- Cisco Community
- Technology and Support
- Security
- Network Security
- Checkpoint to ASA NAT rule
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Checkpoint to ASA NAT rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2014 08:15 AM - edited 03-11-2019 08:46 PM
I'm trying to move my configuration from a Chekcpoint firewall to an ASA 5520 firewall.
My problem is related to the rel 8.4(6) NAT features that seems quite different from the Checkpoint format.
For example in the Checkpoint firewall I've the following NAT rule:
Source Destination Translated Source Translated Destination
INTERNAL DMZ NETW -----> EXTERNAL DMZ NETW EXTERNAL-DMZ-IF-IP ----> Original
this means that when an host (in this case included in a DMZ network) try to connect to an External DMZ network Ip the ip address is translated with the External DMZ Interface Ip
This is working only when the packet is flowing from the Interna DMZ to the External DMZ and not viceversa.
In my new configuration to the ASA I translated this rule using Dynamic PAT:
nat (DMZ-PRODUCTION,EXT-DMZ) source dynamic g-PROD-NETWORK interface destination static g-DMZ-EXT-NET g-DMZ-EXT-NET
where:
DMZ-PRODUCTION is the INTERNAL DMZ NETWORK interface
EXT-DMZ is the EXTERNAL DMZ NETWORK interface
g-PROD-NETWORK is a group containing all the involved networks backward the DMZ-PRODUCTION
g-DMZ-EXT-NET is a group containing all the involved networks backward the EXT-DMZ
All is working fine when I try to reach the external DMZ from the specific production host but if I try to connect from the external DMZ to the production DMZ
host (in reverse mode) I receive a Drop message:
%ASA-5-305013: Asymmetric NAT rules matched for forward and reverse flows; Connection protocol src interface_name:source_address/source_port [(idfw_user)] dst interface_name:dst_address/dst_port [(idfw_user)] denied due to NAT reverse path failure.
An attempt to connect to a mapped host using its actual address was rejected.
Seems that the NAT applied on the interface is enabled also in reverse mode, so can someone explain how I can create this easy NAT rule under Cisco ASA configuration?
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2014 08:27 AM
Hi,
The error message is generated because you are connecting from EXT to PROD and on the initial direction the connection possibly doesnt match any NAT rule but the reverse check for NAT matches the above "nat" configuration you mentioned. The same NAT should be matched for both directions of the traffic and naturally when you have a Dynamic PAT facing from one network to the other then there is problem.
You are essentially first telling the ASA with the "nat" command that the whole PROD network should be hidden behind a PAT address towards EXT but you are trying to connect to the PROD from behind the EXT even though you just configured that the hosts on PROD should be hidden behind PAT.
Typically I would not even configure any NAT between different local interfaces and I am wondering why you want to do Dynamic PAT between your local interfaces? Wouldnt it be easier to allow them to connect with their original IP addresses?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2014 08:44 AM
Hi Jouni,
this is a good question: the EXT-DMZ Interface is also connected to internet public networks (this is an architecture limit).
For this reason in some cases I need to reach the original Ip because connection is starting from the Ext Dmz hosts, in other cases I don't need to reach the orignal Ip but I need to translate the Dmz-production Ip with the external Dmz Interface Ip to reach the Internet public network.
-Roberto
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2014 09:03 AM
Hi,
Are you saying that behind the EXT-DMZ there is an another gateway out of the network that those devices use and you need the Dynamic PAT so the traffic from PROD-DMZ appears to the EXT-DMZ hosts coming from the directly connected network?
Or did I missunderstand the setup completely?
If this is the situation then I think you first need to determine all the PROD-DMZ hosts that need to be connected to using their original/local IP address from EXT-DMZ. Then you will have to configure a Static Policy NAT between PROD-DMZ and EXT-DMZ on a higher priority/order than the existing Dynamic PAT. This would enable these hosts to connect with original IP address while the Dynamic PAT would also function.
Hopefully I have not mistaken something. Already confusing myself between the DMZs
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2014 05:33 AM
Hi Jouni,
please find attached a network schema that can help to better understand my problem.
From the inside network a client with the ip 10.12.1.5 is trying to reach an http server using the url solved by an external (out of the ASA) DNS.
The ip destination is 4.4.5.2 (external Http server) translated to the internal Http host ip 10.112.1.20.
My problem is that if I apply the ASA (8.3) static NAT I cannot use the real ip 10.112.1.20 from the other firewall interfaces because this is already used for the NAT.
This is my ASA configuration:
nat (INTERNAL-LAN,DMZ-PRODUCTION) source static g-INTERNAL g-INTERNAL destination static h-ext—4.4.5.2 h-int-10.112.1.20 no-proxy-arp
For example from the DB server (ip 10.112.2.2) I cannot reach the real ip 10.112.1.20.
Consider that on the Checkpoint firewall the NAT rule is already implemented and is working correctly only when an internal host ip try to reach the external server ip address while the real http server (10.112.1.20) ip can be used for all the other interfaces (and also from the internal lan).
I hope to was clear … thx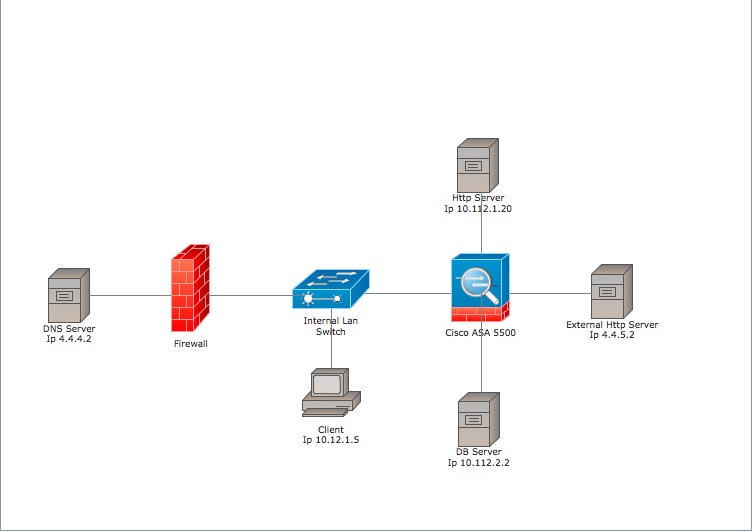
- Roberto
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


