- Cisco Community
- Technology and Support
- Security
- Network Security
- Cisco ASA, connect an IP on OUTSIDE from remote access VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2014 12:58 AM - edited 03-11-2019 08:31 PM
Hi
I looked for resources over net but coudn't find solution, so posting here. May be somebody can help.
So the problem is that i'm trying to access a server on cloud from remote access VPN(cisco asa 5510).
The server on cloud (54.54.54.54) is only accessible from outside interface(192.168.11.2) of NY firewall (cisco asa 5510)
I've added ACE for this in ACL of VPN split tunnel.
ny-fw# access-list vpn_remote-client standard permit host 54.54.54.54
And i can see the route added to my cliet machine after connecting VPN, but still it cannot connect to this server.
From INSIDE network i can connect to server.
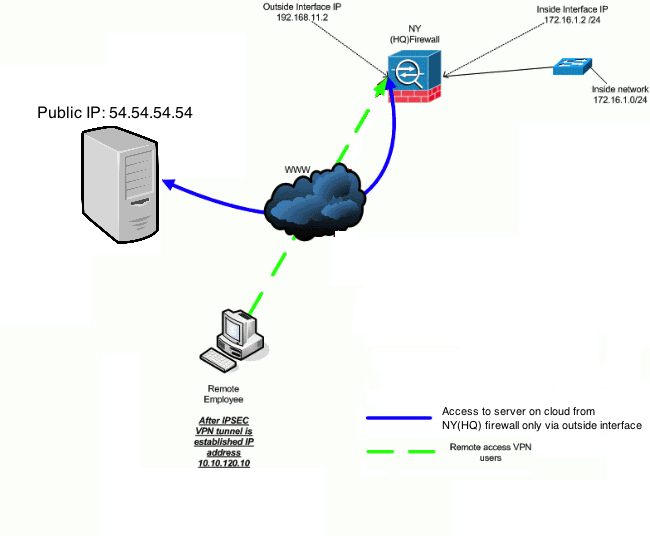
Thanks in advance.
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2014 01:09 AM
Hi,
This is most likely a Hairpin/U-turn problem with NAT.
Would need to see configurations or you would need to check them yourself
I am not sure what your ASA software version is either as that determines what the NAT configuration format is.
So far you have confirmed that the ASA VPN configuration provides the VPN Client with the route for the remote server. So traffic should be tunneled to the ASA.
Next you will have to check the output of this command
show run same-security-traffic
You would need to see the below command in the output
same-security-traffic permit intra-interface
If you dont see it you would need to add it. This commands purpose is to enable traffic to enter an interface and leave through that same interface. In your case this applies to the Internet traffic from VPN Client to the remote server as it enters "outside" and leaves through "outside".
Next we would need to make sure that Dynamic PAT is configured for the VPN Clients.
Software 8.2 (and below)
You most likely have a Dynamic PAT configuration like this on the firewall if running the above software version levels
global (outside) 1 interface
nat (inside) 1 0.0.0.0 0.0.0.0
In this situation if we wanted to add Dynamic PAT for a VPN Pool we would add
nat (outside) 1
This would enable the VPN users to use the same public IP address as the LAN users when accessing the remote server
Software 8.3 (and above)
Since the NAT configuration format is completely different in the newer software you could probably just add a new NAT configuration completely without adding to an existing one
object network VPN-PAT
subnet
nat (outside,outside) dynamic interface
Naturally its possible that there could be some NAT configuration already on the device that might cause problems for this configuration. If it doesnt work then we would have to look at the actual configurations on the ASA.
Hope this helps
Let me know how it goes
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2014 01:09 AM
Hi,
This is most likely a Hairpin/U-turn problem with NAT.
Would need to see configurations or you would need to check them yourself
I am not sure what your ASA software version is either as that determines what the NAT configuration format is.
So far you have confirmed that the ASA VPN configuration provides the VPN Client with the route for the remote server. So traffic should be tunneled to the ASA.
Next you will have to check the output of this command
show run same-security-traffic
You would need to see the below command in the output
same-security-traffic permit intra-interface
If you dont see it you would need to add it. This commands purpose is to enable traffic to enter an interface and leave through that same interface. In your case this applies to the Internet traffic from VPN Client to the remote server as it enters "outside" and leaves through "outside".
Next we would need to make sure that Dynamic PAT is configured for the VPN Clients.
Software 8.2 (and below)
You most likely have a Dynamic PAT configuration like this on the firewall if running the above software version levels
global (outside) 1 interface
nat (inside) 1 0.0.0.0 0.0.0.0
In this situation if we wanted to add Dynamic PAT for a VPN Pool we would add
nat (outside) 1
This would enable the VPN users to use the same public IP address as the LAN users when accessing the remote server
Software 8.3 (and above)
Since the NAT configuration format is completely different in the newer software you could probably just add a new NAT configuration completely without adding to an existing one
object network VPN-PAT
subnet
nat (outside,outside) dynamic interface
Naturally its possible that there could be some NAT configuration already on the device that might cause problems for this configuration. If it doesnt work then we would have to look at the actual configurations on the ASA.
Hope this helps
Let me know how it goes
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2014 01:22 AM
Thanks a lot.
Dynamic PAT for a VPN Pool was missing. By the way software version of device is 8.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2014 01:27 AM
Hi,
Great to hear that it works now
- Jouni
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


