- Cisco Community
- Technology and Support
- Security
- Network Security
- Failed to locate egress interface
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Failed to locate egress interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2017 05:13 AM - edited 02-21-2020 06:15 AM
Can someone help me out with this problem? We currently have 1 ASA in Datacenter 1 and are trying to implement a second firewall in another Datacenter. The interconnectivity between the Datacenters is fine, but i'm getting the "Failed to locate egress interface" interface when i try to SSH/Ping/ASDM/whatever to the new ASA:
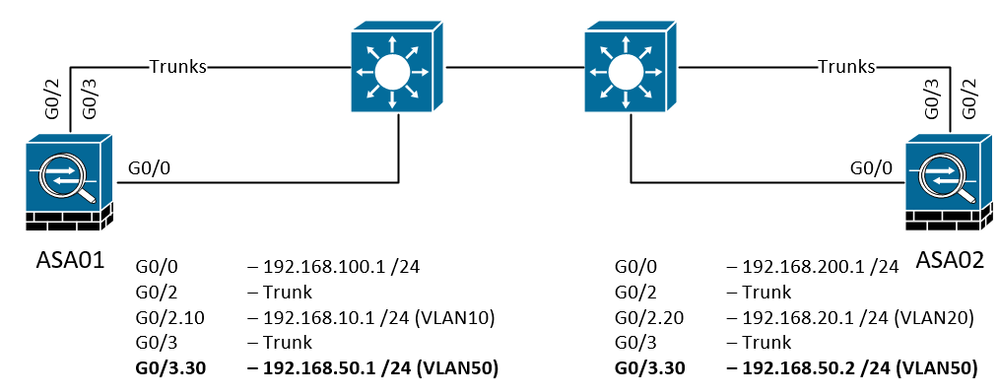
This is the topology:
Both talk to eachother over the "shared" VLAN 50. All the routing to eachothers subnets are done over that VLAN (inter-datacenter-vlan if you like). The ASA's can reach eachother on the 192.168.50.x addresses perfectly fine.
ICMP, SSH, ASDM and every other protocol is working perfectly fine on ASA01, but on the newly installed ASA02 i just can't get it working.
When i try to ping from ASA01 to 192.168.200.1 ASA02 logs the following error:
- %ASA-6-110002: Failed to locate egress interface for ICMP from VLAN50:192.168.50.1/46448 to 192.168.200.1/0
There is no NATing performed.
Same Security Level inter and intra is on
ICMP Permits are on on every interface.
I'm absolutely clueless, since ASA01 is working fine.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2017 04:30 PM - edited 08-29-2017 04:31 PM
Hello,
Make sure you are not trying to reach interface G0/3.30 through G0/0. To be honest, I did not get why you have a trunk and an additional interface linked to the ASA, but, anyway, if you try to cross the firewall to get to another interface, this error arises.
After you are correct the path to the interface you can config the interface you want to access/ping as "management-access ".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2017 10:54 PM
Hi Flavio,
Thanks for the info. I think i'm trying to understand the rule that you cannot enter 1 interface on the ASA, and have that same ASA reply with one of each own other interfaces.
In this case you could even forget that one extra access-link both ASA's have. I'm experimenting with the "management-only" or "management-access" commands but i'm still not getting where i want to be.
Consider the topology from my starting post and. How could i make so that i can SSH/ASDM/ICMP from the ASA01 side to 192.168.20.1 on ASA02? Since all the routing is being done over the shared VLAN50 i'm entering ASA02 on G0/3.30 but i want to reach G0/2.20 on ASA02 (which isn't allowed because of the earlier stated rule for a ASA).
Can i "fix" that with some kind of "management-only" or "management-access" interface? If so, how would i use that since i tried some stuff but i'm not getting it to work.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide