- Cisco Community
- Technology and Support
- Security
- Network Security
- Cut-through proxy for remote Anyconnect clients
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2014 03:07 AM - edited 03-11-2019 08:37 PM
Hi. I am trying to apply cut-through proxy on Anyconnect clients.
I am using ASA 5505 running asa914-k8.bin
Anyconnect clients are connecting to my outside interface. I am trying to apply the cut-through proxy on those clients trying to access any http.
A partial config of my setup:
access-list authmatch extended permit tcp any4 any4 eq www
access-list authmatch2 extended permit tcp any4 any4 eq www
!
aaa authentication match authmatch outsidee LOCAL
aaa authentication match authmatch2 insidee LOCAL
The cut-through proxy works fine on the inside interface, but not on the outside interface. Anyconnect clients connected to the outside interface are not prompted for authentication... although the cut-through proxy related configuration is identical on bot the inside and the outside interfaces.
I did try if the cut-through worked on the outside interface when not connected via VPN- it did work. It is not working only for the Anyconnect VPN clients.
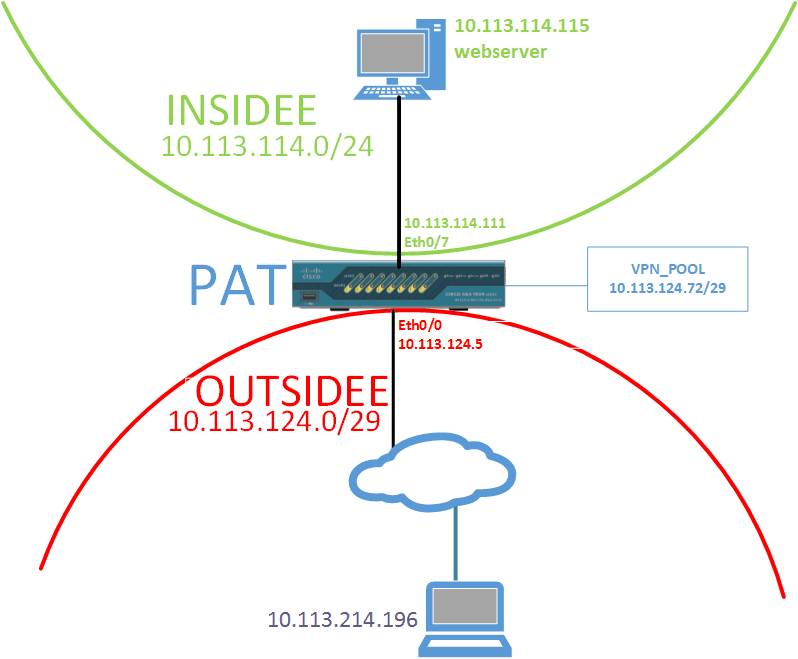
I also added a picture of the network.
Any ideas? thanks!
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2014 09:27 AM
I am not entirely sure that cut through proxy will work with VPN users (though I have not been able to find any documentation to support my theory). Since the VPN users terminate at the ASA (to the box traffic), and it is encrypted when it enters the outside interface, it never leaves the inside interface and comes back in and the traffic is not seen on the outside interface since it is encrypted.
The only option I can think of that might work is to disable the ACL bypass for the VPN traffic. This will mean you need to configure an ACL on the outside interface for the VPN traffic to be allowed in.
no sysopt connection permit-vpn
Though even when this command is present management traffic to the box is still permitted.
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2014 09:27 AM
I am not entirely sure that cut through proxy will work with VPN users (though I have not been able to find any documentation to support my theory). Since the VPN users terminate at the ASA (to the box traffic), and it is encrypted when it enters the outside interface, it never leaves the inside interface and comes back in and the traffic is not seen on the outside interface since it is encrypted.
The only option I can think of that might work is to disable the ACL bypass for the VPN traffic. This will mean you need to configure an ACL on the outside interface for the VPN traffic to be allowed in.
no sysopt connection permit-vpn
Though even when this command is present management traffic to the box is still permitted.
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2014 12:00 AM
no sysopt connection permit-vpn has already been tried- didnt help.
i think you are correct that the proxy is not supposed to work for VPN traffic. thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2014 12:36 AM
Hi,
Did a quick test and seems that the configuration doesnt match to the traffic incoming from the VPN as you mentioned.
Only thing I could think of trying (without going through any documentation and testing this further) would be to use a "tunneled" default route for VPN traffic and forward it straight to some internal router on which the default route would forward traffic back to ASA and you would translate the source address of the VPN users connection (so that the ASA wouldnt see the same source address and drop the connection) and therefore perhaps make this work.
Naturally you might not have a LAN router but a switched network and this would probably also create complexity to the router configurations (if you have one that is)
Naturally the best choice to get this working would be if you had a separate VPN device from which connections would be forwarded to the actual ASA handling the Internet traffic.
Do you have any router on the LAN network or is it only a switched network behind the ASA.
Might be able to test this out on my own network perhaps but not at the moment though.
- Jouni
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide




