- Cisco Community
- Technology and Support
- Security
- Network Security
- Firepower 1010 VLAN and DHCP issues
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Firepower 1010 VLAN and DHCP issues
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2019 04:08 AM - edited 02-21-2020 09:42 AM
Hello,
I recently got a Firepower 1010 for my home lab and was testing the VLAN interface feature that I previously used on my old ASA 5505.
I used my 5505 as a DHCP server on the Inside network and had the DHCP server enabled on my Inside VLAN interface.
I was trying to setup the 1010 the same way, but I only had the option to select a routed interface and not a VLAN interface.
Anyone know if it suppose to be possible to use a VLAN interface for DHCP on the 1010?
Thanks
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2019 07:03 PM
Can you post a sample configuration of this from your 5505 so we can fully understand what you are trying to configure?
Also, is your plan to run ASA or FTD on your 1010?
Thank you for rating helpful posts!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2019 04:28 AM
Hi,
Thanks for answering. I am planing to run the FTD software.
Here is the relevant config from my ASA 5505 that I want to replicate on my 1010.
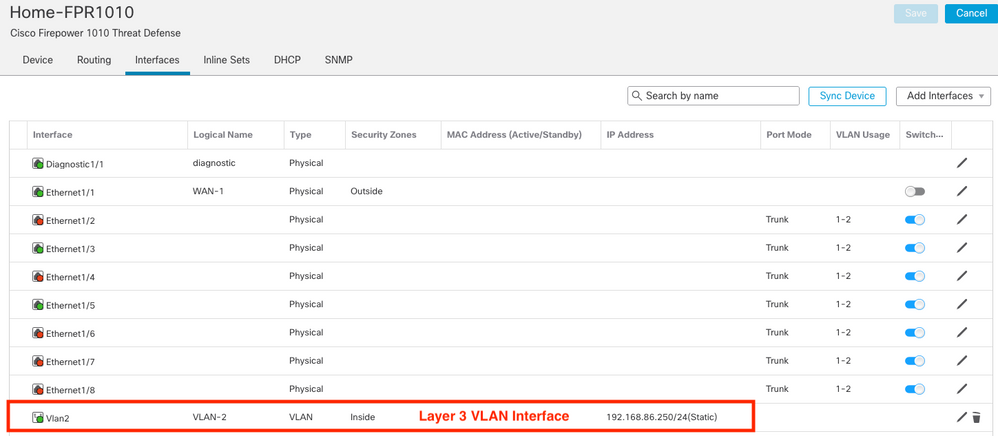
interface Vlan2
nameif INSIDE
security-level 100
allow-ssc-mgmt
ip address 10.46.0.1 255.255.255.0
!
dhcpd address 10.46.0.225-10.46.0.254 INSIDE
dhcpd enable INSIDE
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-01-2020 07:52 AM
The VLAN interface is a routed interface on the ASA 5505, it just has multiple physical interfaces attached to it. So what you are describing is consistent across the two firewalls. DHCP is always enabled on a layer 3 interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 04:37 AM
This is not true. The problem with DHCP on the VLAN interface takes place to be. The interface VLAN does not appear in the list when adding a server. Firepower 1010 version 6.5.0.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2020 04:13 PM
I can assure you a VLAN interface is a routed interface on an ASA5505. This is evidenced by the fact that you apply IP addresses to the VLAN interface on that platform. This, by definition, makes the VLAN interface a routed/layer 3 interface.
Your belief that a VLAN interface on an ASA 5505 is not a routed interface may stem from the fact that a VLAN is a layer 2 mechanism that separates a single broadcast domain into smaller broadcast domains. However, once you create a VLAN interface that for that VLAN, that creates a routable, layer 3 interface for that VLAN which you can then use for DHCP functionality.
As all physical interfaces on an ASA5505 are switched, layer 2 interfaces, the platform utilises VLAN interfaces to route between two different subnets. It is no different to using SVI interfaces on a layer 3 capable switch. Though most, if not all, layer 3 capable switches also allow you to assign an IP address directly to a physical switch port, turning it in to a routed port, the ASA5505 does not support this and must use VLAN interfaces as routed ports.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2020 02:26 AM
Yes, it works on the ASA5500. I wrote that there is a problem with DHCP on the Layer 3 VLAN interface on Firepower 1010
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2020 07:02 AM - edited 04-28-2020 07:02 AM
I have the same issue on my FirePower 1010. I cannot select my L3 VLAN interface when enabling the DHCP server. Both FTD and FMC are running version 6.6. See screenshots below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2021 08:41 AM
Did you solve this?
I've hit the same problem on my FMC (6.6.3) with FPR1010 (FTD 6.6.1)
Can't configure a DHCP relay for VLAN interface... absolutely useless product...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2021 09:06 AM - edited 04-23-2021 09:07 AM
I managed to hack my way around this using flexconfig, for example:
dhcprel enable inside
Replace "inside" with the name of your VLAN interface
(you can't put "dhcprelay" because it's not a supported command....)
Raised a ticket with my reseller, hopefully will make its way into a TAC case because as far as i'm concerned this is basic functionality that should not be missing..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2021 06:58 AM
I'm having the exact same problem with FTD/FMC 6.6.4 - I cannot add DHCP server or relay for VLAN interface... something so basic should be available! I'm not impressed with FTD whatsoever as this isn't the first basic configuration item that I've noticed missing from the platform.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2020 08:36 AM
I have the same problem (or similar), with FMCv 6.5.0.4 & FTD 1010 (v.6.5.0.4)
I wanted to use the ports eth1/7 & eth1/8 to connect 2 access-points (as these ports have PoE option), but I couldn't add the Vlan IDs to the switchport (in FMC GUI it allowed me to configure them, but deployment failed).
At deployment of the configuration, these were the messages:
FMC >> interface Ethernet1/7 FMC >> switchport trunk allowed vlan 5-6 fp1010 >> [info] : Failed to add a switch VLAN 5, a sub-interface E1/3.5 with same vlan-id exists. ERROR: Failed to add a switch VLAN 6, a sub-interface E1/3.6 with same vlan-id exists.
So, I've deleted the sub-interfaces from Ethernet1/3 and created Vlan interfaces (of course, changed also E1/3 to be a switchport in mode trunk for connecting to the rest of the network).
Now deployment works fine, switchport functionality looks ok, BUT:
- DHCP Relay Agent / DHCP Servers definition can't be configured for Vlan interfaces
- OSPF Interface can't be configured for Vlan interfaces
- RIP Passive Interfaces can't be configured for Vlan interfaces
- Multicast Routes or Multicast Boundary Filter can't be configured for Vlan interfaces
Only the physical (sub-) interfaces in routed mode appears in the list, typing the interface name is not working (like the trick with typing "diagnostic" in some older FMC versions)
The behavior is not consistent, as static routes can be configured with Vlan Interfaces :-)
So, as DHCP relay and OSPF are more important than getting 2 additional switchports with PoE, I'm rolling back to using sub-interfaces in routed mode. That was a fun lesson...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide