- Cisco Community
- Technology and Support
- Security
- Network Security
- I can't remember where (i
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5506-X - Switchports?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2015 03:52 PM - edited 03-11-2019 10:40 PM
Just got my hands on a new ASA 5506-X and immediately ran into an odd issue:
There are eight layer 3 ports that seemingly cannot be used as switch ports.
There is no bridge-group capability available either. (which, if present, could be used to resolve this issue)
Why does this device even have 8 ports if they cannot be used as switchports?
Is this going to be fixed in future software? (By adding bridge groups?)
Can anyone think of any other "clever" workarounds?
Between this issue and the lack of POE, this device seems to be significantly less useful than the ASA5505.
Thank you.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2016 09:32 AM
I'm going to be honest, I am a Cisco person, I have been drinking the Cisco Cool aid for years and years. When it comes to Cisco's ASA product offerings, I have become so disheartened by the lack of attention the SMB and medium sized business have been receiving. When I talked to the Cisco Security Products engineers at the world of solutions, and explained to them how lacking the 5506 is, they didn't even realize there was a business use case for the switch ports on a 5505. Cisco is focusing their efforts on the high end products and the people who really build their user communities are left out high and dry.
I started deploying A few PAlo Alto Firewalls, because the ASA is missing so much, and I've actually found myself happier. Licensing is a PAIN (more than Cisco), but once you get the hang of it, the licensing is a no brainer. I hate to say it, but the ASA is losing ground.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2018 08:03 PM
Couldn't agree more. ASA and Firepower are just terrible implementations in 2018. There might be some decent features, but the entire architecture and platform is a cobbled together piece of junk. I have zero patience and am not recommending ASA/FP/FMC to anyone until I see some actual real benefit.
I deployed a small Palo Alto unit (PA-220) and after the initial learning curve it was a joy. On top of that, I get L2 switch ports *with* L2-to-L2 (intranet) IPS inspection! I also get a TRUE separation of management interface and data plane interfaces without this weird kinda-separate management routing table mess. And don't even get me started on FTD.
I still like their routers, switches, and a few other products, but goodbye ASA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2016 03:08 AM
A replacement model shouldn't provide full configuration migration opportunity?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2016 10:09 AM
We purchased what we thought was a replacement for the 5505 and ran into this same problem. In the interest of installing a solution for the customer under time constraints, we ended up putting in an additional switch which added to the cost of the deployment. This forces us to consider other companies for future replacements. I hope Cisco reconsiders this poor decision.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2016 06:43 AM
I can't remember where (i think in this presentation http://ciscoclub.ru/novaya-integrirovannaya-platforma-bezopasnosti-firepower-4100-i-platforma-bezopasnosti-firepower-thr) it was said that Cisco plan to implement some sort of switchport in 5506 in some next release.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2016 10:34 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2017 09:58 PM
Cisco has just released ASA 9.7(1). Among the new features are the ability to configure ports in a bridge group. This should address the primary concern about the 5506-X vs. 5505.
The default configuration on new 5506-Xs will include interfaces in a bridge group. All other models will also be able to configured with this feature. It applies to both ASA appliances running ASA software as well as FTD software (release 6.2 in that case).
Please see the release notes here:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa97/release/notes/asarn97.html#ID-2172-00000128
(The PoE feature will not be forthcoming on the 5506-X.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2017 10:24 AM
It is now supported on versoin 9.7 !!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2017 07:01 AM
Hi everyone!
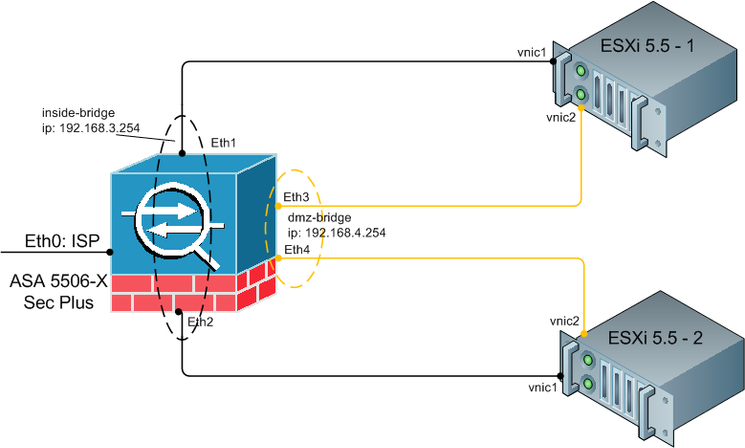
I'm going to purchase Cisco ASA 5506-X-K9 Sec Plus device. I have plans to build the following schema:
As you can see here are two VMWare ESXi servers connected to ASA5506-X firewall. vSwitch of each server has two vlans (vlan3 - inside area, vlan4 - DMZ). So I want to configure vlan trunks between ASA and VMWare. I need vlan trunks to save more ports of my VMWare server for another needs (SAN, redundacy links, additional servers interlinks and etc.).
Can anybody tell me is it possible on Cisco ASA5506-X?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2018 01:01 AM - edited 09-09-2018 12:12 AM
ASA 5506X version 9.8.(2)20
ASDM 7.9.(1)151
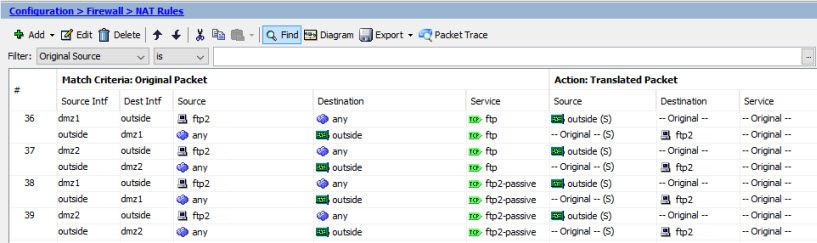
Unfortunately, bridge-group is not fine solution. You can't create NAT rule on bridge-group. You must create NAT rules on each interface (for example dmz1, dmz2) of bridge-group instead:
Look at my example:
I have two ESX hosts. ESX1 connected to interface dmz1, ESX2 - to dmz2.
When my VM (ftp2) hosted on ESX1 NAT rule 36 working fine, BUT if my VM (ftp2) hosted on ESX2 NAT fails!
Why? I see in debug logs ASA trying to establish NAT connection from Outside to DMZ1 interface, but not trying to DMZ2 (where ftp2 situated). So you should to move rules (38-39) for dmz2 interface upper OR move VM ftp2 to ESX1!!!
"Fine"!?
Is it possible to solve this issue without additional switch in my network typology ??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 11:15 AM
Hello, in asa version 9.7 you can create bridge groups. But if you do that you can no longer assign VLAN's to it. VLAN's can only be assigned to interfaces and the Bridge-group is not an interface, Most likely reason the device has more ports is for Etherchannel purposes in combination with a DMZ as an example..
.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 11:34 AM
Thank you very much for your response, Dreminee
I know about Bridge-groups. I try to setup Port-channel, but I have questions about configuration on the VMware side. I have discussion about it on vmware forum, but without replies =(
P.S. I use the latest asa firmware.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 12:13 PM
Interesting schematic you have there in the vmware forum. I have two esxi servers here but no direct connection to the ASA.In my case there is a switch in between. What kind of server hardware you are using for the VMWare esxi servers? Do you run the free version of esxi or a licensed version with the vcenter application?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 01:47 PM - edited 03-01-2018 01:49 PM
I don't want to install additional device to datacenter. That why I trying to configure ASA+ ESXi directly.
We use licensed version with vCener with distributed switch.
Our hardware are: HP ProLiant DL360 gen8 and DL380 gen9.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 12:19 PM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide