- Cisco Community
- Technology and Support
- Security
- Network Security
- Cisco FTD - AAA (Accounting only) to extenral radius server
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco FTD - AAA (Accounting only) to extenral radius server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2023 12:12 AM - edited 05-12-2023 05:05 AM
Recently, I am trying to migrate AAA accounting setting of cisco firewall from ASA to FTD. In old ASA, I have some commands like.
aaa accounting command PRIVILEGE 15 RADIUS
aaa accounting ssh console RADIUS
aaa accounting serial console RADIUS
aaa accounting enable console RADIUS
However it seems that the CLI is something different in FTD platform?
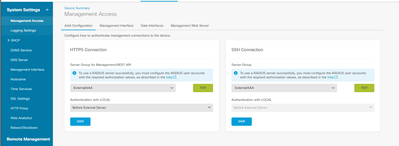
I also checked the managment access page to setup.
The radius server setting only allow authenication and authorization, but no accounting? I mean, if I login by cisco local account, how can I see login log from external server?
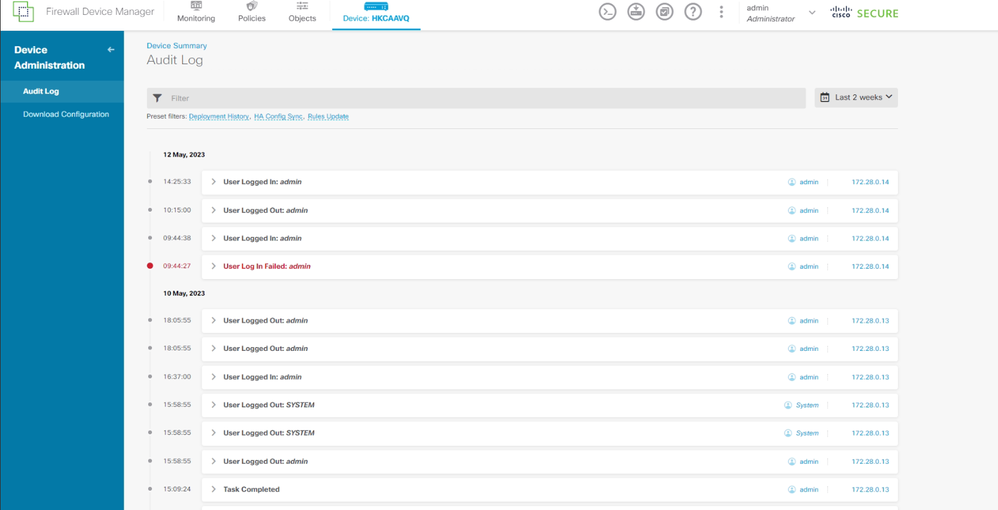
I see that the device login/logout log stored locally is what I needed, but there is no button to export it to external radius.
Or I should use syslog instead to radius accounting to monitor administrative action?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2023 12:49 AM
Streaming to Multiple Syslog Servers
You can stream audit log data to a maximum of five Syslog servers. However, if you have enabled TLS for secured audit log streaming, you can stream only to a single Syslog server.
Classic devices also maintain audit logs. To stream audit logs from Classic devices, see Stream Audit Logs from Classic Devices.
Step 1
Choose System > Configuration.
Step 2
Click Audit Log.
Step 3
Choose Enabled from the Send Audit Log to Syslog drop-down menu.
Step 4
The following fields are applicable only for audit logs sent to syslog:
Step 5
(Optional) To test whether the IP address of the syslog servers is valid, click Test Syslog Server.
The system sends the following packets to verify whether the Syslog server is reachable:
ICMP echo request
TCP SYN on 443 and 80 ports
ICMP time stamp query
TCP SYN on random ports
Step 6
Click Save.
Stream Audit Logs to an HTTP Server
When this feature is enabled, the appliance sends audit log records to an HTTP server in the following format:
Date Time Host [Tag] Sender: User_Name@User_IP, Subsystem, Action
Where the local date, time, and originating hostname precede the bracketed optional tag, and the sending appliance or device name precedes the audit log message.
For example, if you specify a tag of FROMMC, a sample audit log message could appear as follows:
Mar 01 14:45:24 localhost [FROMMC] Dev-MC7000: admin@10.1.1.2, Operations > Monitoring, Page View
To stream audit logs from Classic devices, use device platform settings: Stream Audit Logs from Classic Devices.
Before you begin
Make sure the device can communicate with the HTTP server. Optionally, secure the channel; see Audit Log Certificate.
Procedure
Step 1
Choose System > Configuration.
Step 2
Click Audit Log.
Step 3
Optionally, in the Tag field, enter the tag name that you want to appear with the message. For example, if you want all audit log records to be preceded with FROMMC, enter FROMMC in the field.
Step 4
Choose Enabled from the Send Audit Log to HTTP Server drop-down list.
Step 5
In the URL to Post Audit field, designate the URL where you want to send the audit information. Enter a URL that corresponds to a Listener program that expects the HTTP POST variables as listed:
subsystem
actor
event_type
message
action_source_ip
action_destination_ip
result
time
tag (if defined; see Step 3)
Caution
To allow encrypted posts, use an HTTPS URL. Sending audit information to an external URL may affect system performance.
Step 6
Click Save.
Please refer the below link for reference - https://www.cisco.com/c/en/us/td/docs/security/firepower/70/configuration/guide/fpmc-config-guide-v70/system_configuration.html#ID-2258-00000149
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide