- Cisco Community
- Technology and Support
- Security
- Network Security
- Configure internet access - ASA 5510
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Configure internet access - ASA 5510
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2012 04:26 AM - edited 03-11-2019 05:35 PM
Hi everyone,
I am a newbie and i have to configure a default-factory firewall (ASA 5510) in a simple scenário like this image represents:
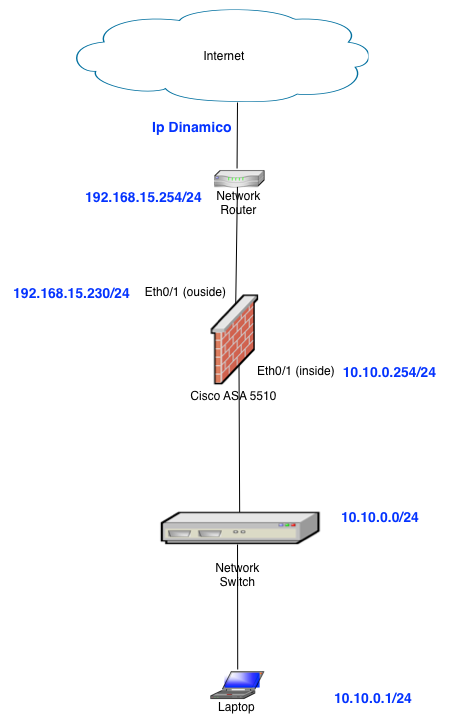 At this moment i have configured the interfaces as represented above and at this moment what i want is grant access from a LAN computer (10.10.0.0/24) to the internet.
At this moment i have configured the interfaces as represented above and at this moment what i want is grant access from a LAN computer (10.10.0.0/24) to the internet.
Any suggestion?
Should i configure some acl? I read that all traffic from an interface with a superior security level to other interface is allowed, so since my inside interface has a security level of 100 and the outside 0, it should be possible access to internet from an inside computer?!
From all configurations and examples i have seen around, they all contemplate a fixed IP address from the ISP, but in my scenário i have a dynamic one. This fact matter for the configuration i want to do?
Another thing, taking my scenário, i should configure the firewall in routed mode, not in transparent. Am i correct?
Notes:
My firewall is running the software version 8.2(5).
Best regards ant thanks for any tip.
JL
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2012 06:05 AM
Hey,
Before we get started,
It seems you have an router infront of the ASA Firewall and its getting the public IP address with DHCP. Would it be possible to make this router/modem bridged so it doesnt do any NAT/Routing in between and ASA would get the IP address from the ISP
Considering the future this might save you from a lot of headaches and in general it would be clearer if the device infront of the ASA wouldnt do anything else but provide the DSL to Ethernet connection.
If you could confirm the above we could forward with the actual configurations.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2012 07:09 AM
Hi Jouni,
Thank you for your reply.
Yes, i have a router in front of ASA firewall and it is getting an dynamic public IP address (DHCP).
Considering my needs, it is possible configure the router in bridged mode.
I haven't represented here (in the image) but i want to enable a guest wifi network that only gives access to the internet, and i was thinking configure it in the network 192.168.15.0/24 (the network that connects ASA to router).
What is your suggestion to this issue considering that i would configure the router in bridged mode?
Thank you once again.
JL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2012 08:07 AM
Hi,
Sorry, Wireless is one area of networking where I sadly have no expirience in. Other people in my company handle it.
Was the current Modem/router the device/AP which would handle the wireless customers?
If so I guess we could go about this matter so that we check your firewall configuration with your orignal setup. That is, with the modem/router in routed mode and getting the public IP address from ISP. Unless you can think of some solution yourself.
Can you provide the current configuration of the ASA if it needs to be gone through.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2012 08:45 AM
Hi Jouni,
The actual running configuration is the following:
: Saved
:
ASA Version 8.2(5)
!
hostname ciscoasa
enable password 5C22.c6gSPFnC4aq encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 192.168.15.230 255.255.255.252
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 10.10.0.254 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
management-only
!
ftp mode passive
pager lines 24
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu management 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 1 0.0.0.0 0.0.0.0
route outside 0.0.0.0 0.0.0.0 192.168.15.254 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.1.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
telnet timeout 5
ssh timeout 5
console timeout 0
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:e47a966eec06717af1463367fb5142d5
And as i refered previously, the only thing i want to do is access the internet from a computer on the inside network (10.10.0.xx/24).
Thank you,
JL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2012 08:49 AM
Hi,
Mask on your "outside" interface is wrong compared to the picture and also regarding the gateway IP address of the default route
EDIT:
Looking above the picture says your ASA outside network is 192.168.15.0/24
The "outside" interface is configured with mask /30
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2012 08:58 AM
Regarding the use of ACL
You have no real need to configure ACL on any interfaces UNLESS
- You need to limit connectivity between networks behind different interfaces
- You need to open some service from the Internet to a LAN server (which has Static NAT configuration)
Do notice also that as soon as you define an ACL to any interface, the "security-level" will not matter anymore, in the same way atleast.
For example,
- You have "inside" interface with "security-level 100" and no ACL attached to the interface
- All traffic can go through the firewall to any interface PROVIDED that the destination interfaces "security-level" is below the source interfaces "security-level"
- You add "access-list INSIDE-IN permit tcp any any" and attach it to "inside" interface with "access-group INSIDE-IN in interface inside"
- While all TCP traffic from behind "inside" interface will go through the firewall, no UDP connections will be permitted from networks behind "inside" interface. It would need an addtional rule.
- If your connection attempt doesnt match some rule in the ACL attached to the interface, it will be denied.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2012 01:07 PM
Hello Jose,
Should i configure some acl? I read that all traffic from an interface with a superior security level to other interface is allowed, so since my inside interface has a security level of 100 and the outside 0, it should be possible access to internet from an inside computer?!
You should if you want it to restrict the inside traffic but if you just want to allow the inside users to go to the internet there is no need for thas because as you read traffic from a higher security level to a higher is allowed by default.
From all configurations and examples i have seen around, they all contemplate a fixed IP address from the ISP, but in my scenário i have a dynamic one. This fact matter for the configuration i want to do?
No, not at all as you will not use that on your ASA, the dynamic IP will be used on your outside router so nothing to worry in your ASA.
Another thing, taking my scenário, i should configure the firewall in routed mode, not in transparent. Am i correct?
Routed mode is more than fine for you
Now based on your configuration and you been unable to access the internet, can you check the following:
Change the netmask on the outsie interface to 255.255.255.0
interface Ethernet0/0
ip address 192.168.15.230 255.255.255.252
What is the DNS server on your PC,
Add the following command: " fixup protocol icmp "
Can you ping 192.168.15.254 from your PC?
Can you ping 4.2.2.2 from the ASA
Can you ping 4.2.2.2 from the pc?
Julio
Remember to rate all of the helpful posts
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


