- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA does not force the client to use TLSv1.2!!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2020 04:33 AM
Hey guys,
I have ASA5525, FPR2110, and old 5515. On all of them, the SSL setting is:
ssl server-version tlsv1.2
ssl client-version tlsv1.2
ssl cipher default fips
ssl cipher tlsv1 fips
ssl cipher tlsv1.1 fips
ssl cipher tlsv1.2 fips
ssl cipher dtlsv1 fips
ssl dh-group group5
ssl trust-point SSL_55ty
ssl trust-point Trev Outside
ssl trust-point Trev Outside vpnlb-ip
And SSL output:
Accept connections using SSLv3 or greater and negotiate to TLSv1.2 or greater
Start connections using TLSv1.2 and negotiate to TLSv1.2 or greater
SSL DH Group: group5 (1536-bit modulus)
SSL ECDH Group: group19 (256-bit EC)
SSL trust-points:
Self-signed (RSA 2048 bits RSA-SHA256) certificate available
Self-signed (EC 256 bits ecdsa-with-SHA256) certificate available
Default: SSL_SPdata (RSA 2048 bits RSA-SHA256)
Interface Outside: Trev (RSA 2048 bits RSA-SHA384)
VPNLB interface Outside: Trev (RSA 2048 bits RSA-SHA384)
Certificate authentication is not enabled
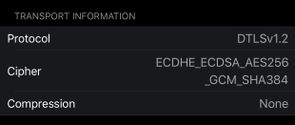
When I connect with my anyconnect to 5515 the connection is DTLSv1.2:
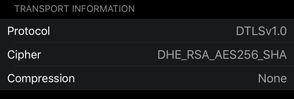
But on FPR2110 and 5525 I get DTLSv1.0:
Why 2110 and 5525 do not force the client to DTLSv1.2?
Thanks
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2020 04:38 AM
What version of ASA are you running? DTLS 1.2 was introduced in version 9.10
If you were running FTD then DTLS 1.2 was only introduced in version 6.6
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2020 04:38 AM
What version of ASA are you running? DTLS 1.2 was introduced in version 9.10
If you were running FTD then DTLS 1.2 was only introduced in version 6.6
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2020 02:44 AM
5525 has 9.8(3)16 and FPR has 9.8(4)17 but 5515 has 9.12. That's it then
Thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide