 PM
You need to decide how you want to authenticate your users, if that is via ISE-PIC or directly with the AD. This is a design choice you need to make and based on that choice you will know if you need the ISE in the network.
As for traffic not hitting your rule, which are you using to authenticate users now? AD or ISE?
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2022 08:47 PM
in the documentation and even in the youtube tutorials, setting up ISE-PIC needs AD realms so i think both AD and ISE-PIC works together.
i also read some exchange conversation online that we need to run this command (user_map_query.pl -i 172.20.7.100) on both FMC and FTD to check if mapping is present. Upon running the command it shows that FMC is mapping the user correctly but not on the FTD and the possible workaround is syncing the database from FMC to FTD and requires a snort restart.
the problem is i dont know what is the command to do this workaround and is it safe to do this?
see results below:
in FMC:
WARNING: This script was not tested on this major version (7.0.1)! The results may be unexpected.
Current Time: 06/16/2022 06:19:51 UTC
Getting information on IP Address(es)...
___
IP #1: 172.20.7.100
---
==============================
| Database |
==============================
##) Username (ID)
1) hsison (1294)
for_policy: 1
Last Seen: Unknown
in FTD:
WARNING: This script was not tested on this major version (7.0.1)! The results may be unexpected.
Current Time: 06/16/2022 06:23:18 UTC
Getting information on IP Address(es)...
ERROR: Unable to find IP address '172.20.7.100' in the database!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2022 01:11 PM
I think you have misunderstood the setup. You integrate AD with ISE and then use ISE as and identity source in FMC.
With regard to mapping the users on the FTD that requires SNORT restart. Any time the SNORT process restarts there will be network outage until the process is back online. So this should be done in a planned service window
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2022 07:51 AM
Hi sir, you are right.
May i know how to map users in FTD? Is there a command or documentation for that? I can perform that during the weekend since that is the only time i can perform reboots.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2022 02:15 PM
Here is a document on integrating FMC with ISE
https://www.cisco.com/c/en/us/products/collateral/security/firepower-ngfw/guide-c07-742017.html
for other documents on FMC integrations you can go to the following link.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2022 10:43 PM
Hi Sir,
Finally the user mapping has been synched between the FTD and FMC by the help of a TAC engineer. What he did is he just added some scrip to a .conf file on the FTD and rebooted Snort and rebooted the FTD device itself then deleted the existing Identity Policy and recreated it then users are now showing in the events connection and also i can now block urls and categories using domain users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2022 11:27 PM
Nice!
Could you summarize the commands used to do this and post it here? This so that it might help someone else experiencing the same issue and will not need to open a TAC case to solve it.
Please remember to select a correct answer and rate helpful posts
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide