- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: asa and pa
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
asa and pa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 01:42 AM - edited 11-28-2020 07:49 AM
Hi,
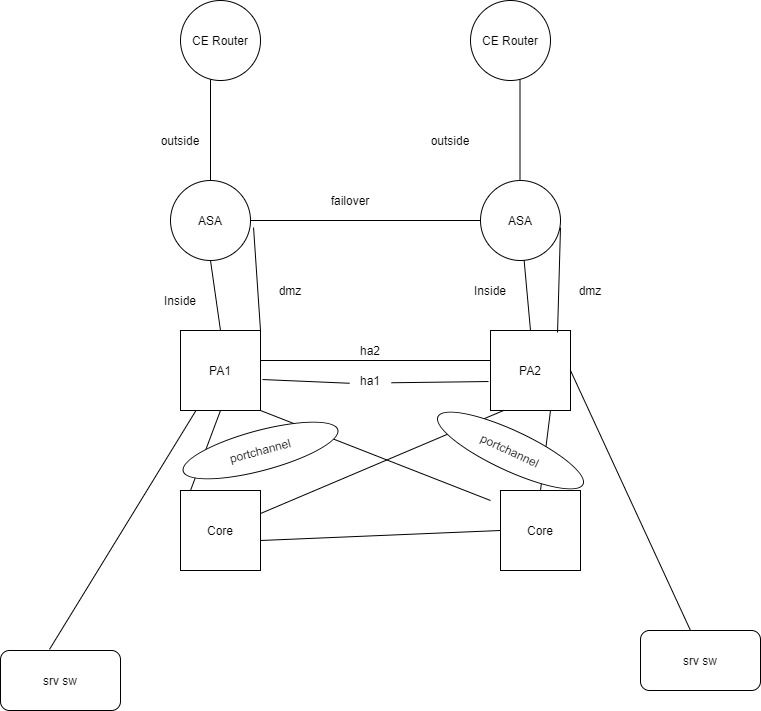
I have the below topology
PA and ASA are in routed mode .
The first question is the design is valid?
I am facing a problem in this design
ASA says the secondary is failed ,primary asa says the secondary and dmz zone interface failed
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 03:09 AM - edited 11-28-2020 03:10 AM
The primary and secondary ASA need to have L2 connectivity with each other on all interfaces. That seems to be not the case in your design. All in all your design is quite "strange" ... What is your design goal here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 06:44 AM - edited 11-28-2020 08:09 AM
Hi,
Thanks for the reply.
The primary and secondary ASA need to have L2 connectivity with each other on all interfaces
If I remove PA from the scenario, there will be l2 connectivity?'
There is a failover connectivity between ASA1 and ASA2 (L2 ). Sorry, I forgot to mark this in the diagram.
What do you mean about L2 connectivity here?
PA here uses as DC firewall and ASA is internet edge firewall. since ASA does not have l7 protection .So the traffic from the internet also going through PA (both directions -inside zone ). And the same is applies to DMZ also
Asa shows the reason for failure
State Last Failure Reason Date/Time
This host - Primary
Active Ifc Failure 13:03:25 Nov 26 2020
Inside: No Link
Other host - Secondary
Standby Ready Ifc Failure 13:17:44 Nov 26 2020
Inside: Failed
there is a link inside, Why asa complaining about no link inside?.
After some time it shows Inside failed
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 08:16 AM
If you want to have PAs L7 protection for your DMZ-Servers, then you have to move that interface to the PA. The inside interface of both ASAs are connected with the outside interfaces of the PA in one VLAN.
Similar for ASAs outside interface: Both interfaces are connected in one VLAN with the ISP-routers. Is that one ore two ISPs? If two, you also have two ASA outside interfaces, each in one VLAN with the corresponding ISP-router-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 09:32 AM
Hi,
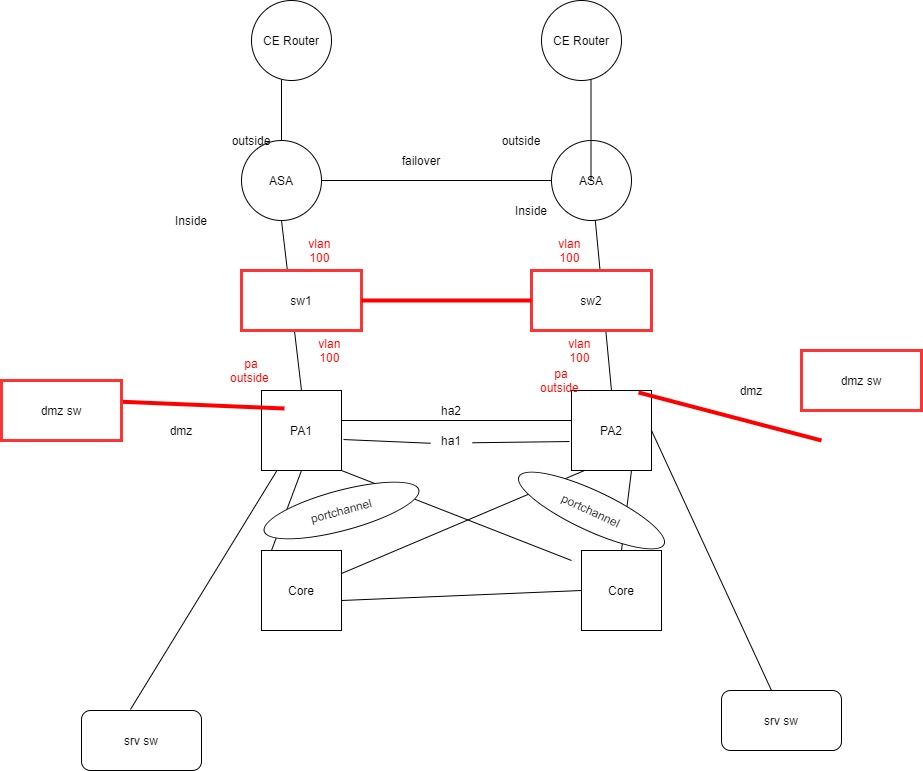
thanks for the reply, it would be great if you can give a rough diagram for a better understanding
As I understand from your comment,
there will be two switches in between ASA inside and PA outside.
VLAN 100 configured, ASA inside interface and PA outside interface are in VLAN 100
And DMZ moved to PA. So the DMZ traffic will flow through the inside interface.
please see the diagram
is that correct
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 09:39 AM
I think you would need a switch in between the ASAs and the PAs. Reason of this is because I think when you connect them directly and the PA is in passive mode, the interfaces status would not be active, accordingly, the ASA standby unit interfaces would be marked as down, hence the primary would deem the standby unit as failed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 10:00 AM
Thanks for the reply. What about DMZ interface. Can I connect to the same switch or do I need another switches ?
security wise, is it recommended connecting dmz interface and inside interface on the same switch
Thanks again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 11:04 AM
You welcome. In this case you would not need additional switches to be dedicated for the DMZ segment. The reason behind this is because your actual internal resources will not be connected to those two switches (SW1 and SW2) as they are protected behind the PA firewalls. Also, the traffic coming through the ASAs is treated as untrusted till it hits and passes through the PAs, so I can't see any issue in segregating SW1 and SW2 with two VLANs, and using one for the cross-connect between the firewalls and another for the DMZ. However, if you wanted to connect the DMZ segment to the same switches where you internal resources are connected (SRV SW), then I would not recommend that, in that case I would recommend to use a dedicated switches for DMZ segment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 10:34 AM - edited 11-28-2020 10:35 AM
Friend first there is something to know
in your design there are two approach one is HW and other is virtual.
I will talk about the virtual
both outside ASA must connect though two VLAN to to CE router.
VLAN for failure link between two ASA.
both inside ASA must connect through one VLAN to the Core.
here PA can config as transparent mode "i don't know about PA but ASA have this mode which is L2 mode"
PA with transparent mode act as bridge which only change the VLAN ID.
NOW here is Core use technology link vPC or VSS.?
if they don't use VSS or VPC then they appear as separate Core SW and hence
VLAN from PA to two both Core must span through link between the both Core
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 11:05 AM
both inside ASA must connect through one VLAN to the Core.
I cannot connect ASA directly connect to the core .
PA with transparent mode act as bridge which only change the VLAN ID.
Can you explain bit more .
It would be great if you give a rough diagram
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 12:07 PM
both inside ASA must connect through one VLAN to the Core.
I cannot connect ASA directly connect to the core .
Answer1.
ASA use one VLAN connect inside of both ASA to the Core, this VLAN ID for example VLAN ID 10,
because ASA not directly connect to Core but connect to PA and PA is connect the Core and as I mention PA will change the VLAN ID to be instead of 10 to be 20.
Answer2.
https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-admin/networking/interface-deployments/virtual-wire-deployments
NOTE:- as I mention before Core since they not use vPC or VSS then the VLAN (which is VLAN 20) must be span from one Core SW to other Core SW.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide