- Cisco Community
- Technology and Support
- Security
- Network Security
- Cisco ASA inside to inside routing problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2016 01:35 PM - edited 03-12-2019 12:59 AM
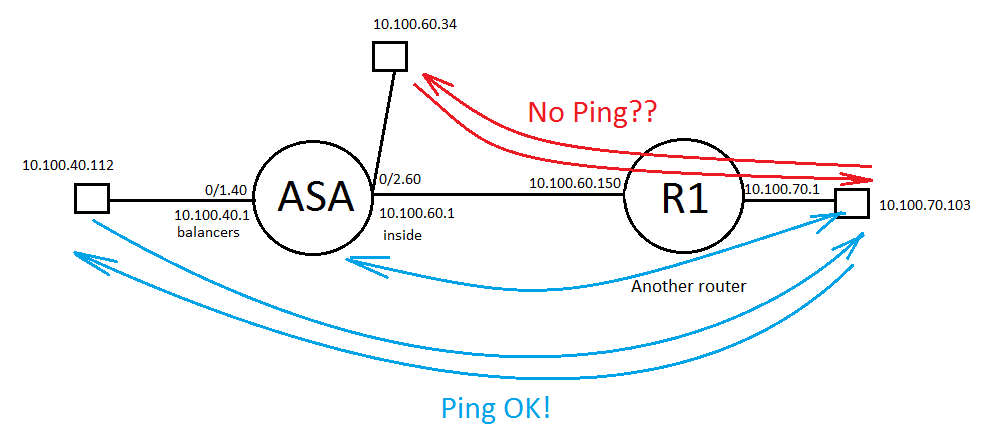
Hello. I have two interfaces configured on ASA - 'inside' 10.100.60.1/24 and 'balancers' 10.100.40.1/24
Also I have router R1 and subnet 10.100.7.0/24 behind. R1 has 2 interfaces - 10.100.70.1/24 and 10.100.60.150/24
Problem is that i can't reach subnet 10.100.70.0/24 from host 10.100.60.34 (Default gateway is ASA 10.100.60.1)
I can successfully reach subnet 10.100.70.0/24 from ASA itself or from other subnets like 10.100.40.0/24
I have access rules for both directions:
access-list access-inside-in extended permit ip object-group net_10.100.70 object-group net_10.100.60
access-list access-inside-in extended permit ip object-group net_10.100.60 object-group net_10.100.70
Also i have NAT rules with 'route-lookup':
nat (any,inside) source static internal_nets internal_nets destination static net_10.100.60 net_10.100.60 no-proxy-arp route-lookup
nat (any,inside) source static internal_nets internal_nets destination static net_10.100.70 net_10.100.70 no-proxy-arp route-lookup
nat (any,balancers) source static internal_nets internal_nets destination static net_10.100.40 net_10.100.40 no-proxy-arp route-lookup
interface GigabitEthernet0/2.60
vlan 60
nameif inside
security-level 100
ip address 10.100.60.1 255.255.255.0 standby 10.100.60.2
interface GigabitEthernet0/1.40
vlan 40
nameif balancers
security-level 60
ip address 10.100.40.1 255.255.255.0 standby 10.100.40.2
# show route
S 10.100.70.0 255.255.255.0 [1/0] via 10.100.60.150, inside
C 10.100.40.0 255.255.255.0 is directly connected, balancers
C 10.100.60.0 255.255.255.0 is directly connected, inside
C ............
packet-tracer input inside icmp 10.100.60.34 8 0 10.100.70.103
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 10.100.70.0 255.255.255.0 inside
Phase: 3
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (any,inside) source static internal_nets internal_nets destination static net_10.100.60 net_10.100.60 no-proxy-arp route-lookup
Additional Information:
NAT divert to egress interface inside
Untranslate 10.100.70.103/0 to 10.100.70.103/0
Phase: 4
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2016 04:15 AM
Hi
I don't see why you have nat exemption as the traffic remains on inside interface.
Also verify that Same-security-traffic permit intra-interface is configured on your asa.
Thanks
PS: Please don't forget to rate and mark as correct answer if this solved your issue
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2016 04:26 PM
Hi
sorry for my short answer I'm on the bus right now.
why are you using nat?
did you activate same-security interface feature?
thanks
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2016 12:16 AM
This rules wasn't configured by me but i guess it stands for security.
Are you asking about 'noproxyarp' option? It is disabled for all interfaces
asa01# show run all sysopt
no sysopt connection timewait
sysopt connection tcpmss 1380
sysopt connection tcpmss minimum 0
sysopt connection permit-vpn
sysopt connection reclassify-vpn
no sysopt connection preserve-vpn-flows
no sysopt radius ignore-secret
no sysopt noproxyarp out
no sysopt noproxyarp public
no sysopt noproxyarp outside
no sysopt noproxyarp dmz
no sysopt noproxyarp balancers
no sysopt noproxyarp in
no sysopt noproxyarp inside
no sysopt noproxyarp management
.....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2016 04:15 AM
Hi
I don't see why you have nat exemption as the traffic remains on inside interface.
Also verify that Same-security-traffic permit intra-interface is configured on your asa.
Thanks
PS: Please don't forget to rate and mark as correct answer if this solved your issue
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2016 05:16 AM
I did 'same-security-traffic permit intra-interface' and the problem is solved
Thanks very much!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2016 05:59 AM
You're very welcome
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


