- Cisco Community
- Technology and Support
- Security
- Network Security
- Configuring Cisco ASA 5540 Transparent Mode topology
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Configuring Cisco ASA 5540 Transparent Mode topology
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2016 02:28 AM - edited 03-12-2019 01:39 AM
Hi Guys,
I’m having trouble configuring a Cisco ASA 5540 in transparent mode:
The current topology is below:
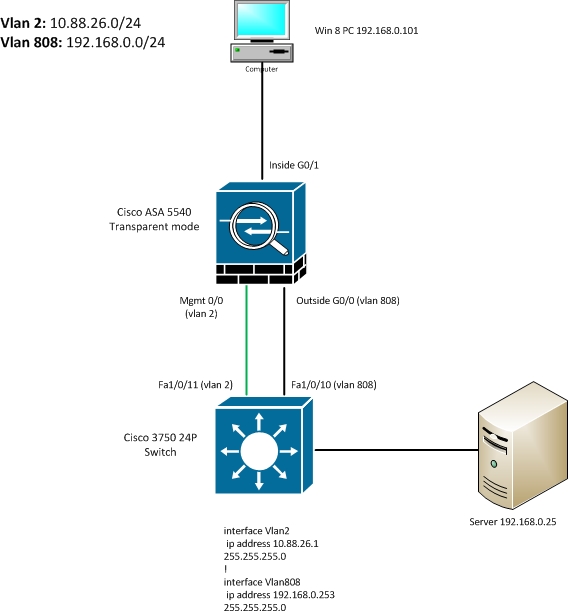
!
!
I would like only specified host/IP addresses to communicate with 192.168.0.101 and vice-versa, these devices are on the same LAN.
Server default gateway = 192.168.0.253
Win 8 PC default gateway = 192.168.0.253
At the moment I would like to ping from the server to the Win 8 PC, but it doesn't seem to work. Have I configured this correctly?
I have attached the configurations below.
(This is on my home network so some of the config isn't relevant.)
Thank you
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2016 02:59 AM
Hello,
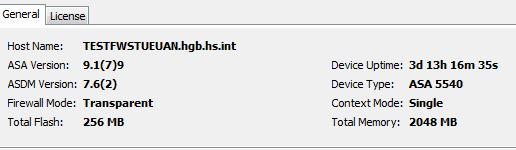
Can you please attach output of
show access-list OUTSIDE_access_in
also, please attach the syslogs you see on ASA once you initiate traffic from server to PC.
-
AJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2016 10:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2016 02:46 AM
Please attach packet-tracer output:
packet-tracer input OUTSIDE icmp 192.168.0.25 8 0 192.168.0.101
Also, please attach output of 'debug icmp trace' while pinging.
Attach output of show access-list OUTSIDE_access_in_1
-
AJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2016 02:11 PM
TESTFWSTUEUAN# packet-tracer input OUTSIDE icmp 192.168.0.25 8 0 192.168.0.101
^
ERROR: % Invalid input detected at '^' marker.
TESTFWSTUEUAN# show access-list OUTSIDE_access_in_1
access-list OUTSIDE_access_in_1; 4 elements; name hash: 0xfb5b9097
access-list OUTSIDE_access_in_1 line 1 extended permit ip host 192.168.0.25 any4 (hitcnt=5893) 0x268e68fa
access-list OUTSIDE_access_in_1 line 2 extended permit ip host 192.168.0.11 any (hitcnt=2018) 0xa05cdcf9
access-list OUTSIDE_access_in_1 line 3 extended permit ip object 10.80.26.20 object 10.80.26.254 (hitcnt=0) 0x8fc319a5
access-list OUTSIDE_access_in_1 line 3 extended permit ip host 10.80.26.20 host 10.80.26.254 (hitcnt=0) 0x8fc319a5
access-list OUTSIDE_access_in_1 line 4 extended deny ip any any (hitcnt=376371) 0xbc7d8fc3
TESTFWSTUEUAN#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2016 10:09 PM
My bad, packet-tracer won't work in transparent mode.
Could you please take captures on inside and outside interface of ASA when ping is attempted from 0.25 to 0.101
Also take asp drop captures as below:
capture drop type asp-drop all
Try to ping the source and destination ip addresses from ASA as well:
ping inside 192.168.0.101
ping OUTSIDE 192.168.0.25
It would be great if we can have some syslogs as well.
-
AJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2016 10:37 AM
TESTFWSTUEUAN# ping inside 192.168.0.101
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.101, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
TESTFWSTUEUAN# ping OUTSIDE 192.168.0.25
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.25, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
TESTFWSTUEUAN#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2016 04:22 AM
The issue seems to be the reachability from ASA to the host 0.101
Could you please check if pings are allowed on the the PC @ 0.101
also, I am assuming that we intend to ping from 0.25 to 0.101, please correct me if I am wrong.
please attach output of show arp
also, please specify how is the PC connected to ASA. Is it connected across the switch or directly to inside interface of ASA.
wireshark captures from PC NIC would be useful.
-
AJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2017 01:55 PM
TESTFWSTUEUAN# sh arp
OUTSIDE 192.168.0.1 e4f4.c6cc.f47b 0
OUTSIDE 192.168.0.253 0027.0d9f.0bc4 40
OUTSIDE 192.168.0.18 000c.2948.c1b0 371
MANAGEMENT 10.88.26.1 0027.0d9f.0bc5 4204
The PC 192.168.0.101 is connected directly to the Firewall (Not via a switch) as shown in the diagram above.
How can I tell the switch how to reach .101?
And you are correct, I'm trying to ping .101 from .25
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide