- Cisco Community
- Technology and Support
- Security
- Network Security
- Default Action vs. Inspection Rule?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Default Action vs. Inspection Rule?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2015 04:00 AM - edited 03-12-2019 05:46 AM
I've seen mixed configurations where someone will explicitly create an inspection rule using an intrusion policy and then other cases where someone has created an inspection rule only for files (no intrusion policy) but then configures the intrusion policy as the default action. Which method is correct?
- Labels:
-
NGIPS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2015 02:35 PM
For me the default action is only used as a fail safe. It reminds me of an implicit deny in an access list.
The last rule in my Access Control Policy is a 'Default Inspection and File' rule configured to allow traffic. Both the Intrusion Policy and File Policy would be included in this rule.
Its also important to include the Inspection Policy and File Policy to any rules with the allow action. Matching traffic will not be scanned by the IPS Policy unless it is applied at the given rule. An example would be a bypass rule for specific users that may be allowed to use applications in a global application block rule.
I feel like with the example given in the Cisco documentation, this would be the correct way to configure the access policy with an Intrusion and File Policy.
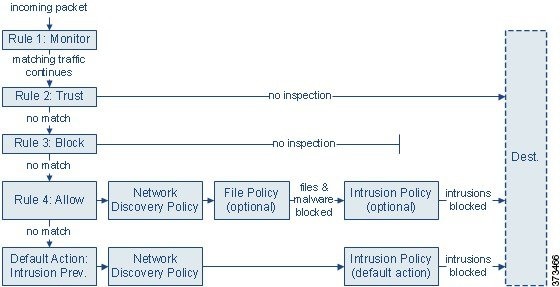
http://www.cisco.com/c/en/us/td/docs/security/firesight/541/user-guide/FireSIGHT-System-UserGuide-v5401/AC-Intrusion-Malware-Detection.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2015 07:16 AM
Gotcha - agree w/ you there. What's confusing me, with that graphic in particular, is where they have the Intrusion Policy on rule 4 as "(optional)" and I'm assuming they are using the same Intrusion Policy as the default action.
Thanks for the thoughts!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
