- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA 5506 site-to-site VPN failover
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5506 site-to-site VPN failover
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2023 11:57 AM
Hello,
I have 2 site-to-site VPN's configured on my ASA 5506-x. They are meant to be failover to each other. If one goes down, the traffic should go through the other one, and vise versa. However, I've noticed most of the times that one of the tunnels stop working, it doesn't go down; it actually stays up, but traffic won't go through it. So i was wondering what's the workaround for that? Should i configure some sort of SLA and then some route policy that would route over to the other tunnel if pings stop responding or something? could you please share an example? thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2023 12:07 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2023 12:46 PM
Thanks Flavio! do you know if that would work for site-to-site VPN failover? the failover i want to implement is not between 2 ISP's but 2 VPN's
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2023 01:27 PM
The SLA monitor should work dont matter if it is two ISP or not, as long as the destination is different. If your ISP is able to provide that fine, otherwise you probably will not have two Site to site vpn anyway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2023 12:25 PM
How many asa there ?
How many ISP for each ASA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2023 12:45 PM
The ASA has only 1 ISP, but it has 2 site-to-site VPN's. I'm intending for the failover to choose between the 2 VPN's rather than 2 ISP's
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2023 01:00 PM
Asa one ISP you can not config two s2s vpn to same destination.
One ISP one s2s vpn to one Peer.
If peer have two ISP then solution is
Crypto map mhm seq 10 set peer <isp1><isp2>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2023 01:31 PM
Thank you.
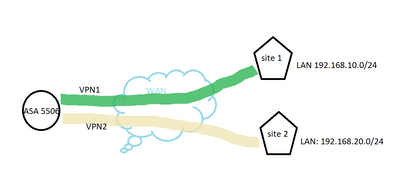
is one ASA with two site-to-site VPN to different peers. From the picture, essentially, i need resources on 192.168.20.0/24 to only be reachable when 192.168.10.0/24 are unreachable. If both circuits are up, 192.168.10.0/24 should take prefference.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2023 01:36 PM
But the lan behind peer is different
One 192.168.10.0 other 192.168.20.0 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2023 01:41 PM
Yes, they would be different
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2023 01:54 PM - edited 07-20-2023 01:54 PM
Your host behind asa connect 192.168.10.0' what if it need to connect 192.168.20.0?
What is the type of this traffic?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2023 06:51 AM
This is what dynamic routing over tunnels is for. But on ASA 5506, which can only run 9.16 and below, you cannot use EIGRP and OSPF over tunnel interfaces. You can only run BGP. IP SLA is also not supported (CSCvd52282).
Another drawback is that configuration should be reworked to use "interface tunnel" instead of vanilla crypto maps and your site-1/site-2 headend devices may not support this technology.
There is also not widely known possibility to run unicast OSPF over crypto maps, but this would require two physical interfaces on your ASA, one per tunnel. The other side must be ASA as well. Not good.
In general, for crypto maps, IPSec SA shouldn't stay up if there is no connectivity over it, because "isakmp keepalive threshold 10 retry 2" is ON by default for L2L. Also, if you have "crypto map <map name> <seq num> set reverse-route" configured, the route to 192.168.10/20.0 should be removed automatically when IPSec SA goes down. To prevent leaking of clear-text packets to the Internet you need to configure static routes to 192.168.10/20.0/24 via null0 with admin distance 250 and also your applications should be able to react to route loss by timeout (I don't believe ASA will send an unreachable when it routes to null0).
All-in-all ASA is not the best platform to use for L2L VPN, to say the least.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2023 07:24 AM
Hey TVotna thanks so muc for the detailed response! there's a lot there. So i'll read it more than twice and process it. Will get back to you soon. thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide