- Cisco Community
- Technology and Support
- Security
- Network Security
- MikeThere would be no routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2015 08:59 AM - edited 03-11-2019 11:37 PM
Hi,
I need help with a DMZ on our edge network and a ton of web servers that are in the DMZ from two different /24 subnets..
We have 2 x /24 public subnets that are routed to us from our ISP (63.241.163.0 and 63.241.172.0). Our ISP routes them to our edge router and I then we have to interfaces off that router for each /24 subnet. The edge firewall’s external IP is 63.241.163.11.
Here’s the main issue. We’re moving our F5 load balancers into the DMZ, the F5’s have over 200 VIPs for IP’s in each one of my public IP ranges.
The DMZ IP range will be 172.21.100.0 /22. Since an ASA can only have one default gateway and I have to solve for two subnets into a single DMZ. How can I allow for each public IP range to hit web servers in my new DMZ from two different public subnets? The ASA’s default route right now is to 63.241.163.1. the upstream router obviously knows about both subnets. I don’t want to trunk the interfaces and I don’t want to route but public IP ranges to the outside IP of the firewall because I need that edge zone for other public service (dmvpn,etc).
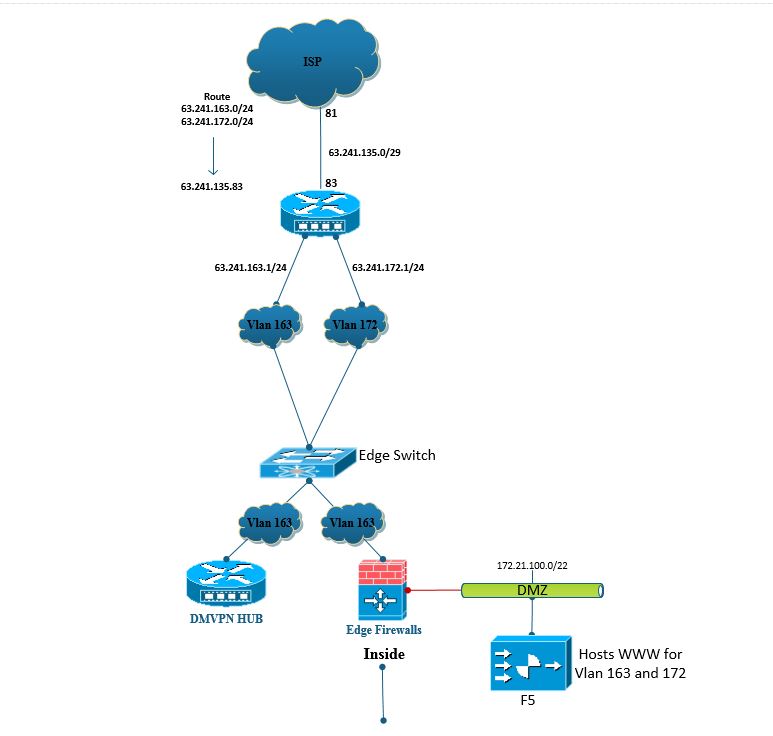
Any help with this is greatly appreciated.
Thanks,
Mike
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2015 01:47 PM
Mike
Your diagram is a bit confusing because it looks like you are using vlan 163 for both the DMVPN and the firewall so when you say you can't route the other range to the outside interface of the firewall is that other range ie. the one for vlan 172 actually being used elsewhere.
Assuming it is and the diagram doesn't show it the only other thing I can think of is to use a secondary IP address for the other range on the edge router internal interface.
So you only have one interface connecting from the edge router to your edge switch and you add the other range as a secondary IP address.
You would then need "permit arp non-connected" on your firewall so that it could respond to arp requests from your router for the range not assigned to any interface.
To be honest I am not a fan of using secondary addresses usually but I'm not sure how else you can do this if you cannot route the second range to the firewall.
Obviously secondary addresses have some quirks so only you can really say whether this is viable or not.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2015 01:47 PM
Mike
Your diagram is a bit confusing because it looks like you are using vlan 163 for both the DMVPN and the firewall so when you say you can't route the other range to the outside interface of the firewall is that other range ie. the one for vlan 172 actually being used elsewhere.
Assuming it is and the diagram doesn't show it the only other thing I can think of is to use a secondary IP address for the other range on the edge router internal interface.
So you only have one interface connecting from the edge router to your edge switch and you add the other range as a secondary IP address.
You would then need "permit arp non-connected" on your firewall so that it could respond to arp requests from your router for the range not assigned to any interface.
To be honest I am not a fan of using secondary addresses usually but I'm not sure how else you can do this if you cannot route the second range to the firewall.
Obviously secondary addresses have some quirks so only you can really say whether this is viable or not.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2015 09:17 PM
Hi Jon,
Thanks for the reply. I too am not a fan of using secondary interfaces.
yes, the other range is the 172 Vlan, I see where my post was confusing. Right now the only way i see this working is if I route the 172Vlan to the outside interface of the firewall - which i didn't want to do.
I guess then I could NAT for that Space into the DMZ. Do you see a possibly for a routing loop here though? Router's DE-route is to 63.241.135.81 - the .81 route's the 172 subnet to the router, the router then routes that subnet to the Firewall. the firewall's def-route is to 63.241.163.1 which is the interface that I would be routing the .172 Vlan address space across....
Confusing this one...
Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2015 07:21 AM
Mike
There would be no routing loop as far as I can see.
Your edge route simply routes all traffic for the vlan 172 IPs to the outside interface of your firewall and you then have NAT statements on the firewall for these IPs.
This is a pretty standard setup unless I am not understanding the question.
Is there are a reason you think there should be a routing loop ?
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2015 04:52 PM
No - you're right Jon.
Thanks for jumping in on this one. I'm going to just route the VLAN 172 IP space to the outside IP of the edge firewall and then NAT from there. I was hoping there was a better way but I think you're right - for what i'm trying to accomplish - this is the easiest and cleanest way to configure the routing.
Thanks for the help.
Mike
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
