- Cisco Community
- Technology and Support
- Security
- Network Security
- Hi Karthik , Thanks a lot ..
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA global policy Vs ACL on interfaces.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2014 06:52 PM - edited 03-11-2019 09:30 PM
Hi All,
Please clear my doubt on ASA global policy how is it work.
understand global policy is inspect the packet if we don't have any ACL applied on interfaces(default behavior).
But when we applied ACL on interfaces will Global policy still inspect the packet ?
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
inspect icmp error
Thanks.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2014 08:58 PM
Hi,
Yes it will still inspect even though you have configured ACL and binded to an interface. There are certain protocols which requires deep inspection in order to pass through a firewall. For some of the protocols ASA cannot create the reverse flows, where inspection is required to do so. Below mentioned excerpt from cisco document will explain much better.
The ASA creates forward and reverse flows in the fast path for TCP traffic; the ASA also creates connection state information for connectionless protocols like UDP, ICMP (when you enable ICMP inspection), so that they can also use the fast path.

Note ![]() For other IP protocols, like SCTP, the ASA does not create reverse path flows. As a result, ICMP error packets that refer to these connections are dropped.
For other IP protocols, like SCTP, the ASA does not create reverse path flows. As a result, ICMP error packets that refer to these connections are dropped.
Some packets that require Layer 7 inspection (the packet payload must be inspected or altered) are passed on to the control plane path. Layer 7 inspection engines are required for protocols that have two or more channels: a data channel, which uses well-known port numbers, and a control channel, which uses different port numbers for each session. These protocols include FTP, H.323, and SNMP.
Regards
Karthik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2014 08:45 PM
Hi Karthik,
Thanks for clarification do you have any Cisco link which explain more.Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2014 10:40 PM
Hi Narinder,
The below mentioned documents will clarify your doubts.
http://www.cisco.com/c/en/us/td/docs/security/asa/asa70/configuration/guide/config/inspect.html
http://www.cisco.com/c/en/us/td/docs/security/asa/asa91/configuration/firewall/asa_91_firewall_config/inspect_overview.html.
Figure 9-1 How Inspection Engines Work
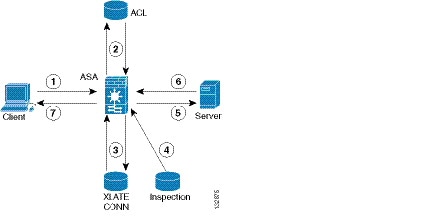
In Figure 9-1, operations are numbered in the order they occur, and are described as follows:
1.![]() A TCP SYN packet arrives at the ASA to establish a new connection.
A TCP SYN packet arrives at the ASA to establish a new connection.
2.![]() The ASA checks the ACL database to determine if the connection is permitted.
The ASA checks the ACL database to determine if the connection is permitted.
3.![]() The ASA creates a new entry in the connection database (XLATE and CONN tables).
The ASA creates a new entry in the connection database (XLATE and CONN tables).
4.![]() The ASA checks the Inspections database to determine if the connection requires application-level inspection.
The ASA checks the Inspections database to determine if the connection requires application-level inspection.
5.![]() After the application inspection engine completes any required operations for the packet, the ASA forwards the packet to the destination system.
After the application inspection engine completes any required operations for the packet, the ASA forwards the packet to the destination system.
6.![]() The destination system responds to the initial request.
The destination system responds to the initial request.
7.![]() The ASA receives the reply packet, looks up the connection in the connection database, and forwards the packet because it belongs to an established session.
The ASA receives the reply packet, looks up the connection in the connection database, and forwards the packet because it belongs to an established session.
The default configuration of the ASA includes a set of application inspection entries that associate supported protocols with specific TCP or UDP port numbers and that identify any special handling required.
Regards
Karthik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2014 07:11 PM
Hi Karthik ,
Thanks a lot ..
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
