- Cisco Community
- Technology and Support
- Security
- Network Security
- Firepower 1120 transparent mode interface best practises?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2025 02:11 AM - edited 02-13-2025 02:13 AM
Hi,
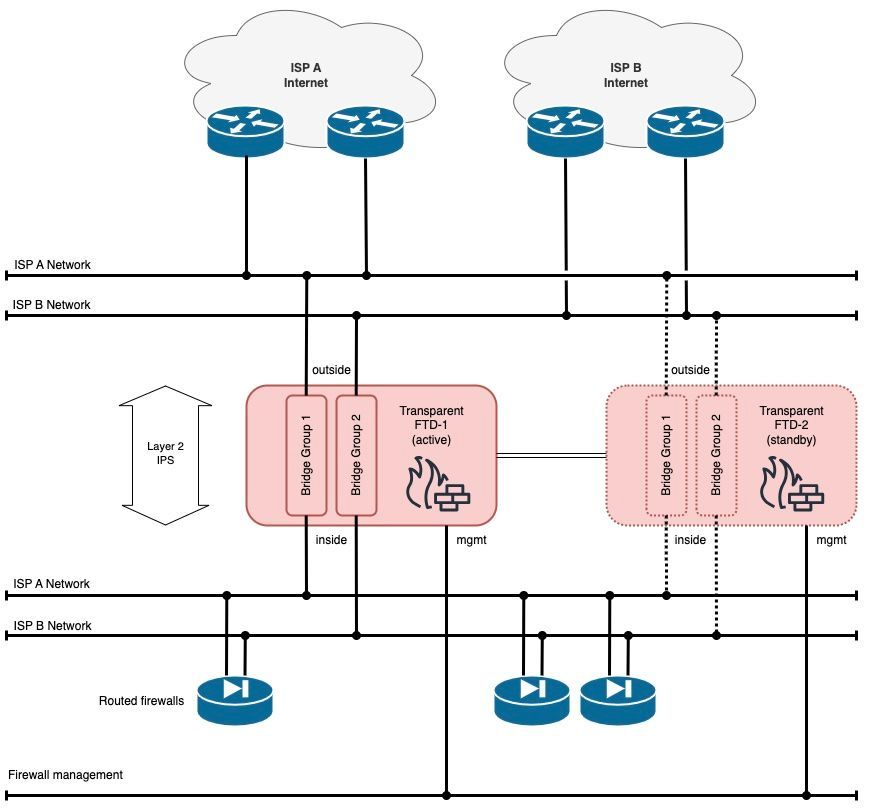
We have a pair of Firepower 1120 running FTD in transparent mode and active/standby HA. They should do IPS and threat protection for internet links with two separate ISP connections and different IP ranges and routing.
Separate bridge groups for each ISP.
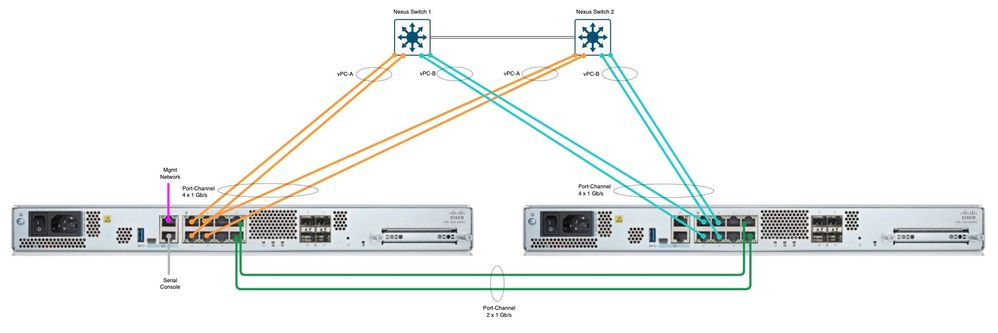
Uplink switches are 2 x Nexus C9348GC switches with vPC.
What's the best practise for interface assignments in such a setup for throughput and failover resiliency? The FTD admin guide is not very clear about this and the Youtube tutorials were all with virtual FTDs.
- Combined: 4 x 1 Gb/s port-channel with VLAN subinterfaces for both ISPs inside and outside
- Separated: 2 x 1 Gb/s port-channel for ISPs inside and another 2 x 1 Gb/s for outside, both with VLAN subinterfaces
- No port-channel and no VLAN subinterfaces at all, hardwired 1:1 connections
- It doesn't matter
Thanks in advance,
Bernd
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2025 05:34 AM
Will a 4 x 1 Gb/s port-channel across two Nexus C9348GC switches with vPC work as expected using VLAN trunking and separate VLANs for outside and inside? Each Nexus switch as two ISP routers (active/standby) connected. All the tutorials I have found on the internet use simple configurations like one VLAN per physical interface. Or are there some undocumented easter eggs to be expected?
Example configuration:
interface Ethernet1/17
description ftd-ips1 gi1
switchport mode trunk
spanning-tree port type edge trunk
spanning-tree guard root
mtu 9216
channel-group 17 mode active
no shutdown
interface Ethernet1/18
description ftd-zh-ips1 gi2
switchport mode trunk
spanning-tree port type edge trunk
spanning-tree guard root
mtu 9216
channel-group 17 mode active
no shutdown
interface port-channel17
description ftd-zh-ips1
switchport mode trunk
spanning-tree port type edge trunk
spanning-tree guard root
mtu 9216
vpc 17
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2025 05:34 AM
Will a 4 x 1 Gb/s port-channel across two Nexus C9348GC switches with vPC work as expected using VLAN trunking and separate VLANs for outside and inside? Each Nexus switch as two ISP routers (active/standby) connected. All the tutorials I have found on the internet use simple configurations like one VLAN per physical interface. Or are there some undocumented easter eggs to be expected?
Example configuration:
interface Ethernet1/17
description ftd-ips1 gi1
switchport mode trunk
spanning-tree port type edge trunk
spanning-tree guard root
mtu 9216
channel-group 17 mode active
no shutdown
interface Ethernet1/18
description ftd-zh-ips1 gi2
switchport mode trunk
spanning-tree port type edge trunk
spanning-tree guard root
mtu 9216
channel-group 17 mode active
no shutdown
interface port-channel17
description ftd-zh-ips1
switchport mode trunk
spanning-tree port type edge trunk
spanning-tree guard root
mtu 9216
vpc 17
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2025 05:32 AM
Separated: 2 x 1 Gb/s port-channel for ISPs inside and another 2 x 1 Gb/s for outside, both with VLAN subinterfaces
This configuration provides the best balance of throughput and failover resiliencyHere's why:
Separate bridge groups for each ISP allow for isolated traffic flows and easier management of different IP ranges and routing.Using port-channels increases bandwidth and provides link redundancy.VLAN subinterfaces allow for logical separation of traffic within each port-channel, accommodating multiple ISPs and inside/outside interfaces.
regarding your specific setup with Nexus C9348GC switches using vPC.
Yes, a 4 x 1 Gb/s port-channel across two Nexus C9348GC switches with vPC will work as expected using VLAN trunking and separate VLANs for outside and inside. This configuration is supported and provides high availability and load balancing.Your example configuration for the Nexus switches is correct and follows best practice/s.
interface Ethernet1/17
description ftd-ips1 gi1
switchport mode trunk
spanning-tree port type edge trunk
spanning-tree guard root
mtu 9216
channel-group 17 mode active
no shutdown
interface Ethernet1/18
description ftd-zh-ips1 gi2
switchport mode trunk
spanning-tree port type edge trunk
spanning-tree guard root
mtu 9216
channel-group 17 mode active
no shutdown
interface port-channel17
description ftd-zh-ips1
switchport mode trunk
spanning-tree port type edge trunk
spanning-tree guard root
mtu 9216
vpc 17The above configuration sets up a trunk port-channel with edge port and root guard features, which is appropriate/helpful for connecting to firewalls which you can take into account.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2025 05:35 AM
The best practice for interface assignments in a Firepower 1120 FTD setup with multiple ISPs is to use separated port-channels 2 x 1 Gb/s for ISPs inside and another 2 x 1 Gb/s for outside, both with VLAN subinterfaces. This configuration optimizes throughput and failover resiliency by segregating traffic, enhancing security zone management, and providing better control over routing and security policies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2025 11:45 PM - edited 04-03-2025 12:27 AM
Hm. When I enable the bridge interfaces then BPDUGuard sets it to errDisable. Firepower1120 has a 4 x 1 Gb/s port-channel and four VLAN subinterfaces. Pone pair VLAN-in/VLAN-out for each bridge group and ISP network range.
Spanning-tree interface options on Nexus switch:
nexus-1(config-if)# spanning-tree ?
bpdufilter Don't send or receive BPDUs on this interface
bpduguard Don't accept BPDUs on this interface
cost Change an interface's spanning tree port path cost
guard Change an interface's spanning tree guard mode
link-type Specify a link type for spanning tree tree protocol use
mst Multiple spanning tree
port Spanning tree port options
port-priority Change an interface's spanning tree port priority
vlan VLAN Switch Spanning TreesDisable guard root ???
nexus-1(config-if)# spanning-tree guard ?
loop Set guard mode to loop guard on interface
none Set guard mode to none
root Set guard mode to root guard on interfaceUse bpdufilter ???
nexus-1(config-if)# spanning-tree bpdufilter
disable enableDisable bpduguard ???
nexus-1(config-if)# spanning-tree bpduguard ?
disable Disable BPDU Guard for this interface
enable Enable BPDU Guard for this interfaceI'm a bit reluctant to play around with interface settings on production switch, although the transparent firewall is new and disconnected. Didn't find a best practises guide.
CheatGPT recommends to remove "spanning-tree guard root", but that's just a language model juggling words together that have thi highest probability and it has been so many times wrong in other situations and topics.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2025 12:38 AM
Interface configuration on Firepower.
Cheat GPT answers:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide