- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA Port Forwarding Issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA Port Forwarding Issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2020 07:00 AM
Hi, Im looking for a bit of assistance, Im pretty sure im making a silly mistake somewhere. I am trying to allow port 3389 through ASA to a host for RDP. I will eventually tie it down so it can only be accessed from one location.
ASA Version 9.8(2)38
ASDM Version 7.8(1)
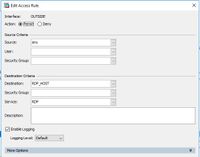
Screenshots of NAT and ACL rules attached. It is failing the packet tracer on the ASA at the NAT section.
Any help appreciated.
Thanks
- Labels:
-
Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2020 07:00 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2020 08:26 AM
The ACL-picture does not show the relevant part. Did you use the internal Host as the destination in your ACL? That is what has to be done. And what is the output of packet-tracer? "it fails" is not a problem-description. It could be the wrong order of NAT-statements, but you also don't show them. Hard to help without this information...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 02:02 AM
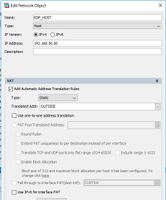
Sorry about that, Too quick editing screencaps, New ones below, as well as the relevant lines from show run
object service RDP
service tcp destination eq 3389
description RDP
object network RDP_HOST
host 192.168.50.50
access-list OUTSIDE_access_in extended permit object RDP any object RDP_HOST
object network RDP_HOST
nat (INSIDE,OUTSIDE) static interface service tcp 3389 3389
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 02:51 AM
At least the config looks fine. What is your packet-tracer command? Did you also test real traffic? Perhaps it is working but you only did a mistake in packet-tracer?
The correct packet-tracer command would be:
packet-tracer input OUTSIDE tcp 1.2.3.4 1234 IP-OF-YOUR-OUTSIDE-INTERFACE 3389
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 03:04 AM
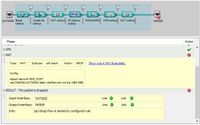
Hi, thanks for that. I thought I was doing something stupid. I ran the packet tracer through ASDM GUI in the example before. However the example below seems to be different
Result of the command: "packet-tracer input OUTSIDE tcp 192.168.50.50 3389 OUTSIDEINTERFACEIP 3389"
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop OUTSIDEINTERFACEIP using egress ifc identity
Phase: 2
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: OUTSIDE
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 04:01 AM
Again, your packet-tracer command is wrong. The source MUST be an IP that is located (based on the routing-table) on the outside interface. Because of that I always use 1.2.3.4 as the source.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 04:10 AM
Apologies, and thanks again,
Result of the command: "packet-tracer input OUTSIDE tcp 1.2.3.4 1234 OUTSIDEIP 3389"
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 0.0.0.0 0.0.0.0 Outside
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: Outside
input-status: up
input-line-status: up
output-interface: Outside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 04:47 AM
Again, something goes wrong here as the ASA thinks that the destination is also outside (should be the interface where the host 192.168.50.50 is located) and it does not match a NAT rule. Double-check the OUTSIDEIP in the packet-tracer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 04:53 AM
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 05:29 AM
Yes, it has to be the IP of the outside interface of the ASA as that is the IP for which the translation is configured. But the output of the packet-tracer says it is not ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 05:53 AM
Hi, Thanks
In that case there must be another misconfiguration issue somewhere, as the command was definitely run using the public IP address of the ASA. I have run it again and got the same output, to check.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 06:05 AM
Result of the command: "packet-tracer input OUTSIDE tcp 1.2.3.4 1234 x.x.x.x 3389"
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop x.x.x.x using egress ifc identity
Phase: 2
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: OUTSIDE
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 06:56 AM
Is your NAT-command still in the config or have you removed it accidentally?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 06:59 AM
It is still there and I can see the XLATE in the table
Result of the command: "show xlate | i 192.168.50.50"
TCP PAT from any:192.168.50.50 3389-3389 to OUTSIDE:217.39.144.61 3389-3389
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide