- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA URL Filtering with MPF
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA URL Filtering with MPF
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2013 10:34 AM - edited 03-11-2019 07:14 PM
Hello all,
We have a few VLANs that need to block all web access except for a few approved URLs. Little diagram never hurt.
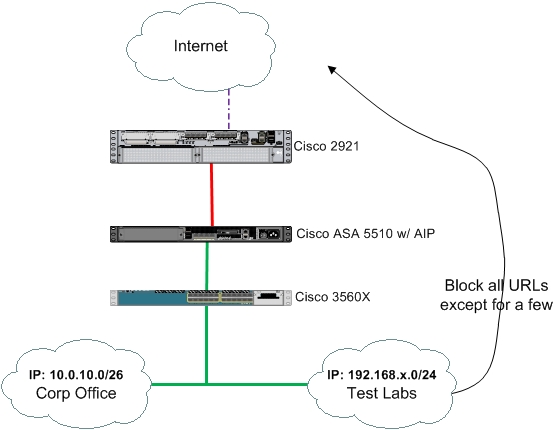
Corp users should have full access to everything web. But the test lab only needs access to just a few 10 or so URLs. Here is what i have configured:
regex TL_URL1 "*\.google\.com"
regex TL_URL2 "www\.yahoo\.com"
class-map type inspect http match-all ALLOWED_URL_CMAP
match not request header host regex TL_URL1
match not request header host regex TL_URL2
access-list TL_URL_ACL extended permit tcp 192.168.1.0 255.255.255.0 any eq www
access-list TL_URL_ACL extended permit tcp 192.168.2.0 255.255.255.0 any eq www
access-list TL_URL_ACL extended permit tcp 192.168.3.0 255.255.255.0 any eq www
class-map TL_USER_CMAP
match access-list TL_URL_ACL
policy-map type inspect http ALLOWED_URL_PMAP
parameters
class ALLOWED_URL_CMAP
drop-connection
policy-map ALLOWED_TL_URL_PMAP
class TL_USER_CMAP
inspect http ALLOWED_URL_PMAP
service-policy ALLOWED_TL_URL_PMAP interface inside
The problem so far is when we apply the map, all web is blocked. What am i missing?
Thanks for the time and support,
Nick
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2013 02:42 PM
If I'm reading your Class-Map correctly:
class-map type inspect http match-all ALLOWED_URL_CMAP
match not request header host regex TL_URL1
match not request header host regex TL_URL2
You are saying, match if the url does NOT match TL_URL1, (2, 3, 4, 5, etc...). The policy-map then states the traffic that matches should be dropped, which is all traffic that doesn't match.
I believe you want to set your class-map to "match-any" and your statemanets to "match request header host regex TL_URLx".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2013 04:37 PM
Thanks for your reply. I will try to play with the settings. But i based my configuration off this like here.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
